Errata exists for this version of the document.
This section includes a listing of the categories that a Profile can be grouped into, a list of named Profiles and the detailed listing of each Profile including directly defined ConformanceUnits and any sub Profiles that are included in the Profile.
Table 23 lists Profiles. The Profile table is ordered by Profile category and then alphabetically by the name of the Profile. The table includes a list of categories the Profile is associated with and a URI. The URI is used to uniquely identify a Profile. The URI shall be able to be used to access the information provided in this document with regard to the given Profile in an on-line display.
An application (Client or Server) shall implement all of the ConformanceUnits in a Profile in order to be compliant with the Profile. Some Profiles contain optional ConformanceUnits. An optional ConformanceUnit means that an application has the option to not support the ConformanceUnit. However, if supported, the application shall pass all tests associated with the ConformanceUnit. For example, some ConformanceUnits require specific information model items to be available. They are, therefore, listed as optional in order to allow for the information model items to be omitted. If a Server desires to be listed as supporting the optional ConformanceUnit then it shall include any required information model items in the configuration provided for certification testing. The test result that is generated by the certification testing lists all optional ConformanceUnits and whether they are supported or not by the tested UA application. Some ConformanceUnits also include lists of supported DataTypes or optional Subtypes, the list are handled in the same manner as optional ConformanceUnits. All reporting requirements for optional ConformanceUnits also apply to these lists of supported DataTypes or Subtypes.
|
Profile |
Related Category |
URI |
|
Core Server Facet |
Server |
|
|
Core 2017 Server Facet |
Server |
|
|
Sessionless Server Facet |
http://opcfoundation.org/UA-Profile/Server/SessionLess |
|
|
Reverse Connect Server Facet |
Server |
|
|
Base Server Behaviour Facet |
Server |
|
|
Request State Change Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/RequestStateChange |
|
Subnet Discovery Server Facet |
Server |
|
|
Global Certificate Management Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/GlobalCertificateManagement |
|
Authorization Service Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/AuthorizationServiceConfiguration |
|
KeyCredential Service Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/KeyCredentialManagement |
|
Attribute WriteMask Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/AttributeWriteMask |
|
File Access Server Facet |
Server |
|
|
Documentation Server Facet |
Server |
|
|
Embedded DataChange Subscription Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/EmbeddedDataChangeSubscription |
|
Standard DataChange Subscription Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/StandardDataChangeSubscription |
|
Standard DataChange Subscription 2017 Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/StandardDataChangeSubscription2017 |
|
Enhanced DataChange Subscription Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/EnhancedDataChangeSubscription |
|
Enhanced DataChange Subscription 2017 Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/EnhancedDataChangeSubscription2017 |
|
Durable Subscription Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/DurableSubscription |
|
Data Access Server Facet |
Server |
|
|
ComplexType Server Facet |
Server |
|
|
ComplexType 2017 Server Facet |
Server |
|
|
Standard Event Subscription Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/StandardEventSubscription |
|
Address Space Notifier Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/AddressSpaceNotifier |
|
A & C Base Condition Server Facet |
Server |
|
|
A & C Refresh2 Server Facet |
Server |
|
|
A & C Address Space Instance Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/ACAddressSpaceInstance |
|
A & C Enable Server Facet |
Server |
|
|
A & C AlarmMetrics Server Facet |
Server |
|
|
A & C Alarm Server Facet |
Server |
|
|
A & C Acknowledgeable Alarm Server Facet |
Server |
|
|
A & C Exclusive Alarming Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/ACExclusiveAlarming |
|
A & C Non-Exclusive Alarming Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/ACNon-ExclusiveAlarming |
|
A & C Previous Instances Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/ACPreviousInstances |
|
A & C Dialog Server Facet |
Server |
|
|
A & C CertificateExpiration Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/ACCertificateExpiration |
|
A & E Wrapper Facet |
Server |
|
|
Method Server Facet |
Server |
|
|
Auditing Server Facet |
Server |
|
|
Node Management Server Facet |
Server |
|
|
User Role Base Server Facet |
Server |
|
|
User Role Management Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/UserRoleManagement |
|
State Machine Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/StateMachine |
|
Client Redundancy Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/ClientRedundancy |
|
Redundancy Transparent Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/TransparentRedundancy |
|
Redundancy Visible Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/VisibleRedundancy |
|
Historical Raw Data Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalRawData |
|
Historical Aggregate Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/AggregateHistorical |
|
Historical Data AtTime Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalDataAtTime |
|
Historical Access Modified Data Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalModifiedData |
|
Historical Annotation Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalAnnotation |
|
Historical Data Insert Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalDataInsert
|
|
Historical Data Update Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalDataUpdate |
|
Historical Data Replace Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalDataReplace |
|
Historical Data Delete Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalDataDelete |
|
Historical Access Structured Data Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalStructuredData |
|
Base Historical Event Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/BaseHistoricalEvent |
|
Historical Event Update Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalEventUpdate |
|
Historical Event Replace Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalEventReplace |
|
Historical Event Insert Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalEventInsert |
|
Historical Event Delete Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/HistoricalEventDelete |
|
Aggregate Subscription Server Facet |
Server |
http://opcfoundation.org/UA-Profile/Server/AggregateSubscription |
|
Nano Embedded Device Server Profile |
Server |
http://opcfoundation.org/UA-Profile/Server/NanoEmbeddedDevice |
|
Nano Embedded Device 2017 Server Profile |
Server |
http://opcfoundation.org/UA-Profile/Server/NanoEmbeddedDevice2017 |
|
Micro Embedded Device Server Profile |
Server |
http://opcfoundation.org/UA-Profile/Server/MicroEmbeddedDevice |
|
Micro Embedded Device 2017 Server Profile |
Server |
http://opcfoundation.org/UA-Profile/Server/MicroEmbeddedDevice2017 |
|
Embedded UA Server Profile |
Server |
|
|
Embedded 2017 UA Server Profile |
Server |
|
|
Standard UA Server Profile |
Server |
|
|
Standard 2017 UA Server Profile |
Server |
|
|
Core Client Facet |
||
|
Core 2017 Client Facet |
||
|
Sessionless Client Facet |
http://opcfoundation.org/UA-Profile/Client/SessionLess |
|
|
Reverse Connect Client Facet |
Client |
|
|
Base Client Behaviour Facet |
Client |
|
|
Discovery Client Facet |
Client |
|
|
Subnet Discovery Client Facet |
Client |
|
|
Global Discovery Client Facet |
Client |
|
|
Global Certificate Management Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/GlobalCertificateManagement |
|
KeyCredential Service Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/KeyCredentialManagement |
|
Access Token Request Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/AccessTokenRequest |
|
AddressSpace Lookup Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/AddressSpaceLookup |
|
Request State Change Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/RequestStateChange |
|
File Access Client Facet |
Client |
|
|
Entry Level Support 2015 Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/EntryLevelSupport2015 |
|
Multi-Server Client Connection Facet |
Client |
|
|
Documentation – Client |
Client |
|
|
Attribute Read Client Facet |
Client |
|
|
Attribute Write Client Facet |
Client |
|
|
DataChange Subscriber Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/DataChangeSubscriber |
|
Durable Subscription Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/DurableSubscription |
|
DataAccess Client Facet |
Client |
|
|
Event Subscriber Client Facet |
Client |
|
|
Base Event Processing Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/BaseEventProcessing |
|
Notifier and Source Hierarchy Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/NotifierAndSourceHierarchy |
|
A & C Base Condition Client Facet |
Client |
|
|
A & C Refresh2 Client Facet |
Client |
|
|
A & C Address Space Instance Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/ACAddressSpaceInstance |
|
A & C Enable Client Facet |
Client |
|
|
A & C AlarmMetrics Client Facet |
Client |
|
|
A & C Alarm Client Facet |
Client |
|
|
A & C Exclusive Alarming Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/ACExclusiveAlarming |
|
A & C Non-Exclusive Alarming Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/ACNon-ExclusiveAlarming |
|
A & C Previous Instances Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/ACPreviousInstances |
|
A & C Dialog Client Facet |
Client |
|
|
A & C CertificateExpiration Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/ACCertificateExpiration |
|
A & E Proxy Facet |
Client |
|
|
Method Client Facet |
Client |
|
|
Auditing Client Facet |
Client |
|
|
Node Management Client Facet |
Client |
|
|
Advanced Type Programming Client Facet |
Client |
|
|
User Role Management Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/UserRoleManagement |
|
State Machine Client Facet |
Client |
|
|
Diagnostic Client Facet |
Client |
|
|
Redundant Client Facet |
Client |
|
|
Redundancy Switch Client Facet |
Client |
|
|
Historical Access Client Facet |
Client |
|
|
Historical Data AtTime Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalAccessAtTime |
|
Historical Aggregate Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalAccessAggregate |
|
Historical Annotation Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalAnnotation |
|
Historical Access Modified Data Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalAccessModifiedData |
|
Historical Data Insert Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalInsertData
|
|
Historical Data Update Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalUpdateData |
|
Historical Data Replace Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalReplaceData |
|
Historical Data Delete Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalDeleteData |
|
Historical Access Client Server Timestamp Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalServerTimeStamp |
|
Historical Structured Data Access Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalAccessStructuredData |
|
Historical Structured Data AtTime Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalAtTimeStructuredData |
|
Historical Structured Data Modified Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalModifiedStructuredData |
|
Historical Structured Data Insert Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalInsertStructuredData |
|
Historical Structured Data Update Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalUpdateStructuredData |
|
Historical Structured Data Replace Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalReplaceStructuredData |
|
Historical Structured Data Delete Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalDeleteStructuredData |
|
Historical Events Client Facet |
Client |
|
|
Historical Event Insert Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalInsertEvents |
|
Historical Event Update Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalUpdateEvents |
|
Historical Event Replace Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalReplaceEvents |
|
Historical Event Delete Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/HistoricalDeleteEvents |
|
Aggregate Subscriber Client Facet |
Client |
http://opcfoundation.org/UA-Profile/Client/AggregateSubscriber |
|
Standard UA Client Profile |
Client |
|
|
Standard UA Client 2017 Profile |
Client |
|
|
UA-TCP UA-SC UA-Binary |
Transport |
http://opcfoundation.org/UA-Profile/Transport/uatcp-uasc-uabinary |
|
HTTPS UA-Binary |
Transport |
http://opcfoundation.org/UA-Profile/Transport/https-uabinary
|
|
HTTPS UA-XML |
Transport |
http://opcfoundation.org/UA-Profile/Transport/https-uasoapxml |
|
HTTPS UA-JSON |
Transport |
|
|
WSS UA-SC UA-Binary |
Transport |
http://opcfoundation.org/UA-Profile/Transport/wss-uasc-uabinary |
|
WSS UA-JSON |
Transport |
|
|
Security User Access Control Full |
Security, Server |
|
|
Security User Access Control Base |
Security, Server |
|
|
Security Time Synchronization |
Security |
|
|
Best Practice – Audit Events |
Security, Server |
http://opcfoundation.org/UA-Profile/Security/BestPracticeAuditEvents |
|
Best Practice – Alarm Handling |
Security, Server |
http://opcfoundation.org/UA-Profile/Security/BestPracticeAlarmHandling |
|
Best Practice – Random Numbers |
Security |
http://opcfoundation.org/UA-Profile/Security/BestPracticeRandomNumbers |
|
Best Practice – Timeouts |
Security |
http://opcfoundation.org/UA-Profile/Security/BestPracticeTimeouts |
|
Best Practice – Administrative Access |
Security |
http://opcfoundation.org/UA-Profile/Security/BestPracticeAdministrativeAccess |
|
Best Practice – Strict Message Handling |
Security, Server |
http://opcfoundation.org/UA-Profile/Security/BestPracticeStrictMessage |
|
Best Practice – Audit Events Client |
Client, Security |
http://opcfoundation.org/UA-Profile/Security/BestPracticeAuditEventsClient |
|
TransportSecurity – TLS 1.2 |
Security |
http://opcfoundation.org/UA-Profile/TransportSecurity/TLS-1-2 |
|
TransportSecurity – TLS 1.2 with PFS |
Security |
http://opcfoundation.org/UA-Profile/TransportSecurity/TLS-1-2-PFS |
|
SecurityPolicy – None |
Security |
|
|
SecurityPolicy [A] - Aes128-Sha256-RsaOaep |
Security |
http://opcfoundation.org/UA/SecurityPolicy#Aes128_Sha256_RsaOaep |
|
SecurityPolicy [B] – Basic256Sha256 |
Security |
|
|
SecurityPolicy - Aes256-Sha256-RsaPss |
Security |
http://opcfoundation.org/UA/SecurityPolicy#Aes256_Sha256_RsaPss |
|
User Token – Anonymous Facet |
Security |
http://opcfoundation.org/UA-Profile/Security/UserToken/Anonymous |
|
User Token – User Name Password Server Facet |
Security, Server |
http://opcfoundation.org/UA-Profile/Security/UserToken/Server/UserNamePassword |
|
User Token – X509 Certificate Server Facet |
Security, Server |
http://opcfoundation.org/UA-Profile/Security/UserToken/Server/X509Certificate |
|
User Token – Issued Token Server Facet |
Security, Server |
http://opcfoundation.org/UA-Profile/Security/UserToken/Server/IssuedToken |
|
User Token – Issued Token Windows Server Facet |
Security, Server |
http://opcfoundation.org/UA-Profile/Security/UserToken/Server/IssuedTokenWindows |
|
User Token – JWT Server Facet |
Security |
http://opcfoundation.org/UA-Profile/Security/UserToken/Server/JsonWebToken |
|
User Token – User Name Password Client Facet |
Client, Security |
http://opcfoundation.org/UA-Profile/Security/UserToken/Client/UserNamePassword |
|
User Token – X509 Certificate Client Facet |
Client, Security |
http://opcfoundation.org/UA-Profile/Security/UserToken/Client/X509Certificate |
|
User Token – Issued Token Client Facet |
Client, Security |
http://opcfoundation.org/UA-Profile/Security/UserToken/Client/IssuedToken |
|
User Token – Issued Token Windows Client Facet |
Client, Security |
http://opcfoundation.org/UA-Profile/Security/UserToken/Client/IssuedTokenWindows |
|
User Token – JWT Client Facet |
Security |
http://opcfoundation.org/UA-Profile/Security/UserToken/Client/JsonWebToken |
|
Global Discovery Server Profile |
Global Directory Service, Server |
|
|
Global Discovery Server 2017 Profile |
Global Directory Service, Server |
http://opcfoundation.org/UA-Profile/Server/GlobalDiscovery2017 |
|
Global Discovery and Certificate Management Server |
Global Directory Service, Server |
http://opcfoundation.org/UA-Profile/Server/GlobalDiscoveryAndCertificateManagement |
|
Global Discovery and Certificate Mgmt 2017 Server |
Global Directory Service, Server |
http://opcfoundation.org/UA-Profile/Server/GlobalDiscoveryAndCertificateManagement2017 |
|
Global Certificate Management Client Profile |
Client, Global Directory Service |
http://opcfoundation.org/UA-Profile/Client/GlobalCertificateManagement |
|
Global Certificate Management Client 2017 Profile |
Client, Global Directory Service |
http://opcfoundation.org/UA-Profile/Client/GlobalCertificateManagement2017 |
|
Global Service Authorization Request Server Facet |
Global Directory Service |
http://opcfoundation.org/UA-Profile/Server/GlobalServiceAuthorization |
|
Global Service KeyCredential Pull Facet |
Global Directory Service |
http://opcfoundation.org/UA-Profile/Server/GlobalServiceKeyCredentials |
|
Global Service KeyCredential Push Facet |
Global Directory Service |
http://opcfoundation.org/UA-Profile/Client/GlobalServiceKeyCredentials |
The contents of each of the listed Profiles will be described in a tabular form in a separate section. Each table may contain references to additional Profiles and or ConformanceUnits. If a Profile is referenced it means that it is completely included. The ConformanceUnits are referenced using their name and conformance group. For the details of the ConformanceUnit the reader should examine the ConformanceUnit details in the appropriate conformance group section.
Profiles have the following naming conventions:
- Profiles intended for OPC UA Servers contain the term Server in their titles,
- Profiles intended for OPC UA Clients contain the term Client in their titles
- The term Facet in the title of a Profile indicates that this Profile is expected to be part of another larger Profile or concerns a specific aspect of OPC UA. Profiles with the term Facet in their title are expected to be combined with other Profiles to define the complete functionality of an OPC UA Server, Client, Publisher, or Subscriber.
Versioning of Profile is accomplished with a naming convention. Whenever a profile is revised, the year of the new revision is added to the name. Example:
|
Version 1 |
Core Server Facet |
|
Version 2 |
Core 2017 Server Facet |
A vendor that is developing a UA application, whether it is a Server application or a Client application, shall review the list of available Profiles. From this list the vendor shall select the Profiles that include the functionality required by the application. Typically this will be multiple Profiles. Conformance to a single Profile may not yield a complete application. In most cases multiple Profiles are needed to yield a useful application. All Servers and Clients shall support at least a core Profile (Core Server Facet or Core Client Facet) and at least one Transport Profile
For example an HMI Client application may choose to support the “Core Client Facet”, the “UA-TCP UA-SC UA-Binary” Profile, the “Data Access Client Facet”, the “DataChange Subscriber Client Facet” and the “Attribute Write Client Facet”. If the Client is to be TestLab tested then it would also support “Base Client Behaviour” Profile. This list of Profiles would allow the Client to communicate with an OPC UA Server using UA-TCP/UA Security/UA binary. It would be able to subscribe for data, write to data and would support the DA data model. It would also follow the best practice guideline for behaviour. Figure 2 illustrates the Profile hierarchy that this application may contain: This figure is only an illustration and the represented Profiles may change.
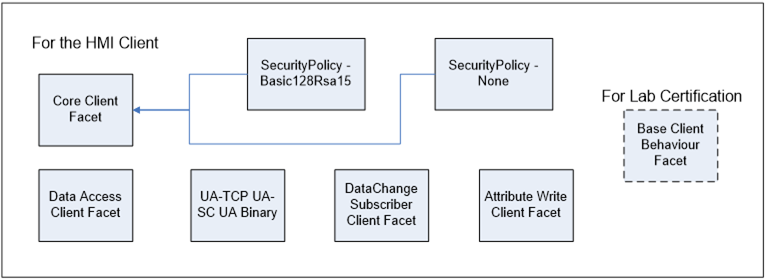
All Clients should take into account the types of Servers and Server Profiles that they are targeted to support. Some Servers might not support Subscriptions and Clients should be able to fall back to Read Services.
A special case is a generic Client that is designed to communicate with a large number of Servers and therefore able to perform a broad range of functionality. ”Standard UA Client Profile” has been defined for this kind of Clients.
Many Clients, however, will be specialized and do not need all of the functionality in the ”Standard UA Client Profile” and thus would only support the limited set of functionality they require. A trend Client, for example, would only need functionality to subscribe to or read data.
Another example is an embedded device OPC UA Server application that may choose to support “Embedded UA Server” Profile and the “DataAccess Server Facet” Profile. This device would be a resource constrained device that would support UA-TCP, UA-Security, UA Binary encoding, data subscriptions and the DA data model. It may not support the optional attribute write. Figure 3 illustrates the hierarchy that this application may contain: This figure is just an illustration and the represented Profiles may change.
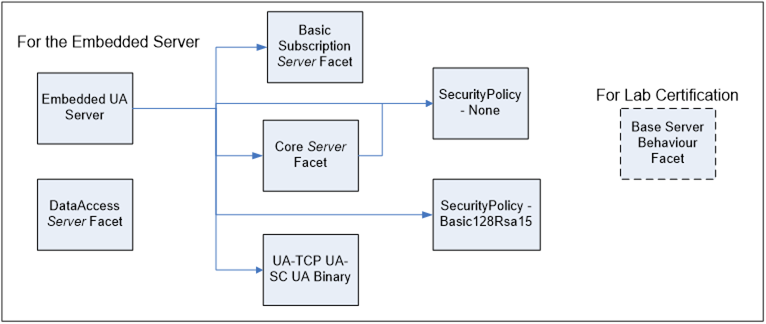
Figure 3 – Embedded Server sample
Another simple system Server application may choose to support: “Standard UA Server” Profile and the “DataAccess Server Facet” Profile. If the Server is to be lab tested then it would also support “Base Server Behaviour” Profile. This device would be a mid-level OPC UA Server that would support all that the embedded Server in the previous example supported and it would add support for an enhance level of the subscription service and support for writes. Figure 4 illustrates the hierarchy that this application may contain: This figure is just an illustration and the represented Profile may change.
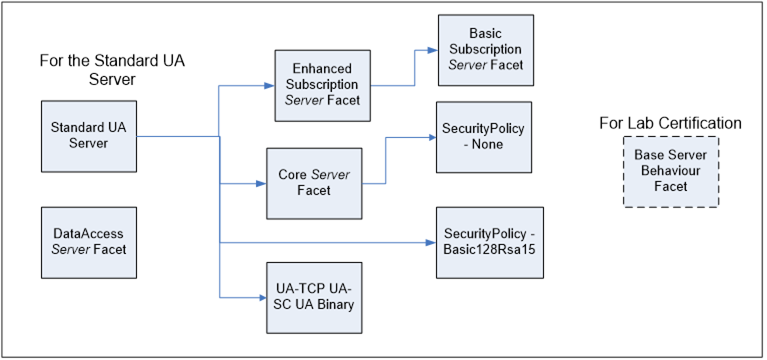
Figure 4 – Standard UA Server sample
If the example HMI Client were to connect to either of the example Servers, it may have to adjust its behavior based on the Profile reported by the respective Servers. If the HMI Client were communicating with the embedded device it would not be able to perform any write operations. It may also have to limit the number of subscriptions or sessions based on the performance limits of the Server. If the HMI Client is connected to the Standard Server it would be able to open additional windows, have higher limits on performance related items and it would be able to allow writes.
The following sections describe Profiles in a tabular format.
Each table contains three columns. The first column is a description of the conformance group that the ConformanceUnit is part of. This allows the reader to easily find the ConformanceUnit. This column may also state “Profile” in which case the listed item is not a ConformanceUnit, but an included P rofile. The second column is a brief description of the ConformanceUnit or included Profile. The last column indicates if the ConformanceUnit is optional or required.
Table 24 describes the details of the Core Server Facet. This Facet defines the core functionality required for any UA Server implementation. The core functionality includes the ability to discover endpoints, establish secure communication channels, create Sessions, browse the AddressSpace and read and/or write to Attributes of Nodes. The key requirements are: support for a single Session, support for the Server and Server Capabilities Object, all mandatory Attributes for Nodes in the AddressSpace, and authentication with UserName and Password. This Facet has been extended with additional Base Information ConformanceUnits. They are optional to provide backward compatibility. In the future the ConformanceUnit “Base Info Server Capabilities” will become required, and so it is highly recommended that all Servers support it. For broad applicability, it is recommended that Servers support multiple transport and security Profiles.
|
Group |
Conformance Unit / Profile Title |
Optional |
|
SecurityPolicy – None |
False |
|
|
User Token – User Name Password Server Facet |
False |
|
|
Address Space Model |
Address Space Base |
False |
|
Attribute Read |
False |
|
|
Attribute Write Index |
True |
|
|
Attribute Write Values |
True |
|
|
Base Information |
Base Info Core Structure |
False |
|
Base Information |
Base Info OptionSet |
True |
|
Base Information |
Base Info Placeholder Modelling Rules |
True |
|
Base Information |
Base Info Server Capabilities |
True |
|
Base Information |
Base Info ValueAsText |
True |
|
False |
||
|
Discovery Get Endpoints |
False |
|
|
Security |
Security – No Application Authentication |
True |
|
Security |
Security Administration |
True |
|
Session Base |
False |
|
|
False |
||
|
Session Minimum 1 |
False |
|
|
View Services |
View Basic |
False |
|
View Services |
View Minimum Continuation Point 01 |
False |
|
View Services |
View RegisterNodes |
False |
|
View Services |
View TranslateBrowsePath |
False |
Table 25 describes the details of the Core 2017 Server Facet. This Facet defines the core functionality required for any UA Server implementation. The core functionality includes the ability to discover endpoints, establish secure communication channels, create Sessions, browse the AddressSpace and read and/or write to Attributes of Nodes. The key requirements are: support for a single Session, support for the Server and Server Capabilities Object, all mandatory Attributes for Nodes in the AddressSpace, and authentication with UserName and Password. For broad applicability, it is recommended that Servers support multiple transport and security Profiles. This Facet supersedes the “Core Server Facet”.
Table 25 – Core 2017 Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
SecurityPolicy – None |
False |
|
|
User Token – User Name Password Server Facet |
False |
|
|
Address Space Model |
Address Space Atomicity |
False |
|
Address Space Model |
Address Space Base |
False |
|
Address Space Model |
Address Space Full Array Only |
False |
|
Attribute Read |
False |
|
|
Attribute Write Index |
True |
|
|
Attribute Write Values |
True |
|
|
Base Information |
Base Info Core Structure |
False |
|
Base Information |
Base Info Estimated Return Time |
True |
|
Base Information |
Base Info OptionSet |
True |
|
Base Information |
Base Info Placeholder Modelling Rules |
True |
|
Base Information |
Base Info Selection List |
True |
|
Base Information |
Base Info Server Capabilities |
True |
|
Base Information |
Base Info ValueAsText |
True |
|
False |
||
|
Discovery Get Endpoints |
False |
|
|
Security |
Security Administration |
True |
|
Security |
Security Role Server Authorization |
True |
|
Session Base |
False |
|
|
False |
||
|
Session Minimum 1 |
False |
|
|
View Services |
View Basic |
False |
|
View Services |
View Minimum Continuation Point 01 |
False |
|
View Services |
View RegisterNodes |
False |
|
View Services |
View TranslateBrowsePath |
False |
Table 26 describes the details of the Sessionless Server Facet. Defines the use of Sessionless Service invocation in a Server.
Table 26 – Sessionless Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Discovery Get Endpoints SessionLess |
False |
|
|
Session Sessionless Invocation |
False |
Table 27 describes the details of the Reverse Connect Server Facet. This Facet defines support of reverse connectivity in a Server. Usually, a connection is opened by the Client before starting the UA-specific handshake. This will fail, however, when Servers are behind firewalls with no open ports to connect to. In the reverse connectivity scenario, the Server opens the connection and starts with a ReverseHello message requesting that the Client establish a Secure Channel using this connection.
Table 27 – Reverse Connect Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Protocol and Encoding |
Protocol Reverse Connect Server |
False |
Table 28 describes the details of the Base Server Behaviour Facet. This Facet defines best practices for the configuration and management of Servers when they are deployed in a production environment. It provides the ability to enable or disable certain protocols and to configure the Discovery Server and specify where this Server shall be registered.
Table 28 – Base Server Behaviour Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Discovery Configuration |
False |
|
|
Protocol and Encoding |
Protocol Configuration |
False |
|
Security |
Security Administration |
False |
|
Security |
Security Administration – XML Schema |
False |
|
Security |
Security Certificate Administration |
False |
Table 29 describes the details of the Request State Change Server Facet. This Facet specifies the support of the RequestServerStateChange Method.
Table 29 – Request State Change Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Base Information |
Base Info RequestServerStateChange Method |
False |
Table 30 describes the details of the Subnet Discovery Server Facet. Support of this Facet enables discovery of the Server on a subnet using mDNS. This functionality is only applicable when Servers do not register with an LDS.
Table 30 – Subnet Discovery Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
Table 31 describes the details of the Global Certificate Management Server Facet. This Facet defines the capability to interact with a Global Certificate Management Server to obtain an initial or renewed Certificate and Trust Lists.
Table 31 – Global Certificate Management Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Push Model for Global Certificate and TrustList Management |
False |
Table 32 describes the details of the Authorization Service Server Facet. This Facet defines the support for configuring the necessary information to validate access tokens when presented by a Client during session establishment. Access Tokens are issued by Authorization Services.
Table 32 – Authorization Service Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Authorization Service Configuration Server |
False |
Table 33 describes the details of the KeyCredential Service Server Facet. This Facet defines the capability to interact with a KeyCredential Service to obtain KeyCredentials. For example KeyCredentials are needed to access an Authorization Service or a Broker. The KeyCredential Service is typically part of a system-wide tool, like a GDS that also manages Applications, Access Tokens, and Certificates.
Table 33 – KeyCredential Service Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Push Model for KeyCredential Service |
False |
Table 34 describes the details of the Attribute WriteMask Server Facet. This Facet defines the capability to update characteristics of individual Nodes in the AddressSpace by allowing writing to Node Attributes. It requires support for authenticating user access as well as providing information related to access rights in the AddressSpace and actually restricting the access rights as described.
Table 34 – Attribute WriteMask Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security User Access Control Base |
False |
|
|
Address Space Model |
Address Space UserWriteMask |
False |
|
Address Space Model |
Address Space UserWriteMask Multilevel |
True |
|
Address Space Model |
Address Space WriteMask |
False |
Table 35 describes the details of the File Access Server Facet. This Facet specifies the support of exposing File information via the defined FileType. This includes reading of file as well as optionally writing of file data.
Table 35 – File Access Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Base Information |
Base Info FileType Base |
False |
|
Base Information |
Base Info FileType Write |
True |
Table 36 describes the details of the Documentation Server Facet. This Facet defines a list of user documentation that a server application should provide.
Table 36 – Documentation Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Miscellaneous |
Documentation – Installation |
False |
|
Miscellaneous |
Documentation – Multiple Languages |
True |
|
Miscellaneous |
Documentation – On-line |
True |
|
Miscellaneous |
Documentation – Supported Profiles |
True |
|
Miscellaneous |
Documentation – Trouble Shooting Guide |
True |
|
Miscellaneous |
Documentation – Users Guide |
False |
Table 37 describes the details of the Embedded DataChange Subscription Server Facet. This Facet specifies the minimum level of support for data change notifications within subscriptions. It includes limits which minimize memory and processing overhead required to implement the Facet. This Facet includes functionality to create, modify and delete Subscriptions and to add, modify and remove Monitored Items. As a minimum for each Session, Servers shall support one Subscription with up to two items. In addition, support for two parallel Publish requests is required. This Facet is geared for a platform such as the one provided by the Micro Embedded Device Server Profile in which memory is limited and needs to be managed.
Table 37 – Embedded DataChange Subscription Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Monitored Item Services |
Monitor Basic |
False |
|
Monitored Item Services |
Monitor Items 2 |
False |
|
Monitored Item Services |
Monitor QueueSize_1 |
False |
|
Monitored Item Services |
Monitor Value Change |
False |
|
Subscription Basic |
False |
|
|
Subscription Minimum 1 |
False |
|
|
Subscription Publish Discard Policy |
False |
|
|
Subscription Publish Min 02 |
False |
Table 38 describes the details of the Standard DataChange Subscription Server Facet. This Facet specifies the standard support of subscribing to data changes. This Facet extends features and limits defined by the Embedded Data Change Subscription Facet. As a minimum, Servers shall support 2 Subscriptions with at least 100 items for at least half of the required Sessions. The 100 items shall be supported for at least half of the required Subscriptions. Queuing with up to two queued entries is required. Support of five parallel Publish requests per Session is required. This Facet also requires the support of the triggering service. This Facet has been updated to include optional ConformanceUnits to allow for backward compatibility. These optional ConformanceUnits are highly recommended, in that in a future release they will be made mandatory.
Table 38 – Standard DataChange Subscription Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Embedded DataChange Subscription Server Facet |
False |
|
|
Base Information |
Base Info GetMonitoredItems Method |
True |
|
Method Call |
True |
|
|
Monitored Item Services |
Monitor Items 10 |
False |
|
Monitored Item Services |
Monitor Items 100 |
False |
|
Monitored Item Services |
Monitor MinQueueSize_02 |
False |
|
Monitored Item Services |
Monitor Triggering |
False |
|
Monitored Item Services |
Monitored Items Deadband Filter |
False |
|
Subscription Minimum 02 |
False |
|
|
Subscription Publish Min 05 |
False |
Table 39 describes the details of the Standard DataChange Subscription 2017 Server Facet. This Facet specifies the standard support of subscribing to data changes and extends features and limits defined by the Embedded Data Change Subscription Facet. See ConformanceUnits for these limits. Note that the Method Call Service is only required for the Methods defined in this Facet. This Facet supersedes the “Standard DataChange Subscription Server Facet”.
Table 39 – Standard DataChange Subscription 2017 Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Embedded DataChange Subscription Server Facet |
False |
|
|
Base Information |
Base Info GetMonitoredItems Method |
False |
|
Base Information |
Base Info ResendData Method |
False |
|
Method Call |
False |
|
|
Monitored Item Services |
Monitor Items 10 |
False |
|
Monitored Item Services |
Monitor Items 100 |
False |
|
Monitored Item Services |
Monitor MinQueueSize_02 |
False |
|
Monitored Item Services |
Monitor Triggering |
False |
|
Monitored Item Services |
Monitored Items Deadband Filter |
False |
|
Subscription Minimum 02 |
False |
|
|
Subscription Publish Min 05 |
False |
Table 40 describes the details of the Enhanced DataChange Subscription Server Facet. This Facet specifies an enhanced support of subscribing to data changes. It is part of the Standard UA Server Profile. This Facet increases the limits defined by the Standard Data Change Subscription Facet.
Table 40 – Enhanced DataChange Subscription Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Standard DataChange Subscription Server Facet |
False |
|
|
Monitored Item Services |
Monitor Items 500 |
False |
|
Monitored Item Services |
Monitor MinQueueSize_05 |
False |
|
Subscription Minimum 05 |
False |
|
|
Subscription Publish Min 10 |
False |
Table 41 describes the details of the Enhanced DataChange Subscription 2017 Server Facet. This Facet specifies an enhanced support of subscribing to data changes. It is part of the Standard UA Server 2017 Profile. This Facet increases the limits defined by the Standard Data Change Subscription 2017 Server Facet.
Table 41 – Enhanced DataChange Subscription 2017 Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Standard DataChange Subscription 2017 Server Facet |
False |
|
|
Monitored Item Services |
Monitor Items 500 |
False |
|
Monitored Item Services |
Monitor MinQueueSize_05 |
False |
|
Subscription Minimum 05 |
False |
|
|
Subscription Publish Min 10 |
False |
Table 42 describes the details of the Durable Subscription Server Facet. This Facet specifies support of durable storage of data and events even when Clients are disconnected. This Facet implies support of any of the DataChange or Event Subscription Facets.
Table 42 – Durable Subscription Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Subscription Durable |
False |
|
|
Subscription Durable StorageLevel High |
True |
|
|
Subscription Durable StorageLevel Medium |
True |
|
|
Subscription Durable StorageLevel Small |
True |
Table 43 describes the details of the Data Access Server Facet. This Facet specifies the support for an Information Model used to provide industrial automation data. This model defines standard structures for analog and discrete data items and their quality of service. This Facet extends the Core Server Facet which includes support of the basic AddressSpace behaviour.
Table 43 – Data Access Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Data Access |
Data Access AnalogItems |
True |
|
Data Access |
Data Access ArrayItemType |
True |
|
Data Access |
Data Access Complex Number |
True |
|
Data Access |
Data Access DataItems |
False |
|
Data Access |
Data Access DoubleComplex Number |
True |
|
Data Access |
Data Access MultiState |
True |
|
Data Access |
Data Access MultiStateValueDiscrete |
True |
|
Data Access |
Data Access PercentDeadband |
True |
|
Data Access |
Data Access Semantic Changes |
True |
|
Data Access |
Data Access TwoState |
True |
Table 44 describes the details of the ComplexType Server Facet. This Facet extends the Core Server Facet to include Variables with Complex Data, i.e. data that are composed of multiple elements such as a structure and where the individual elements are exposed as component variables. Support of this Facet requires the implementation of structured DataTypes and Variables that make use of these DataTypes. The Read, Write and Subscriptions service set shall support the encoding and decoding of these structured DataTypes. As an option the Server can also support alternate encodings, such as an XML encoding when the binary protocol is currently used and vice-versa.
Table 44 – ComplexType Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Complex Data Dictionary |
False |
|
Attribute Alternate Encoding |
True |
|
|
Attribute Read Complex |
False |
|
|
Attribute Write Complex |
False |
|
|
Monitored Item Services |
Monitor Alternate Encoding |
True |
Table 45 describes the details of the ComplexType 2017 Server Facet. This Facet extends the Core Server Facet to include Variables with structured data, i.e. data that are composed of multiple elements such as a structure and where the individual elements are exposed as component variables. Support of this Facet requires the implementation of structured DataTypes and Variables that make use of these DataTypes. The Read, Write and Subscriptions service set shall support the encoding and decoding of these structured DataTypes. As an option the Server can also support alternate encodings, such as an XML encoding when the binary protocol is currently used and vice-versa.
Table 45 – ComplexType 2017 Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space DataTypeDefinition Attribute |
False |
|
Attribute Alternate Encoding |
True |
|
|
Attribute Read Complex |
False |
|
|
Attribute Write Complex |
False |
|
|
Monitored Item Services |
Monitor Alternate Encoding |
True |
|
Monitored Item Services |
Monitor Complex Value |
True |
Table 46 describes the details of the Standard Event Subscription Server Facet. This Facet specifies the standard support for subscribing to events and is intended to supplement any of the FullFeatured Profiles. Support of this Facet requires the implementation of Event Types representing the Events that the Server can report and their specific fields. It also requires at least the Server Object to have the EventNotifier Attribute set. It includes the Services to Create, Modify and Delete Subscriptions and to Add, Modify and Remove Monitored Items for Object Nodes with an “EventNotifier Attribute”. Creating a monitoring item may include a filter that includes SimpleAttribute FilterOperands and a select list of Operators. The operators include: Equals, IsNull, GreaterThan, LessThan, GreaterThanOrEqual, LessThanOrEqual, Like, Not, Between, InList, And, Or, Cast, BitwiseAnd, BitwiseOr and TypeOf. Support of more complex filters is optional. This Facet has been updated to include several optional Base Information ConformanceUnits. These ConformanceUnits are optional to allow for backward compatibility, in the future these optional ConformanceUnits will become required, and so it is highly recommended that all servers support them.
Table 46 – Standard Event Subscription Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Events |
False |
|
Base Information |
Base Info Device Failure |
True |
|
Base Information |
Base Info EventQueueOverflow EventType |
True |
|
Base Information |
Base Info Progress Events |
True |
|
Base Information |
Base Info SemanticChange |
True |
|
Base Information |
Base Info System Status |
True |
|
Base Information |
Base Info System Status Underlying System |
True |
|
Monitored Item Services |
Monitor Basic |
False |
|
Monitored Item Services |
Monitor Complex Event Filter |
True |
|
Monitored Item Services |
Monitor Events |
False |
|
Monitored Item Services |
Monitor Items 10 |
False |
|
Monitored Item Services |
Monitor QueueSize_ServerMax |
False |
|
Subscription Basic |
False |
|
|
Subscription Minimum 02 |
False |
|
|
Subscription Publish Discard Policy |
False |
|
|
Subscription Publish Min 05 |
False |
Table 47 describes the details of the Address Space Notifier Server Facet. This Facet requires the support of a hierarchy of Object Nodes that are notifiers and Nodes that are event sources. The hierarchy is commonly used as a way to organize a plant into areas that can be managed by different operators.
Table 47 – Address Space Notifier Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Notifier Hierarchy |
False |
|
Address Space Model |
Address Space Source Hierarchy |
False |
Table 48 describes the details of the A & C Base Condition Server Facet. This Facet requires basic support for Conditions. Information about Conditions is provided through Event notifications and thus this Facet builds upon the Standard Event Subscription Server Facet. Conditions that are in an “interesting” state (as defined by the Server) can be refreshed using the Refresh Method, which requires support for the Method Server Facet. Optionally the server may also provide support for Condition classes
Table 48 – A & C Base Condition Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Standard Event Subscription Server Facet |
False |
|
|
Alarms and Conditions |
A & C Basic |
False |
|
Alarms and Conditions |
A & C Condition Sub-Classes |
True |
|
Alarms and Conditions |
A & C ConditionClasses |
True |
|
Alarms and Conditions |
A & C Refresh |
False |
Table 49 describes the details of the A & C Refresh2 Server Facet. This Facet enhances the A & C Base Condition Server Facet with support of the ConditionRefresh2 Method.
Table 49 – A & C Refresh2 Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Refresh2 |
False |
Table 50 describes the details of the A & C Address Space Instance Server Facet. This Facet specifies the support required for a Server to expose Alarms and Conditions in its AddressSpace. This includes the A & C AddressSpace information model.
Table 50 – A & C Address Space Instance Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Alarms and Conditions |
A & C Instances |
False |
Table 51 describes the details of the A & C Enable Server Facet. This Facet requires the enabling and disabling of Conditions. This Facet builds upon the A&C Base Condition Server Facet. Enabling and disabling also requires that instances of these ConditionTypes exist in the AddressSpace since the enable Method can only be invoked on an instance of the Condition
Table 51 – A & C Enable Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Enable |
False |
|
Alarms and Conditions |
A & C Instances |
False |
Table 52 describes the details of the A & C AlarmMetrics Server Facet. This Facet requires support for AlarmMetrics. AlarmMetrics expose status and potential issues in the alarm system. A Server can provide these metrics at various levels (operator station, plant area, overall system etc.).
Table 52 – A & C AlarmMetrics Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Alarms and Conditions |
A & C Alarm Metrics |
False |
Table 53 describes the details of the A & C Alarm Server Facet. This Facet requires support for Alarms. Alarms extend the ConditionType by adding an Active state which indicates when something in the system requires attention by an Operator. This Facet builds upon the A&C Base Condition Server Facet. This facet requires that discrete AlarmTypes be supported, it also allows for optional support of shelving, alarm comments and other discrete AlarmTypes such as Trip or Off-Normal.
Table 53 – A & C Alarm Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Alarm |
False |
|
Alarms and Conditions |
A & C Audible Sound |
True |
|
Alarms and Conditions |
A & C Comment |
True |
|
Alarms and Conditions |
A & C Discrepancy |
True |
|
Alarms and Conditions |
A & C Discrete |
False |
|
Alarms and Conditions |
A & C First in Group Alarm |
True |
|
Alarms and Conditions |
A & C OffNormal |
True |
|
Alarms and Conditions |
A & C On-Off Delay |
True |
|
Alarms and Conditions |
A & C Out Of Service |
True |
|
Alarms and Conditions |
A & C Re-Alarming |
True |
|
Alarms and Conditions |
A & C Shelving |
True |
|
Alarms and Conditions |
A & C Silencing |
True |
|
Alarms and Conditions |
A & C Suppression |
True |
|
Alarms and Conditions |
A & C Suppression by Operator |
True |
|
Alarms and Conditions |
A & C SystemOffNormal |
True |
|
Alarms and Conditions |
A & C Trip |
True |
Table 54 describes the details of the A & C Acknowledgeable Alarm Server Facet. This Facet requires support for Acknowledgement of active Alarms. This Facet builds upon the A & C Alarm Server Facet. Acknowledgement requires support of the Acknowledge Method and the Acknowledged state. Support of the Confirmed state and the Confirm Method is optional.
Table 54 – A & C Acknowledgeable Alarm Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Acknowledge |
False |
|
Alarms and Conditions |
A & C Confirm |
True |
Table 55 describes the details of the A & C Exclusive Alarming Server Facet. This Facet requires support for Alarms with multiple sub-states that identify different limit Conditions. This facet builds upon the A&C Alarm Server Facet. The term exclusive means only one sub-state can be active at a time. For example, a temperature exceeds the HighHigh limit the associated exclusive LevelAlarm will be in the HighHigh sub-state and not in the High sub-state. This Facet requires that a Server support at least one of the optional Alarm models: Limit, RateOfChange or Deviation.
Table 55 – A & C Exclusive Alarming Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Exclusive Deviation |
True |
|
Alarms and Conditions |
A & C Exclusive Level |
True |
|
Alarms and Conditions |
A & C Exclusive Limit |
False |
|
Alarms and Conditions |
A & C Exclusive RateOfChange |
True |
Table 56 describes the details of the A & C Non-Exclusive Alarming Server Facet. This Facet requires support for Alarms with multiple sub-states that identify different limit Conditions. This Facet builds upon the A&C Alarm Server Facet. The term non-exclusive means more than one sub-state can be active at a time. For example, if a temperature exceeds the HighHigh limit the associated non-exclusive LevelAlarm will be in both the High and the HighHigh sub-state. This Facet requires that a server support at least one of the optional alarm models: Limit, RateOfChange or Deviation.
Table 56 – A & C Non-Exclusive Alarming Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Non-Exclusive Deviation |
True |
|
Alarms and Conditions |
A & C Non-Exclusive Level |
True |
|
Alarms and Conditions |
A & C Non-Exclusive Limit |
False |
|
Alarms and Conditions |
A & C Non-Exclusive RateOfChange |
True |
Table 57 describes the details of the A & C Previous Instances Server Facet. This Facet requires support for Conditions with previous states that still require action on the part of the operator. This Facet builds upon the A&C Base Condition Server Facet. A common use case for this Facet is a safety critical system that requires that all Alarms be acknowledged even if it the original problem goes away and the Alarm returns to the inactive state. In these cases, the previous state with active Alarm is still reported by the Server until the Operator acknowledges it. When a Condition has previous states it will produce events with different Branch identifiers. When previous state no longer needs attention the branch will disappear.
Table 57 – A & C Previous Instances Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Branch |
False |
Table 58 describes the details of the A & C Dialog Server Facet. This Facet requires support of Dialog Conditions. This Facet builds upon the A & C BaseCondition Server Facet Dialogs are ConditionTypes used to request user input. They are typically used when a Server has entered some state that requires intervention by a Client. For example, a Server monitoring a paper machine indicates that a roll of paper has been wound and is ready for inspection. The Server would activate a Dialog Condition indicating to the user that an inspection is required. Once the inspection has taken place the user responds by informing the Server of an accepted or unaccepted inspection allowing the process to continue.
Table 58 – A & C Dialog Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Dialog |
False |
Table 59 describes the details of the A & C CertificateExpiration Server Facet. This Facet requires support of the CertificateExpirationAlarmType. It is used to inform Clients when the Server’s Certificate is within the defined expiration period.
Table 59 – A & C CertificateExpiration Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Acknowledge |
False |
|
Alarms and Conditions |
A & C Alarm |
False |
|
Alarms and Conditions |
A & C CertificateExpiration |
False |
|
Alarms and Conditions |
A & C Comment |
True |
|
Alarms and Conditions |
A & C Confirm |
True |
|
Alarms and Conditions |
A & C Shelving |
True |
Table 60 describes the details of the A & E Wrapper Facet. This Facet specifies the requirements for a UA Server that wraps an OPC Alarm & Event (AE) Server (COM). This Profile identifies the sub-set of the UA Alarm & Condition model which is provided by the COM OPC AE specification. It is intended to provide guidance to developers who are creating servers that front end existing applications. It is important to note that some OPC A&E COM Servers may not support all of the functionality provided by an OPC UA A&C server, in these cases similar functionality maybe available via some non-OPC interface. For example if an A&E COM server does not support sending Alarm Acknowledgement messages to the system that it is obtaining alarm information from, this functionality may be available via some out of scope features in the underlying Alarm system. Another possibility is that the underlying system does not require acknowledgements or automatically acknowledges the alarm.
Table 60 – A & E Wrapper Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Events |
False |
|
Address Space Model |
Address Space Notifier Hierarchy |
False |
|
Address Space Model |
Address Space Source Hierarchy |
False |
|
Alarms and Conditions |
A & C Acknowledge |
False |
|
Alarms and Conditions |
A & C Alarm |
False |
|
Alarms and Conditions |
A & C Basic |
False |
|
Alarms and Conditions |
A & C ConditionClasses |
False |
|
Alarms and Conditions |
A & C Refresh |
False |
|
Alarms and Conditions |
A & E Wrapper Mapping |
False |
|
Monitored Item Services |
Monitor Basic |
False |
|
Monitored Item Services |
Monitor Complex Event Filter |
False |
|
Monitored Item Services |
Monitor Events |
False |
|
Monitored Item Services |
Monitor Items 2 |
False |
|
Monitored Item Services |
Monitor QueueSize_ServerMax |
False |
|
Subscription Basic |
False |
|
|
Subscription Minimum 1 |
False |
|
|
Subscription Publish Discard Policy |
False |
|
|
Subscription Publish Min 02 |
False |
Table 61 describes the details of the Method Server Facet. This Facet specifies the support of Method invocation via the Call service. Methods are “lightweight” functions which are similar to the methods of a class found in any object-oriented programming language. A Method can have its scope bounded by an owning Object or an owning ObjectType. Methods with an ObjectType as their scope are similar to static methods in a class.
Table 61 – Method Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Method |
False |
|
Method Call |
False |
Table 62 describes the details of the Auditing Server Facet. This Facet requires the support of Auditing which includes the Standard Event Subscription Server Facet. Support of this Facet requires that Audit Events be produced when a client performs some action to change the state of the server, such as changing the AddressSpace, inserting or updating a value etc. The auditEntryId passed by the Client is a field contained in every Audit Event and allows actions to be traced across multiple systems. The Audit Event Types and their fields must be exposed in the Server’s AddressSpace
Table 62 – Auditing Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Standard Event Subscription Server Facet |
False |
|
|
Auditing |
Auditing Base |
False |
Table 63 describes the details of the Node Management Server Facet. This Facet requires the support of the Services that allow the Client to add, modify and delete Nodes in the AddressSpace. These Services provide an interface which can be used to configure Servers. This means all changes to the AddressSpace are expected to persist even after the Client has disconnected from the Server
Table 63 – Node Management Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Base |
False |
|
Base Information |
Base Info Model Change |
False |
|
Base Information |
Base Info Type System |
False |
|
False |
||
|
Node Management Add Ref |
False |
|
|
False |
||
|
Node Management Delete Ref |
False |
Table 64 describes the details of the User Role Base Server Facet. This Facet defines support of the OPC UA Information Model to expose configured user roles and permissions.
Table 64 – User Role Base Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security Role Server Base |
False |
Table 65 describes the details of the User Role Management Server Facet. This Facet defines support of the OPC UA approach to manage user roles and permissions and to grant access to Nodes and Services based on the assigned roles and permissions.
Table 65 – User Role Management Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
||
|
User Role Base Server Facet |
False |
|||
|
Security |
Security Role Server DefaultRolePermissions |
False |
||
|
Security |
Security Role Server IdentityManagement |
False |
||
|
Security |
Security Role Server Management |
False |
||
|
Security |
Security Role Server Restrict Applications |
True |
||
|
Security |
Security Role Server Restrict Endpoints |
True |
||
|
Security |
Security Role Server RolePermissions |
True |
||
|
Security |
Security Role Well Known |
False |
||
Table 66 describes the details of the State Machine Server Facet. This Facet defines support of StateMachines based on the types in UA Part 5.
Table 66 – State Machine Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Base Information |
Base Info Available States and Transitions |
True |
|
Base Information |
Base Info Finite State Machine Instance |
True |
|
Base Information |
Base Info State Machine Instance |
False |
Table 67 describes the details of the Client Redundancy Server Facet. This Facet defines the Server actions that are required for support of redundant Clients. Support of this Facet requires the implementation of the TransferSubscriptions Service which allows the transfer of Subscriptions from one Client’s Session to another Client’s Session.
Table 67 – Client Redundancy Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Subscription Transfer |
False |
Table 68 describes the details of the Redundancy Transparent Server Facet. This Facet requires support for transparent redundancy. If Servers implement transparent redundancy then the failover from one Server to another is transparent to the Client such that the Client is unaware that a failover has occurred; the Client does not need to do anything at all to keep data flowing. This type of redundancy is usually a hardware solution.
Table 68 – Redundancy Transparent Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Redundancy |
Redundancy Server Transparent |
False |
Table 69 describes the details of the Redundancy Visible Server Facet. This Facet specifies the support for non-transparent redundancy. Failover for this type of redundancy requires the Client to monitor Server status and to switch to a backup Server if it detects a failure. The Server shall expose the methods of failover it supports (cold, warm or hot). The failover method tells the Client what it must do when connecting to a Server and when a failure occurs. Cold redundancy requires a Client to reconnect to a backup Server after the initial Server has failed. Warm redundancy allows a Client to connect to multiple Servers, but only one Server will be providing values. In hot redundancy multiple Servers are able to provide data and a Client can connect to multiple Servers for the data.
Table 69 – Redundancy Visible Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Redundancy |
Redundancy Server |
False |
Table 70 describes the details of the Historical Raw Data Server Facet. This Facet defines the basic functionality when supporting historical data access for raw data.
Table 70 – Historical Raw Data Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Read |
False |
|
|
Historical Access |
Historical Access Data Max Nodes Read Continuation Point |
False |
|
Historical Access |
Historical Access Read Raw |
False |
|
Historical Access |
Historical Access ServerTimestamp |
True |
Table 71 describes the details of the Historical Aggregate Server Facet. This Facet indicates that the server supports aggregate processing to produce derived values from raw historical data.
Table 71 – Historical Aggregate Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Aggregates |
Aggregate – AnnotationCount |
True |
|
Aggregates |
Aggregate – Average |
True |
|
Aggregates |
Aggregate – Count |
True |
|
Aggregates |
Aggregate – Custom |
True |
|
Aggregates |
Aggregate – Delta |
True |
|
Aggregates |
Aggregate – DeltaBounds |
True |
|
Aggregates |
Aggregate – DurationBad |
True |
|
Aggregates |
Aggregate – DurationGood |
True |
|
Aggregates |
Aggregate – DurationInStateNonZero |
True |
|
Aggregates |
Aggregate – DurationInStateZero |
True |
|
Aggregates |
Aggregate – End |
True |
|
Aggregates |
Aggregate – EndBound |
True |
|
Aggregates |
Aggregate – Interpolative |
True |
|
Aggregates |
Aggregate – Maximum |
True |
|
Aggregates |
Aggregate – Maximum2 |
True |
|
Aggregates |
Aggregate – MaximumActualTime |
True |
|
Aggregates |
Aggregate – MaximumActualTime2 |
True |
|
Aggregates |
Aggregate – Minimum |
True |
|
Aggregates |
Aggregate – Minimum2 |
True |
|
Aggregates |
Aggregate – MinimumActualTime |
True |
|
Aggregates |
Aggregate – MinimumActualTime2 |
True |
|
Aggregates |
Aggregate – NumberOfTransitions |
True |
|
Aggregates |
Aggregate – PercentBad |
True |
|
Aggregates |
Aggregate – PercentGood |
True |
|
Aggregates |
Aggregate – Range |
True |
|
Aggregates |
Aggregate – Range2 |
True |
|
Aggregates |
Aggregate – StandardDeviationPopulation |
True |
|
Aggregates |
Aggregate – StandardDeviationSample |
True |
|
Aggregates |
Aggregate – Start |
True |
|
Aggregates |
Aggregate – StartBound |
True |
|
Aggregates |
Aggregate – TimeAverage |
True |
|
Aggregates |
Aggregate – TimeAverage2 |
True |
|
Aggregates |
Aggregate – Total |
True |
|
Aggregates |
Aggregate – Total2 |
True |
|
Aggregates |
Aggregate – VariancePopulation |
True |
|
Aggregates |
Aggregate – VarianceSample |
True |
|
Aggregates |
Aggregate – WorstQuality |
True |
|
Aggregates |
Aggregate – WorstQuality2 |
True |
|
Aggregates |
Aggregate Historical Configuration |
True |
|
Aggregates |
Aggregate Master Configuration |
False |
|
Attribute Historical Read |
False |
|
|
Historical Access |
Historical Access Aggregates |
False |
|
Historical Access |
Historical Access Data Max Nodes Read Continuation Point |
False |
Table 72 describes the details of the Historical Data AtTime Server Facet. This Facet indicates that the historical Server supports reading data by specifying specific timestamps.
Table 72 – Historical Data AtTime Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Read |
False |
|
|
Historical Access |
Historical Access Data Max Nodes Read Continuation Point |
False |
|
Historical Access |
Historical Access Time Instance |
False |
Table 73 describes the details of the Historical Access Modified Data Server Facet. This Facet defines support of reading modified historical values (values that where modified or inserted).
Table 73 – Historical Access Modified Data Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Read |
False |
|
|
Historical Access |
Historical Access Modified Values |
False |
Table 74 describes the details of the Historical Annotation Server Facet. This Facet defines support for the storage and retrieval of annotations for historical data.
Table 74 – Historical Annotation Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Read |
False |
|
|
Attribute Historical Update |
False |
|
|
Historical Access |
Historical Access Annotations |
False |
Table 75 describes the details of the Historical Data Insert Server Facet. This Facet includes Historical Data Insert functionality.
Table 75 – Historical Data Insert Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Update |
False |
|
|
Historical Access |
Historical Access Insert Value |
False |
|
Historical Access |
Historical Access ServerTimestamp |
True |
Table 76 describes the details of the Historical Data Update Server Facet. This Facet includes Historical Data Update functionality.
Table 76 – Historical Data Update Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Update |
False |
|
|
Historical Access |
Historical Access ServerTimestamp |
True |
|
Historical Access |
Historical Access Update Value |
False |
Table 77 describes the details of the Historical Data Replace Server Facet. This Facet includes Historical Data Replace functionality.
Table 77 – Historical Data Replace Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Update |
False |
|
|
Historical Access |
Historical Access Replace Value |
False |
|
Historical Access |
Historical Access ServerTimestamp |
True |
Table 78 describes the details of the Historical Data Delete Server Facet. This Facet includes Historical Data Delete functionality.
Table 78 – Historical Data Delete Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Update |
False |
|
|
Historical Access |
Historical Access Delete Value |
False |
Table 79 describes the details of the Historical Access Structured Data Server Facet. This Facet indicates that the Server supports storage and retrieval of structured values for all supported access types. If a listed access type is supported then the corresponding optional ConformanceUnit shall be supported.
Table 79 – Historical Access Structured Data Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Access |
Historical Access Structured Data Delete |
True |
|
Historical Access |
Historical Access Structured Data Insert |
True |
|
Historical Access |
Historical Access Structured Data Read Modified |
True |
|
Historical Access |
Historical Access Structured Data Read Raw |
False |
|
Historical Access |
Historical Access Structured Data Replace |
True |
|
Historical Access |
Historical Access Structured Data Time Instance |
True |
|
Historical Access |
Historical Access Structured Data Update |
True |
Table 80 describes the details of the Base Historical Event Server Facet. This Facet defines the server requirements to support basic Historical Event functionality, including simple filtering and general access.
Table 80 – Base Historical Event Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Read |
False |
|
|
Historical Access |
Historical Access Event Max Events Read Continuation Point |
False |
|
Historical Access |
Historical Access Events |
False |
Table 81 describes the details of the Historical Event Update Server Facet. This Facet includes Historical Event update access functionality.
Table 81 – Historical Event Update Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Update |
False |
|
|
Historical Access |
Historical Access Update Event |
False |
Table 82 describes the details of the Historical Event Replace Server Facet. This Facet includes Historical Event replace access functionality.
Table 82 – Historical Event Replace Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Update |
False |
|
|
Historical Access |
Historical Access Replace Event |
False |
Table 83 describes the details of the Historical Event Insert Server Facet. This Facet includes Historical Event insert access functionality.
Table 83 – Historical Event Insert Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Update |
False |
|
|
Historical Access |
Historical Access Insert Event |
False |
Table 84 describes the details of the Historical Event Delete Server Facet. This Facet includes Historical Event delete access functionality
Table 84 – Historical Event Delete Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Attribute Historical Update |
False |
|
|
Historical Access |
Historical Access Delete Event |
False |
Table 85 describes the details of the Aggregate Subscription Server Facet. This Facet defines the handling of the aggregate filter when subscribing for Attribute values.
Table 85 – Aggregate Subscription Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Standard DataChange Subscription Server Facet |
False |
|
|
Aggregates |
Aggregate Subscription – AnnotationCount |
True |
|
Aggregates |
Aggregate Subscription – Average |
True |
|
Aggregates |
Aggregate Subscription – Count |
True |
|
Aggregates |
Aggregate Subscription – Custom |
True |
|
Aggregates |
Aggregate Subscription – Delta |
True |
|
Aggregates |
Aggregate Subscription – DeltaBounds |
True |
|
Aggregates |
Aggregate Subscription – DurationBad |
True |
|
Aggregates |
Aggregate Subscription – DurationGood |
True |
|
Aggregates |
Aggregate Subscription – DurationInStateNonZero |
True |
|
Aggregates |
Aggregate Subscription – DurationInStateZero |
True |
|
Aggregates |
Aggregate Subscription – End |
True |
|
Aggregates |
Aggregate Subscription – EndBound |
True |
|
Aggregates |
Aggregate Subscription – Filter |
False |
|
Aggregates |
Aggregate Subscription – Interpolative |
True |
|
Aggregates |
Aggregate Subscription – Maximum |
True |
|
Aggregates |
Aggregate Subscription – Maximum2 |
True |
|
Aggregates |
Aggregate Subscription – MaximumActualTime |
True |
|
Aggregates |
Aggregate Subscription – MaximumActualTime2 |
True |
|
Aggregates |
Aggregate Subscription – Minimum |
True |
|
Aggregates |
Aggregate Subscription – Minimum2 |
True |
|
Aggregates |
Aggregate Subscription – MinimumActualTime |
True |
|
Aggregates |
Aggregate Subscription – MinimumActualTime2 |
True |
|
Aggregates |
Aggregate Subscription – NumberOfTransitions |
True |
|
Aggregates |
Aggregate Subscription – PercentBad |
True |
|
Aggregates |
Aggregate Subscription – PercentGood |
True |
|
Aggregates |
Aggregate Subscription – Range |
True |
|
Aggregates |
Aggregate Subscription – Range2 |
True |
|
Aggregates |
Aggregate Subscription – StandardDeviationPopulation |
True |
|
Aggregates |
Aggregate Subscription – StandardDeviationSample |
True |
|
Aggregates |
Aggregate Subscription – Start |
True |
|
Aggregates |
Aggregate Subscription – StartBound |
True |
|
Aggregates |
Aggregate Subscription – TimeAverage |
True |
|
Aggregates |
Aggregate Subscription – TimeAverage2 |
True |
|
Aggregates |
Aggregate Subscription – Total |
True |
|
Aggregates |
Aggregate Subscription – Total2 |
True |
|
Aggregates |
Aggregate Subscription – VariancePopulation |
True |
|
Aggregates |
Aggregate Subscription – VarianceSample |
True |
|
Aggregates |
Aggregate Subscription – WorstQuality |
True |
|
Aggregates |
Aggregate Subscription – WorstQuality2 |
True |
|
Monitored Item Services |
Monitor Aggregate Filter |
False |
Table 86 describes the details of the Nano Embedded Device Server Profile. This Profile is a FullFeatured Profile intended for chip level devices with limited resources. This Profile is functionally equivalent to the Core Server Facet and defines the OPC UA TCP binary protocol as the required transport profile.The support of Diagnostic Objects and Variables is optional for this Profile despite it being defined as “mandatory” in UA Part 5. Support of Diagnostic Objects and Variables is mandatory in some higher level Profiles.Exposing types in the AddressSpace is optional for this Profile except if custom types (i.e. types that are derived from well-known ObjectTypes, VariableTypes, ReferenceType or DataTypes) are used. Exposing all supported types in the AddressSpace is mandatory in some higher level Profiles.
Table 86 – Nano Embedded Device Server Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Core Server Facet |
False |
|
|
UA-TCP UA-SC UA-Binary |
False |
|
|
Base Information |
Base Info Custom Type System |
True |
|
Base Information |
Base Info Diagnostics |
True |
Table 87 describes the details of the Nano Embedded Device 2017 Server Profile. This Profile is a FullFeatured Profile intended for chip level devices with limited resources. This Profile is functionally equivalent to the Core Server Facet and defines the OPC UA TCP binary protocol as the required transport profile.The support of Diagnostic Objects and Variables is optional for this Profile despite it being defined as “mandatory” in UA Part 5. Support of Diagnostic Objects and Variables is mandatory in some higher level Profiles. Exposing types in the AddressSpace is optional for this Profile except if custom types (i.e. types that are derived from well-known ObjectTypes, VariableTypes, ReferenceType or DataTypes) are used. Exposing all supported types in the AddressSpace is mandatory in some higher level Profiles.This profile supersedes the “Nano Embedded Device Server Profile”.
Table 87 – Nano Embedded Device 2017 Server Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Core 2017 Server Facet |
False |
|
|
UA-TCP UA-SC UA-Binary |
False |
|
|
Base Information |
Base Info Custom Type System |
True |
|
Base Information |
Base Info Diagnostics |
True |
Table 88 describes the details of the Micro Embedded Device Server Profile. This Profile is a FullFeatured Profile intended for small devices with limited resources. This Profile builds upon the Nano Embedded Device Server Profile. The most important additions are: support for subscriptions via the Embedded Data Change Subscription Server Facet and support for at least two sessions. A complete Type System is not required; however, if the Server implements any non-UA types then these types and their super-types must be exposed.
Table 88 – Micro Embedded Device Server Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Embedded DataChange Subscription Server Facet |
False |
|
|
False |
||
|
Session Minimum 2 Parallel |
False |
Table 89 describes the details of the Micro Embedded Device 2017 Server Profile. This Profile is a FullFeatured Profile intended for small devices with limited resources. This Profile builds upon the Nano Embedded Device Server Profile. The most important additions are: support for subscriptions via the Embedded Data Change Subscription Server Facet and support for at least two sessions. A complete Type System is not required; however, if the Server implements any non-UA types then these types and their super-types must be exposed.This profile supersedes the “Micro Embedded Device Server Profile”.
Table 89 – Micro Embedded Device 2017 Server Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Embedded DataChange Subscription Server Facet |
False |
|
|
False |
||
|
Session Minimum 2 Parallel |
False |
Table 90 describes the details of the Embedded UA Server Profile. This Profile is a FullFeatured Profile that is intended for devices with more than 50 MBs of memory and a more powerful processor. This Profile builds upon the Micro Embedded Device Server Profile. The most important additions are: support for security via the Security Policy – Basic128Rsa15 Facet, and support for the Standard DataChange Subscription Server Facet. This Profile also requires that servers expose all OPC-UA types that are used by the Server including their components and their super-types.
Table 90 – Embedded UA Server Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
SecurityPolicy – Basic128Rsa15 |
False |
|
|
Standard DataChange Subscription Server Facet |
False |
|
|
Base Information |
Base Info Engineering Units |
True |
|
Base Information |
Base Info Placeholder Modelling Rules |
True |
|
Base Information |
Base Info Type System |
False |
|
Security |
Security Default ApplicationInstance Certificate |
False |
Table 91 describes the details of the Embedded 2017 UA Server Profile. This Profile is a FullFeatured Profile that is intended for devices with more than 50 MBs of memory and a more powerful processor. This Profile builds upon the Micro Embedded Device Server Profile. The most important additions are: support for security via the Security Policies and support for the Standard DataChange Subscription Server Facet. This Profile also requires that Servers expose all OPC-UA types that are used by the Server including their components and their super-types. This profile supersedes the “Embedded Device Server Profile”.
Table 91 – Embedded 2017 UA Server Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Standard DataChange Subscription 2017 Server Facet |
False |
|
|
Base Information |
Base Info Engineering Units |
True |
|
Base Information |
Base Info Type System |
False |
|
Security |
Security – No Application Authentication |
True |
|
Security |
Security Default ApplicationInstance Certificate |
False |
|
Security |
Security Policy Required |
False |
Table 92 describes the details of the Standard UA Server Profile. This Profile is a FullFeatured Profile that defines a minimum set of functionality required for PC based OPC UA servers. Such a server must provide the base AddressSpace structure with type nodes, instance nodes and diagnostic information. The Server must provide connection establishment through the OPC UA TCP binary protocol with security and the creation of at least 50 parallel sessions. It includes view services like browsing and the attribute services for reading and writing of current values. In addition, the monitoring of data changes is included with a minimum of 5 subscriptions for half of the required sessions (total 225) and a minimum of 500 monitored items for half of the subscriptions (total 56250).
Table 92 – Standard UA Server Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Enhanced DataChange Subscription Server Facet |
False |
|
|
User Token – X509 Certificate Server Facet |
False |
|
|
Attribute Write StatusCode & Timestamp |
True |
|
|
Base Information |
Base Info Diagnostics |
False |
|
Discovery Register |
False |
|
|
Discovery Register2 |
True |
|
|
Session Cancel |
False |
|
|
Session Change User |
True |
|
|
Session Minimum 50 Parallel |
False |
|
|
View Services |
View Minimum Continuation Point 05 |
False |
Table 93 describes the details of the Standard 2017 UA Server Profile. This Profile is a FullFeatured Profile that defines a minimum set of functionality required for PC based OPC UA servers. Compared to the embedded profiles, the Profile requires higher limits for Sessions, Subscriptions and Monitored Items. It also requires support of diagnostic information. This profile supersedes the “Standard UA Server Profile”.
Table 93 – Standard 2017 UA Server Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Enhanced DataChange Subscription 2017 Server Facet |
False |
|
|
User Token – X509 Certificate Server Facet |
False |
|
|
Attribute Write StatusCode & Timestamp |
True |
|
|
Base Information |
Base Info Diagnostics |
False |
|
Discovery Register |
False |
|
|
Discovery Register2 |
False |
|
|
Session Cancel |
False |
|
|
Session Change User |
True |
|
|
Session Minimum 50 Parallel |
False |
|
|
View Services |
View Minimum Continuation Point 05 |
False |
Table 94 describes the details of the Core Client Facet. This Facet defines the core functionality required for any Client. This Facet includes the core functions for Security and Session handling.
|
Group |
Conformance Unit / Profile Title |
Optional |
|
SecurityPolicy – Basic128Rsa15 |
False |
|
|
SecurityPolicy – None |
False |
|
|
User Token – User Name Password Client Facet |
False |
|
|
User Token – X509 Certificate Client Facet |
False |
|
|
Base Information |
Base Info Client Estimated Return Time |
True |
|
Security |
Security Administration |
False |
|
False |
||
|
True |
||
|
False |
||
|
False |
||
|
True |
||
|
False |
||
|
True |
Table 95 describes the details of the Core 2017 Client Facet. This Facet defines the core functionality required for any Client. This Facet includes the core functions for Security and Session handling.This Facet supersedes the Core Client Facet.
Table 95 – Core 2017 Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
SecurityPolicy – None |
False |
|
|
User Token – User Name Password Client Facet |
False |
|
|
User Token – X509 Certificate Client Facet |
False |
|
|
Base Information |
Base Info Client Estimated Return Time |
True |
|
Base Information |
Base Info Client Selection List |
True |
|
Security |
Security Administration |
False |
|
Security |
Security Policy Required |
False |
|
False |
||
|
False |
||
|
True |
||
|
False |
||
|
False |
||
|
True |
||
|
False |
||
|
True |
Table 96 describes the details of the Sessionless Client Facet. Defines the use of Sessionless Service invocation in a Client.
Table 96 – Sessionless Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
True |
||
|
False |
Table 97 describes the details of the Reverse Connect Client Facet. This Facet defines support of reverse connectivity in a Client. Usually, a connection is opened by the Client before starting the UA-specific handshake. This will fail, however, when Servers are behind firewalls. In the reverse connectivity scenario, the Client accepts a connection request and a ReverseHello message from a Server and establishes a Secure Channel using this connection.
Table 97 – Reverse Connect Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Protocol and Encoding |
Protocol Reverse Connect Client |
False |
Table 98 describes the details of the Base Client Behaviour Facet. This Facet indicates that the Client supports behaviour that Clients shall follow for best use by operators and administrators. They include allowing configuration of an endpoint for a server without using the discovery service set; Support for manual security setting configuration and behaviour with regard to security issues; support for Automatic reconnection to a disconnected server. These behaviours can only be tested in a test lab. They are best practice guidelines.
Table 98 – Base Client Behaviour Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
||
|
Base Information |
True |
|||
|
False |
||||
|
Security |
Security Administration |
False |
||
|
Security |
Security Administration – XML Schema |
False |
||
|
Security |
Security Certificate Administration |
False |
||
|
True |
||||
|
Subscription Client Multiple |
False |
|||
|
Subscription Client Publish Configurable |
False |
|||
Table 99 describes the details of the Discovery Client Facet. This Facet defines the ability to discover Servers and their Endpoints.
Table 99 – Discovery Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
False |
||
|
False |
||
|
True |
||
|
False |
||
|
False |
Table 100 describes the details of the Subnet Discovery Client Facet. Support of this Facet enables discovery of the Server on a subnet.
Table 100 – Subnet Discovery Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
True |
||
|
True |
Table 101 describes the details of the Global Discovery Client Facet. Support of this Facet enables system-wide discovery of Servers using a Global Discovery Server (GDS).
Table 101 – Global Discovery Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
True |
||
|
False |
Table 102 describes the details of the Global Certificate Management Client Facet. This Facet defines the capability to interact with a Global Certificate Management Server to obtain an initial or renewed Certificate and Trust Lists.
Table 102 – Global Certificate Management Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Pull Model for Global Certificate and TrustList Management |
False |
Table 103 describes the details of the KeyCredential Service Client Facet. This Facet defines the capability to interact with a KeyCredential Service to obtain KeyCredentials. For example KeyCredentials are needed to access an Authorization Service or a Broker. The KeyCredential Service is typically part of a system-wide tool, like a GDS that also manages Applications, Access Tokens, and Certificates.
Table 103 – KeyCredential Service Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Pull Model for KeyCredential Service |
False |
Table 104 describes the details of the Access Token Request Client Facet. A Client Facet for using the RequestAccessToken Method on an Authorization Server (defined in Part 12) to request such a token.
Table 104 – Access Token Request Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
False |
Table 105 describes the details of the AddressSpace Lookup Client Facet. This Facet defines the ability to navigate through the AddressSpace and includes basic AddressSpace concepts, view and browse functionality and simple attribute read functionality.
Table 105 – AddressSpace Lookup Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Client Base |
False |
|
False |
||
|
True |
||
|
Base Information |
Base Info Client Basic |
False |
|
Base Information |
True |
|
|
View Services |
View Client Basic Browse |
False |
|
View Services |
View Client Basic ResultSet Filtering |
False |
|
View Services |
View Client RegisterNodes |
True |
|
View Services |
True |
|
|
View Services |
True |
|
|
View Services |
View Client TranslateBrowsePath |
True |
Table 106 describes the details of the Request State Change Client Facet. This Facet specifies the ability to invoke the RequestServerStateChange Method.
Table 106 – Request State Change Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Base Information |
Base Info Client RequestServerStateChange |
False |
Table 107 describes the details of the File Access Client Facet. This Facet defines the ability to use File transfer via the defined FileType. This includes reading and optionally writing.
Table 107 – File Access Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Base Information |
Base Info Client FileType Base |
False |
|
Base Information |
Base Info Client FileType Write |
True |
Table 108 describes the details of the Entry Level Support 2015 Client Facet. This Facet defines the ability to interoperate with low-end Servers, in particular Servers that support the Nano Embedded Profile but in general Servers with defined limits.
Table 108 – Entry Level Support 2015 Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Base Information |
Base Info Client Honour Operation Limits |
False |
|
Base Information |
Base Info Client Type Pre-Knowledge |
False |
|
False |
||
|
Subscription Client Fallback |
False |
Table 109 describes the details of the Multi-Server Client Connection Facet. This Facet defines the ability for simultaneous access to multiple Servers.
Table 109 – Multi-Server Client Connection Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
Table 110 describes the details of the Documentation – Client. This Facet provides a list of user documentation that a Client application should provide.
Table 110 – Documentation – Client
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Miscellaneous |
Documentation Client – Installation |
False |
|
Miscellaneous |
Documentation Client – Multiple Languages |
True |
|
Miscellaneous |
Documentation Client – On-line |
True |
|
Miscellaneous |
True |
|
|
Miscellaneous |
Documentation Client – Trouble Shooting Guide |
True |
|
Miscellaneous |
Documentation Client – Users Guide |
False |
Table 111 describes the details of the Attribute Read Client Facet. This Facet defines the ability to read Attribute values of Nodes.
Table 111 – Attribute Read Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
||
|
Address Space Model |
Address Space Client Atomicity |
True |
||
|
Address Space Model |
Address Space Client Complex Data Dictionary |
True |
||
|
Address Space Model |
True |
|||
|
Address Space Model |
Address Space Client Full Array Only |
True |
||
|
False |
||||
|
True |
||||
|
True |
||||
Table 112 describes the details of the Attribute Write Client Facet. This Facet defines the ability to write Attribute values of Nodes.
Table 112 – Attribute Write Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
||
|
Address Space Model |
Address Space Client Atomicity |
True |
||
|
Address Space Model |
Address Space Client Complex Data Dictionary |
True |
||
|
Address Space Model |
True |
|||
|
Address Space Model |
Address Space Client Full Array Only |
True |
||
|
False |
||||
|
True |
||||
|
True |
||||
Table 113 describes the details of the DataChange Subscriber Client Facet. This Facet defines the ability to monitor Attribute values for data change.
Table 113 – DataChange Subscriber Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
||
|
Address Space Model |
Address Space Client Atomicity |
True |
||
|
Address Space Model |
Address Space Client Complex Data Dictionary |
True |
||
|
Address Space Model |
True |
|||
|
Address Space Model |
Address Space Client Full Array Only |
True |
||
|
Base Information |
True |
|||
|
Base Information |
True |
|||
|
Monitored Item Services |
Monitor Client by Index |
False |
||
|
Monitored Item Services |
Monitor Client Complex Value |
True |
||
|
Monitored Item Services |
Monitor Client Deadband Filter |
True |
||
|
Monitored Item Services |
Monitor Client Modify |
True |
||
|
Monitored Item Services |
Monitor Client Trigger |
True |
||
|
Monitored Item Services |
Monitor Client Value Change |
False |
||
|
Subscription Client Basic |
False |
|||
|
Subscription Client Modify |
True |
|||
|
Subscription Client Multiple |
True |
|||
|
Subscription Client Republish |
False |
|||
Table 114 describes the details of the Durable Subscription Client Facet. This Facet specifies use of durable Subscriptions. It implies support of any of the DataChange or Event Subscriber Facets.
Table 114 – Durable Subscription Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Subscription Client Durable |
False |
Table 115 describes the details of the DataAccess Client Facet. This Facet defines the ability to utilize the DataAccess Information Model, i.e., industrial automation data like analog and discrete data items and their quality of service.
Table 115 – DataAccess Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Client Base |
False |
|
Address Space Model |
Address Space Client Complex Data Dictionary |
True |
|
False |
||
|
True |
||
|
True |
||
|
Data Access |
Data Access Client AnalogItems |
True |
|
Data Access |
Data Access Client Basic |
False |
|
Data Access |
Data Access Client Deadband |
True |
|
Data Access |
Data Access Client MultiState |
True |
|
Data Access |
Data Access Client MultiStateValueDiscrete |
True |
|
Data Access |
Data Access Client SemanticChange |
True |
|
Data Access |
Data Access Client TwoState |
True |
Table 116 describes the details of the Event Subscriber Client Facet. This Facet defines the ability to subscribe for Event Notifications. This includes basic AddressSpace concept and the browsing of it, adding events and event filters as monitored items and adding subscriptions.
Table 116 – Event Subscriber Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Client Base |
False |
|
Monitored Item Services |
True |
|
|
Monitored Item Services |
False |
|
|
Monitored Item Services |
Monitor Client Events |
False |
|
Monitored Item Services |
Monitor Client Modify |
True |
|
Monitored Item Services |
Monitor Client Trigger |
True |
|
Subscription Client Basic |
False |
|
|
Subscription Client Modify |
True |
|
|
Subscription Client Multiple |
True |
|
|
Subscription Client Republish |
False |
|
|
View Services |
View Client Basic Browse |
True |
|
View Services |
View Client TranslateBrowsePath |
True |
Table 117 describes the details of the Base Event Processing Client Facet. This Facet defines the ability to subscribe for and process basic OPC UA Events. The Client has to support at least one of the Events in the Facet.
Table 117 – Base Event Processing Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Base Information |
Base Info Client Change Events |
True |
|
Base Information |
Base Info Client Device Failure |
True |
|
Base Information |
Base Info Client Progress Events |
True |
|
Base Information |
Base Info Client System Status |
True |
|
Base Information |
Base Info Client System Status Underlying System |
True |
|
Base Information |
Base Info Event Processing |
False |
Table 118 describes the details of the Notifier and Source Hierarchy Client Facet. This Facet defines the ability to find and use a hierarchy of Objects that are event notifier and Nodes that are event sources in the Server AddressSpace.
Table 118 – Notifier and Source Hierarchy Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Address Space Model |
Address Space Client Notifier Hierarchy |
False |
|
Address Space Model |
Address Space Client Source Hierarchy |
False |
|
Subscription Client Publish Configurable |
False |
Table 119 describes the details of the A & C Base Condition Client Facet. This Facet defines the ability to use the Alarm and Condition basic model. This includes the ability to subscribe for Events and to initiate a Refresh Method.
Table 119 – A & C Base Condition Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
False |
||
|
Alarms and Conditions |
A & C Basic Client |
False |
|
Alarms and Conditions |
True |
|
|
Alarms and Conditions |
A & C ConditionClasses Client |
False |
|
Alarms and Conditions |
A & C Refresh Client |
False |
Table 120 describes the details of the A & C Refresh2 Client Facet. This Facet enhances the A & C Base Condition Server Facet with the ability to initiate a ConditionRefresh2 Method.
Table 120 – A & C Refresh2 Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Refresh2 Client |
False |
Table 121 describes the details of the A & C Address Space Instance Client Facet. This Facet defines the ability to use Condition instances in the AddressSpace.
Table 121 – A & C Address Space Instance Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Alarms and Conditions |
A & C Instances Client |
False |
Table 122 describes the details of the A & C Enable Client Facet. This Facet defines the ability to enable and disable Alarms.
Table 122 – A & C Enable Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Enable Client |
False |
Table 123 describes the details of the A & C AlarmMetrics Client Facet. This Facet defines the ability to use the AlarmMetrics model, i.e. understand and use the collected alarm metrics at any level in the HasNotifier hierarchy.
Table 123 – A & C AlarmMetrics Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Alarms and Conditions |
False |
Table 124 describes the details of the A & C Alarm Client Facet. This Facet defines the ability to use the alarming model (the AlarmType or any of the sub-types).
Table 124 – A & C Alarm Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Acknowledge Client |
False |
|
Alarms and Conditions |
False |
|
|
Alarms and Conditions |
A & C Audible Sound Client |
True |
|
Alarms and Conditions |
A & C Comment Client |
True |
|
Alarms and Conditions |
A & C Confirm Client |
True |
|
Alarms and Conditions |
A & C Discrepancy Client |
True |
|
Alarms and Conditions |
A & C Discrete Client |
False |
|
Alarms and Conditions |
True |
|
|
Alarms and Conditions |
A & C OffNormal Client |
True |
|
Alarms and Conditions |
A & C On-Off Delay Client |
True |
|
Alarms and Conditions |
True |
|
|
Alarms and Conditions |
A & C Re-Alarming Client |
True |
|
Alarms and Conditions |
A & C Shelving Client |
True |
|
A & C Silencing Client |
True |
|
|
Alarms and Conditions |
A & C Suppression by Operator Client |
True |
|
A & C Suppression Client |
True |
|
|
Alarms and Conditions |
A & C SystemOffNormal Client |
True |
|
Alarms and Conditions |
A & C Trip Client |
True |
Table 125 describes the details of the A & C Exclusive Alarming Client Facet. This Facet defines the ability to use the exclusive Alarm model. This includes understanding the various subtypes such as ExclusiveRateOfChangeAlarm, ExclusiveLevelAlarm and ExclusiveDeviationAlarm.
Table 125 – A & C Exclusive Alarming Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Exclusive Deviation Client |
True |
|
Alarms and Conditions |
A & C Exclusive Level Client |
True |
|
Alarms and Conditions |
A & C Exclusive Limit Client |
False |
|
Alarms and Conditions |
A & C Exclusive RateOfChange Client |
True |
Table 126 describes the details of the A & C Non-Exclusive Alarming Client Facet. This Facet defines the ability to use the non-exclusive Alarm model. This includes understanding the various subtypes such as NonExclusiveRateOfChangeAlarm, NonExclusiveLevelAlarm and NonExclusiveDeviationAlarm.
Table 126 – A & C Non-Exclusive Alarming Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Non-Exclusive Deviation Client |
True |
|
Alarms and Conditions |
A & C Non-Exclusive Level Client |
True |
|
Alarms and Conditions |
A & C Non-Exclusive Limit Client |
False |
|
Alarms and Conditions |
A & C Non-Exclusive RateOfChange Client |
True |
Table 127 describes the details of the A & C Previous Instances Client Facet. This Facet defines the ability to use previous instances of Alarms. This implies the ability to understand branchIds.
Table 127 – A & C Previous Instances Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Branch Client |
False |
Table 128 describes the details of the A & C Dialog Client Facet. This Facet defines the ability to use the dialog model. This implies the support of Method invocation to respond to dialog messages.
Table 128 – A & C Dialog Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Dialog Client |
False |
Table 129 describes the details of the A & C CertificateExpiration Client Facet. This Facet defines the ability to use the CertificateExpirationAlarmType.
Table 129 – A & C CertificateExpiration Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Alarms and Conditions |
A & C Acknowledge Client |
True |
|
Alarms and Conditions |
False |
|
|
Alarms and Conditions |
A & C CertificateExpiration Client |
False |
|
Alarms and Conditions |
A & C Comment Client |
True |
|
Alarms and Conditions |
A & C Confirm Client |
True |
|
Alarms and Conditions |
A & C Shelving Client |
True |
Table 130 describes the details of the A & E Proxy Facet. This Facet describes the functionality used by a default A & E Client proxy. A Client exposes this Facet so that a Server may be able to better understand the commands that are being issued by the Client, since this Facet indicates that the Client is an A&E Com Client.
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Client Base |
False |
|
Alarms and Conditions |
A & C Acknowledge Client |
False |
|
Alarms and Conditions |
False |
|
|
Alarms and Conditions |
A & C Basic Client |
False |
|
Alarms and Conditions |
A & C ConditionClasses Client |
False |
|
Alarms and Conditions |
A & C Discrete Client |
False |
|
Alarms and Conditions |
A & C Exclusive Deviation Client |
False |
|
Alarms and Conditions |
A & C Exclusive Level Client |
False |
|
Alarms and Conditions |
A & C Exclusive Limit Client |
False |
|
Alarms and Conditions |
A & C Exclusive RateOfChange Client |
False |
|
Alarms and Conditions |
A & C Instances Client |
False |
|
Alarms and Conditions |
A & C Non-Exclusive Deviation Client |
False |
|
Alarms and Conditions |
A & C Non-Exclusive Level Client |
False |
|
Alarms and Conditions |
A & C Non-Exclusive Limit Client |
False |
|
Alarms and Conditions |
A & C Non-Exclusive RateOfChange Client |
False |
|
Alarms and Conditions |
A & C OffNormal Client |
False |
|
Alarms and Conditions |
A & C Refresh Client |
False |
|
Alarms and Conditions |
A & C SystemOffNormal Client |
True |
|
Alarms and Conditions |
A & C Trip Client |
False |
|
False |
||
|
Base Information |
Base Info Client Basic |
False |
|
Base Information |
Base Info Client Change Events |
False |
|
False |
||
|
False |
||
|
False |
||
|
False |
||
|
False |
||
|
False |
||
|
False |
||
|
Monitored Item Services |
False |
|
|
Monitored Item Services |
False |
|
|
Monitored Item Services |
Monitor Client Events |
False |
|
Security |
Security Administration |
False |
|
Security |
Security Administration – XML Schema |
False |
|
Security |
Security Certificate Administration |
False |
|
False |
||
|
Subscription Client Basic |
False |
|
|
Subscription Client Multiple |
False |
|
|
Subscription Client Publish Configurable |
False |
|
|
Subscription Client Republish |
False |
|
|
View Services |
View Client Basic Browse |
False |
|
View Services |
View Client Basic ResultSet Filtering |
False |
|
View Services |
View Client TranslateBrowsePath |
False |
Table 131 describes the details of the Method Client Facet. This Facet defines the ability to call arbitrary Methods.
Table 131 – Method Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
Table 132 describes the details of the Auditing Client Facet. This Facet defines the ability to monitor Audit Events.
Table 132 – Auditing Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Auditing |
Auditing Client Audit ID |
False |
|
Auditing |
Auditing Client Subscribes |
False |
Table 133 describes the details of the Node Management Client Facet. This Facet defines the ability to configure the AddressSpace of an OPC UA Server through OPC UA Node Management Service Set.
Table 133 – Node Management Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Client Base |
False |
|
False |
Table 134 describes the details of the Advanced Type Programming Client Facet. This Facet defines the ability to use the type model and process the instance AddressSpace based on the type model. For example a client may contain generic displays that are based on a type, in that they contain a relative path from some main type. On call up this main type is matched to an instance and all of display items are resolved based on the provided type model.
Table 134 – Advanced Type Programming Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Client Base |
False |
|
Base Information |
Base Info Client Basic |
False |
|
Base Information |
Base Info Client Type Programming |
False |
|
View Services |
View Client TranslateBrowsePath |
False |
Table 135 describes the details of the User Role Management Client Facet. This Facet defines knowledge of the OPC UA Information Model for user roles and permissions and the use of the Methods to manage them.
Table 135 – User Role Management Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security Role Client Base |
False |
|
Security |
Security Role Client DefaultRolePermissions |
False |
|
Security |
Security Role Client Management |
False |
|
Security |
Security Role Client Restrict Applications |
True |
|
Security |
Security Role Client Restrict Endpoints |
True |
|
Security |
Security Role Client RolePermissions |
False |
Table 136 describes the details of the State Machine Client Facet. This Facet defines the ability to use state machines based on the StateMachineType or a sub-type.
Table 136 – State Machine Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Base Information |
Base Info Client Available States and Transitions |
True |
|
Base Information |
Base Info Client Finite State Machine Instance |
True |
|
Base Information |
Base Info Client State Machine Instance |
False |
Table 137 describes the details of the Diagnostic Client Facet. This Facet defines the ability to read and process diagnostic information that is part of the OPC UA information model.
Table 137 – Diagnostic Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space Client Base |
False |
|
Base Information |
Base Info Client Basic |
False |
|
Base Information |
Base Info Client Diagnostics |
False |
Table 138 describes the details of the Redundant Client Facet. This Facet defines the ability to use the redundancy feature available for redundant Clients.
Table 138 – Redundant Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Redundancy |
Redundancy Client |
False |
|
Subscription Client TransferSubscriptions |
True |
Table 139 describes the details of the Redundancy Switch Client Facet. A Client that supports this Facet supports monitoring the redundancy status for non-transparent redundant Servers and switching to the backup Server when they recognize a change.
Table 139 – Redundancy Switch Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Redundancy |
Redundancy Client Switch |
False |
Table 140 describes the details of the Historical Access Client Facet. This Facet defines the ability to read, process, and update historical data.
Table 140 – Historical Access Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Historical Access |
Historical Access Client Browse |
False |
|
Historical Access |
Historical Access Client Read Raw |
False |
Table 141 describes the details of the Historical Data AtTime Client Facet. This Facet defines the ability to access data at specific instances in time.
Table 141 – Historical Data AtTime Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Access Client Facet |
False |
|
|
Historical Access |
Historical Access Client Time Instance |
False |
Table 142 describes the details of the Historical Aggregate Client Facet. This Facet defines the ability to read historical data by specifying the needed aggregate. This implies consideration of the list of aggregates supported by the Server.
Table 142 – Historical Aggregate Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Aggregates |
Aggregate – Client AnnotationCount |
True |
|
Aggregates |
Aggregate – Client Average |
True |
|
Aggregates |
Aggregate – Client Count |
True |
|
Aggregates |
Aggregate – Client Custom Aggregates |
True |
|
Aggregates |
Aggregate – Client Delta |
True |
|
Aggregates |
Aggregate – Client DeltaBounds |
True |
|
Aggregates |
Aggregate – Client DurationBad |
True |
|
Aggregates |
Aggregate – Client DurationGood |
True |
|
Aggregates |
Aggregate – Client DurationInStateNonZero |
True |
|
Aggregates |
Aggregate – Client DurationInStateZero |
True |
|
Aggregates |
Aggregate – Client End |
True |
|
Aggregates |
Aggregate – Client EndBound |
True |
|
Aggregates |
Aggregate – Client Interpolative |
True |
|
Aggregates |
Aggregate – Client Maximum |
True |
|
Aggregates |
Aggregate – Client Maximum2 |
True |
|
Aggregates |
Aggregate – Client MaximumActualTime |
True |
|
Aggregates |
Aggregate – Client MaximumActualTime2 |
True |
|
Aggregates |
Aggregate – Client Minimum |
True |
|
Aggregates |
Aggregate – Client Minimum2 |
True |
|
Aggregates |
Aggregate – Client MinimumActualTime |
True |
|
Aggregates |
Aggregate – Client MinimumActualTime2 |
True |
|
Aggregates |
Aggregate – Client NumberOfTransitions |
True |
|
Aggregates |
Aggregate – Client PercentBad |
True |
|
Aggregates |
Aggregate – Client PercentGood |
True |
|
Aggregates |
Aggregate – Client Range |
True |
|
Aggregates |
Aggregate – Client Range2 |
True |
|
Aggregates |
Aggregate – Client StandardDeviationPopulation |
True |
|
Aggregates |
Aggregate – Client StandardDeviationSample |
True |
|
Aggregates |
Aggregate – Client Start |
True |
|
Aggregates |
Aggregate – Client StartBound |
True |
|
Aggregates |
Aggregate – Client TimeAverage |
True |
|
Aggregates |
Aggregate – Client TimeAverage2 |
True |
|
Aggregates |
Aggregate – Client Total |
True |
|
Aggregates |
Aggregate – Client Total2 |
True |
|
Aggregates |
Aggregate – Client Usage |
False |
|
Aggregates |
Aggregate – Client VariancePopulation |
True |
|
Aggregates |
Aggregate – Client VarianceSample |
True |
|
Aggregates |
Aggregate – Client WorstQuality |
True |
|
Aggregates |
Aggregate – Client WorstQuality2 |
True |
|
Historical Access |
Historical Access Client Read Aggregates |
False |
Table 143 describes the details of the Historical Annotation Client Facet. This Facet defines the ability to retrieve and write annotations for historical data.
Table 143 – Historical Annotation Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Access Client Facet |
False |
|
|
Historical Data Update Client Facet |
False |
|
|
Historical Access |
Historical Access Client Annotations |
False |
Table 144 describes the details of the Historical Access Modified Data Client Facet. This Facet defines the ability to access prior historical data (values that were modified or inserted).
Table 144 – Historical Access Modified Data Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Access Client Facet |
False |
|
|
Historical Access |
Historical Access Client Read Modified |
False |
Table 145 describes the details of the Historical Data Insert Client Facet. This Facet defines the ability to insert historical data.
Table 145 – Historical Data Insert Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Historical Access |
Historical Access Client Data Insert |
False |
Table 146 describes the details of the Historical Data Update Client Facet. This Facet defines the ability to update historical data.
Table 146 – Historical Data Update Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Historical Access |
Historical Access Client Data Update |
False |
Table 147 describes the details of the Historical Data Replace Client Facet. This Facet defines the ability to replace historical data.
Table 147 – Historical Data Replace Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Historical Access |
Historical Access Client Data Replace |
False |
Table 148 describes the details of the Historical Data Delete Client Facet. This Facet defines the ability to delete historical data.
Table 148 – Historical Data Delete Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Historical Access |
Historical Access Client Data Delete |
False |
Table 149 describes the details of the Historical Access Client Server Timestamp Facet. This Facet defines the ability to request and process Server timestamps, in addition to source timestamps.
Table 149 – Historical Access Client Server Timestamp Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Access |
False |
Table 150 describes the details of the Historical Structured Data Access Client Facet. This Facet defines the ability to read structured values for historical nodes.
Table 150 – Historical Structured Data Access Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Access Client Facet |
False |
|
|
Historical Access |
Historical Access Client Structure Data Raw |
False |
Table 151 describes the details of the Historical Structured Data AtTime Client Facet. This Facet defines the ability to read structured values for historical nodes at specific instances in time.
Table 151 – Historical Structured Data AtTime Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Data AtTime Client Facet |
False |
|
|
Historical Access |
Historical Access Client Structure Data Time Instance |
False |
Table 152 describes the details of the Historical Structured Data Modified Client Facet. This Facet defines the ability to read structured values for prior historical data (values that were modified or inserted).
Table 152 – Historical Structured Data Modified Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Access Modified Data Client Facet |
False |
|
|
Historical Access |
Historical Access Client Structure Data Read Modified |
False |
Table 153 describes the details of the Historical Structured Data Insert Client Facet. This Facet defines the ability to insert structured historical data.
Table 153 – Historical Structured Data Insert Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Data Insert Client Facet |
False |
|
|
Historical Access |
Historical Access Client Structure Data Insert |
False |
Table 154 describes the details of the Historical Structured Data Update Client Facet. This Facet defines the ability to update structured historical data.
Table 154 – Historical Structured Data Update Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Data Update Client Facet |
False |
|
|
Historical Access |
Historical Access Client Structure Data Update |
False |
Table 155 describes the details of the Historical Structured Data Replace Client Facet. This Facet defines the ability to replace structured historical data.
Table 155 – Historical Structured Data Replace Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Data Replace Client Facet |
False |
|
|
Historical Access |
Historical Access Client Structure Data Replace |
False |
Table 156 describes the details of the Historical Structured Data Delete Client Facet. This Facet defines the ability to remove structured historical data.
Table 156 – Historical Structured Data Delete Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Historical Data Delete Client Facet |
False |
|
|
Historical Access |
Historical Access Client Structure Data Delete |
False |
Table 157 describes the details of the Historical Events Client Facet. This Facet defines the ability to read Historical Events, including simple filtering.
Table 157 – Historical Events Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Historical Access |
Historical Access Client Read Events |
False |
Table 158 describes the details of the Historical Event Insert Client Facet. This Facet defines the ability to insert historical events.
Table 158 – Historical Event Insert Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Historical Access |
False |
Table 159 describes the details of the Historical Event Update Client Facet. This Facet defines the ability to update historical events.
Table 159 – Historical Event Update Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Historical Access |
False |
Table 160 describes the details of the Historical Event Replace Client Facet. This Facet defines the ability to replace historical events.
Table 160 – Historical Event Replace Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Historical Access |
False |
Table 161 describes the details of the Historical Event Delete Client Facet. This Facet defines the ability to delete Historical events.
Table 161 – Historical Event Delete Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
False |
||
|
Historical Access |
False |
Table 162 describes the details of the Aggregate Subscriber Client Facet. This Facet defines the ability to use the aggregate filter when subscribing for Attribute values.
Table 162 – Aggregate Subscriber Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Aggregates |
Aggregate Subscription – Client AnnotationCount |
True |
|
Aggregates |
Aggregate Subscription – Client Average |
True |
|
Aggregates |
Aggregate Subscription – Client Count |
True |
|
Aggregates |
Aggregate Subscription – Client Custom Aggregates |
True |
|
Aggregates |
Aggregate Subscription – Client Delta |
True |
|
Aggregates |
Aggregate Subscription – Client DeltaBounds |
True |
|
Aggregates |
Aggregate Subscription – Client DurationBad |
True |
|
Aggregates |
Aggregate Subscription – Client DurationGood |
True |
|
Aggregates |
Aggregate Subscription – Client DurationInStateNonZero |
True |
|
Aggregates |
Aggregate Subscription – Client DurationInStateZero |
True |
|
Aggregates |
Aggregate Subscription – Client End |
True |
|
Aggregates |
Aggregate Subscription – Client EndBound |
True |
|
Aggregates |
Aggregate Subscription – Client Filter |
False |
|
Aggregates |
Aggregate Subscription – Client Interpolative |
True |
|
Aggregates |
Aggregate Subscription – Client Maximum |
True |
|
Aggregates |
Aggregate Subscription – Client Maximum2 |
True |
|
Aggregates |
Aggregate Subscription – Client MaximumActualTime |
True |
|
Aggregates |
Aggregate Subscription – Client MaximumActualTime2 |
True |
|
Aggregates |
Aggregate Subscription – Client Minimum |
True |
|
Aggregates |
Aggregate Subscription – Client Minimum2 |
True |
|
Aggregates |
Aggregate Subscription – Client MinimumActualTime |
True |
|
Aggregates |
Aggregate Subscription – Client MinimumActualTime2 |
True |
|
Aggregates |
Aggregate Subscription – Client NumberOfTransitions |
True |
|
Aggregates |
Aggregate Subscription – Client PercentBad |
True |
|
Aggregates |
Aggregate Subscription – Client PercentGood |
True |
|
Aggregates |
Aggregate Subscription – Client Range |
True |
|
Aggregates |
Aggregate Subscription – Client Range2 |
True |
|
Aggregates |
Aggregate Subscription – Client StandardDeviationPopulation |
True |
|
Aggregates |
Aggregate Subscription – Client StandardDeviationSample |
True |
|
Aggregates |
Aggregate Subscription – Client Start |
True |
|
Aggregates |
Aggregate Subscription – Client StartBound |
True |
|
Aggregates |
Aggregate Subscription – Client TimeAverage |
True |
|
Aggregates |
Aggregate Subscription – Client TimeAverage2 |
True |
|
Aggregates |
Aggregate Subscription – Client Total |
True |
|
Aggregates |
Aggregate Subscription – Client Total2 |
True |
|
Aggregates |
Aggregate Subscription – Client VariancePopulation |
True |
|
Aggregates |
Aggregate Subscription – Client VarianceSample |
True |
|
Aggregates |
Aggregate Subscription – Client WorstQuality |
True |
|
Aggregates |
Aggregate Subscription – Client WorstQuality2 |
True |
|
Monitored Item Services |
Monitor Client Aggregate Filter |
False |
|
Monitored Item Services |
Monitor Client by Index |
False |
|
Monitored Item Services |
Monitor Client Modify |
True |
|
Monitored Item Services |
Monitor Client Value Change |
False |
|
Subscription Client Basic |
False |
|
|
Subscription Client Modify |
True |
|
|
Subscription Client Multiple |
True |
|
|
Subscription Client Republish |
True |
Table 163 describes the details of the Standard UA Client Profile. This Profile is a FullFeatured Profile that defines a minimum set of functionality required for generic OPC UA Clients. Such a Client shall be able to use local, subnet and global discovery. It shall be able to maintain a connection with a single Session (as required for nano embedded Servers). If Subscriptions are used, the Client shall respect the limits of Servers with limited resources. If a Server does not support Subscriptions, the Client shall provide read access as fallback. The Client must provide connection establishment through the OPC UA TCP binary protocol with and without security.
Table 163 – Standard UA Client Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
AddressSpace Lookup Client Facet |
False |
|
|
False |
||
|
False |
||
|
Base Client Behaviour Facet |
False |
|
|
Core Client Facet |
False |
|
|
DataChange Subscriber Client Facet |
False |
|
|
False |
||
|
Entry Level Support 2015 Client Facet |
False |
|
|
Global Certificate Management Client Facet |
False |
|
|
False |
||
|
False |
||
|
SecurityPolicy [B] – Basic256Sha256 |
False |
|
|
SecurityPolicy – Basic256 |
False |
|
|
False |
||
|
UA-TCP UA-SC UA-Binary |
False |
|
|
User Token – Anonymous Facet |
False |
Table 164 describes the details of the Standard UA Client 2017 Profile. This Profile is a FullFeatured Profile that defines a minimum set of functionality required for generic OPC UA Clients. Such a Client shall be able to use local, subnet and global discovery. It shall be able to maintain a connection with a single Session (as required for nano embedded Servers). If Subscriptions are used, the Client shall respect the limits of Servers with limited resources. If a Server does not support Subscriptions, the Client shall provide read access as fallback. The Client must provide connection establishment through the OPC UA TCP binary protocol with and without security.This Profile supersedes the “Standard UA Client Profile”
Table 164 – Standard UA Client 2017 Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
AddressSpace Lookup Client Facet |
False |
|
|
False |
||
|
False |
||
|
Base Client Behaviour Facet |
False |
|
|
Core 2017 Client Facet |
False |
|
|
DataChange Subscriber Client Facet |
False |
|
|
False |
||
|
Entry Level Support 2015 Client Facet |
False |
|
|
Global Certificate Management Client Facet |
False |
|
|
False |
||
|
False |
||
|
False |
||
|
UA-TCP UA-SC UA-Binary |
False |
|
|
User Token – Anonymous Facet |
False |
Table 165 describes the details of the UA-TCP UA-SC UA-Binary. This transport Facet defines a combination of network protocol, security protocol and message encoding that is optimized for low resource consumption and high performance. It combines the simple TCP based network protocol UA-TCP 1.0 with the binary security protocol UA-SecureConversation 1.0 and the binary message encoding UA-Binary 1.0.
Table 165 – UA-TCP UA-SC UA-Binary
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Protocol and Encoding |
Protocol UA TCP |
False |
|
Protocol and Encoding |
UA Binary Encoding |
False |
|
Protocol and Encoding |
UA Secure Conversation |
False |
Table 166 describes the details of the HTTPS UA-Binary. This transport Facet defines a combination of network protocol, security protocol and message encoding that balances compatibility with widely used HTTPS transport and a compact UA-Binary encoded message for added performance. It is expected that this transport will be used to support installations where firewalls only permit HTTPS or where a WEB browser is used as Client. This transport requires that one of the TransportSecurity Profiles for TLS be provided.
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Protocol and Encoding |
Protocol HTTPS |
False |
|
Protocol and Encoding |
UA Binary Encoding |
False |
|
Security |
Security TLS General |
False |
Table 167 describes the details of the HTTPS UA-XML. This transport Facet defines a combination of network protocol, security protocol and message encoding that uses HTTPS transport and a SOAP XML encoded message for use with standard SOAP V1.2 toolkits. This transport requires that one of the TransportSecurity Profiles for TLS be provided.
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Protocol and Encoding |
Protocol HTTPS |
False |
|
Protocol and Encoding |
UA SOAP-XML Encoding |
False |
|
Security |
Security TLS General |
False |
Table 168 describes the details of the HTTPS UA-JSON. This transport Facet defines a combination of network protocol, security protocol and message encoding that uses HTTPS transport and a UA-JSON encoded message. This transport requires that one of the TransportSecurity Profiles for TLS be provided.
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Protocol and Encoding |
JSON Reversible Encoding |
False |
|
Protocol and Encoding |
Protocol HTTPS |
False |
|
Security |
Security TLS General |
False |
Table 169 describes the details of the WSS UA-SC UA-Binary. This transport Facet defines a combination of network protocol, security protocol and message encoding that uses WSS transport as a tunnel for UA-SecureConversation and UA-Binary encoded messages. Although transport security is available in WSS via TLS, additional message security can be used to assure end-to-end security.
Table 169 – WSS UA-SC UA-Binary
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Protocol and Encoding |
Protocol Web Sockets |
False |
|
Protocol and Encoding |
UA Binary Encoding |
False |
|
Protocol and Encoding |
UA Secure Conversation |
False |
|
Security |
Security TLS General |
False |
Table 170 describes the details of the WSS UA-JSON. This transport Facet defines a combination of network protocol, security protocol and message encoding that uses WSS transport with UA-JSON encoded messages.
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Protocol and Encoding |
JSON Reversible Encoding |
False |
|
Protocol and Encoding |
Protocol Web Sockets |
False |
|
Security |
Security TLS General |
False |
Table 171 describes the details of the Security User Access Control Full. A Server that supports this profile supports restricting multiple levels of access to all Nodes in the AddressSpace based on the validated user.
Table 171 – Security User Access Control Full
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security User Access Control Base |
False |
|
|
Address Space Model |
Address Space User Access Level Full |
False |
Table 172 describes the details of the Security User Access Control Base. A Server that supports this profile supports restricting some level of access to some Nodes in the AddressSpace based on the validated user.
Table 172 – Security User Access Control Base
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Address Space Model |
Address Space User Access Level Base |
False |
|
Security |
Security User IssuedToken Kerberos |
True |
|
Security |
Security User IssuedToken Kerberos Windows |
True |
|
Security |
Security User Name Password |
False |
|
Security |
Security User X509 |
True |
Table 173 describes the details of the Security Time Synchronization. This Facet indicates that the application supports the minimum required level of time synchronization to ensure secure communication. One of the optional time synchronization conformance units must be supported.
Table 173 – Security Time Synchronization
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security Time Synch – Configuration |
False |
|
Security |
Security Time Synch – NTP / OS Based support |
True |
|
Security |
Security Time Synch – UA based support |
True |
Table 174 describes the details of the Best Practice – Audit Events. Subscriptions for Audit Events shall be restricted to authorized personnel.
Table 174 – Best Practice – Audit Events
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Miscellaneous |
Best Practice – Audit Events |
False |
Table 175 describes the details of the Best Practice – Alarm Handling. A Server should restrict critical alarm handling functionality to users that have the appropriate rights to perform these actions.
Table 175 – Best Practice – Alarm Handling
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Miscellaneous |
Best Practice – Alarm Handling |
False |
Table 176 describes the details of the Best Practice – Random Numbers. All random numbers that are required for security should use appropriate cryptographic library based random number generators.
Table 176 – Best Practice – Random Numbers
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Miscellaneous |
Best Practice – Random Numbers |
False |
Table 177 describes the details of the Best Practice – Timeouts. The administrator should be able to configure reasonable timeouts for Secure Channels, Sessions and Subscriptions. Setting these timeouts allows limiting Denial of Service attacks and overload issues.
Table 177 – Best Practice – Timeouts
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Miscellaneous |
Best Practice – Timeouts |
False |
Table 178 describes the details of the Best Practice – Administrative Access. The Server and Client allow restricting the use of certain Services and access to parts of the AddressSpace to administrative personnel. This includes multiple level of administrative access on platforms that support multiple administrative roles (such as Windows or Linux).
Table 178 – Best Practice – Administrative Access
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Miscellaneous |
Best Practice – Administrative Access |
False |
Table 179 describes the details of the Best Practice – Strict Message Handling. Server and Client reject messages that are incorrectly formed as specified in Part 4 and Part 6.
Table 179 – Best Practice – Strict Message Handling
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Miscellaneous |
Best Practice – Strict Message Handling |
False |
Table 180 describes the details of the Best Practice – Audit Events Client. Audit Tracking system connect to a Server using a Secure Channel and under the appropriate authorization to allow access to Audit Events.
Table 180 – Best Practice – Audit Events Client
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Miscellaneous |
Best Practice – Audit Events Client |
False |
Table 181 describes the details of the TransportSecurity – TLS 1.2. This Facet defines a transport security for configurations with high security needs. It makes use of TLS 1.2 and uses TLS_RSA_WITH_AES_256_CBC_SHA256. As computing power increases, security algorithms are expected to expire. NIST provides guidelines for expected expiration dates for individual algorithms. These guidelines provide recommended dates at which the algorithm should be replaced or upgraded to a more secure algorithm. They do not indicate a failure of the algorithm. NIST has no recommendations for this TransportSecurity. It is recommended that Servers and Clients support all security profiles and developers provide the recommended profile as a default. It is up to an administrator to configure the actual exposed TransportSecurity Profiles.
Table 181 – TransportSecurity – TLS 1.2
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security TLS_RSA with AES_256_CBC_SHA256 |
False |
Table 182 describes the details of the TransportSecurity – TLS 1.2 with PFS. This Facet defines a transport security for configurations with high security needs and perfect forward secrecy (PFS). It makes use of TLS 1.2 and uses TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 or TLS_DHE_RSA_WITH_AES_256_CBC_SHA256. As computing power increases, security algorithms are expected to expire. NIST provides guidelines for expected expiration dates for individual algorithms. These guidelines provide recommended dates at which the algorithm should be replaced or upgraded to a more secure algorithm. They do not indicate a failure of the algorithm. NIST has no recommendations for this TransportSecurity. It is recommended that Servers and Clients support all security profiles and developers provide the recommended profile as a default. It is up to an administrator to configure the actual exposed TransportSecurity Profiles.
Table 182 – TransportSecurity – TLS 1.2 with PFS
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security TLS_DHE_RSA with AES_nnn_CBC_SHA256 |
False |
Table 183 describes the details of the SecurityPolicy – None. This security Facet defines a security policy used for configurations with the lowest security needs. This security policy can affect the behaviour of the CreateSession and ActivateSession Services. It also results in a SecureChannel which has no channel security. By default this security policy should be disabled if any other security policies are available.
Table 183 – SecurityPolicy – None
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
AsymmetricEncryptionAlgorithm_None |
False |
|
Security |
AsymmetricSignatureAlgorithm_None |
False |
|
Security |
KeyDerivationAlgorithm_None |
False |
|
Security |
Security None CreateSession ActivateSession |
False |
|
Security |
Security None CreateSession ActivateSession 1.0 |
True |
|
Security |
SecurtyPolicy_None_Limits |
False |
|
Security |
SymmetricEncryptionAlgorithm_None |
False |
|
Security |
SymmetricSignatureAlgorithm_None |
False |
SecurityPolicy – Basic128Rsa15 has been deprecated in v1.04 since the hash algorithm Sha-1 is not considered secure anymore.
SecurityPolicy – Basic128Rsa15 has been deprecated in v1.04 since the hash algorithm Sha-1 is not considered secure anymore.
Table 184 describes the details of the SecurityPolicy [A] - Aes128-Sha256-RsaOaep. This security Facet defines a security policy for configurations with average security needs. It requires a PKI infrastructure. As computing power increases, security policies are expected to expire. NIST provides guidelines for expected expiration dates for individual algorithms. These guidelines provide recommended dates at which the algorithm should be replaced or upgraded to a more secure algorithm. They do not indicate a failure of the algorithm. This security policy has no published end dates as of this time. It is recommended that Servers and Clients support all security profiles and support configurability of actual exposed and default security policies.
Table 184 – SecurityPolicy [A] - Aes128-Sha256-RsaOaep
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Aes128-Sha256-RsaOaep_Limits |
False |
|
Security |
AsymmetricEncryptionAlgorithm_RSA-OAEP-SHA1 |
False |
|
Security |
AsymmetricSignatureAlgorithm_RSA-PKCS15-SHA2-256 |
False |
|
Security |
CertificateSignatureAlgorithm_RSA-PKCS15-SHA2-256 |
False |
|
Security |
KeyDerivationAlgorithm_P-SHA2-256 |
False |
|
Security |
Security Certificate Validation |
False |
|
Security |
Security Encryption Required |
False |
|
Security |
Security Signing Required |
False |
|
Security |
SymmetricEncryptionAlgorithm_AES128-CBC |
False |
|
Security |
SymmetricSignatureAlgorithm_HMAC-SHA2-256 |
False |
Table 185 describes the details of the SecurityPolicy [B] – Basic256Sha256. This security Facet defines a security policy for configurations with high security needs. It requires a PKI infrastructure.As computing power increases, security policies are expected to expire. NIST provides guidelines for expected expiration dates for individual algorithms. These guidelines provided recommended dates at which the algorithm should be replaced or upgraded to a more secure algorithm. They do not indicate a failure of the algorithm. This security policy has no published end dates as of this time. It is recommended that Servers and Clients support all security profiles and developers provide the recommended profile as a default. It is up to an administrator to configure the actual exposed security policies.
Table 185 – SecurityPolicy [B] – Basic256Sha256
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
AsymmetricEncryptionAlgorithm_RSA-OAEP-SHA1 |
False |
|
Security |
AsymmetricSignatureAlgorithm_RSA-PKCS15-SHA2-256 |
False |
|
Security |
Basic256Sha256_Limits |
False |
|
Security |
CertificateSignatureAlgorithm_RSA-PKCS15-SHA2-256 |
False |
|
Security |
KeyDerivationAlgorithm_P-SHA2-256 |
False |
|
Security |
Security Certificate Validation |
False |
|
Security |
Security Encryption Required |
False |
|
Security |
Security Signing Required |
False |
|
Security |
SymmetricEncryptionAlgorithm_AES256-CBC |
False |
|
Security |
SymmetricSignatureAlgorithm_HMAC-SHA2-256 |
False |
Table 186 describes the details of the SecurityPolicy - Aes256-Sha256-RsaPss. This security Facet defines a security policy for configurations with a need for high security. It requires a PKI infrastructure. As computing power increases, security policies are expected to expire. NIST provides guidelines for expected expiration dates for individual algorithms. These guidelines provide recommended dates at which the algorithm should be replaced or upgraded to a more secure algorithm. They do not indicate a failure of the algorithm. This security policy has no published end dates as of this time. It is recommended that Servers and Clients support all security profiles and support configurability of actual exposed and default security policies.
Table 186 – SecurityPolicy - Aes256-Sha256-RsaPss
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Aes256-Sha256-RsaPss_Limits |
False |
|
Security |
AsymmetricEncryptionAlgorithm_RSA-OAEP-SHA2-256 |
False |
|
Security |
AsymmetricSignatureAlgorithm_RSA-PSS -SHA2-256 |
False |
|
Security |
CertificateSignatureAlgorithm_ RSA-PKCS15-SHA2-256 |
False |
|
Security |
KeyDerivationAlgorithm_P-SHA2-256 |
False |
|
Security |
Security Certificate Validation |
False |
|
Security |
Security Encryption Required |
False |
|
Security |
Security Signing Required |
False |
|
Security |
SymmetricEncryptionAlgorithm_AES256-CBC |
False |
|
Security |
SymmetricSignatureAlgorithm_HMAC-SHA2-256 |
False |
Table 187 describes the details of the User Token – Anonymous Facet. This Facet indicates that anonymous User Tokens are supported.
Table 187 – User Token – Anonymous Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security User Anonymous |
False |
Table 188 describes the details of the User Token – User Name Password Server Facet. This Facet indicates that a user token that is comprised of a username and password is supported. This user token can affect the behaviour of the ActivateSession Service.
Table 188 – User Token – User Name Password Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security Invalid user token |
False |
|
Security |
Security User Name Password |
False |
Table 189 describes the details of the User Token – X509 Certificate Server Facet. This Facet indicates that the use of an X509 certificates to identify users is supported.
Table 189 – User Token – X509 Certificate Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security Invalid user token |
False |
|
Security |
Security User X509 |
False |
Table 190 describes the details of the User Token – Issued Token Server Facet. This Facet indicates that a User Token that is comprised of an issued token is supported.
Table 190 – User Token – Issued Token Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security Invalid user token |
False |
|
Security |
Security User IssuedToken Kerberos |
False |
Table 191 describes the details of the User Token – Issued Token Windows Server Facet. This Facet further refines the User Token - Issued Token to indicate a windows implementation of Kerberos
Table 191 – User Token – Issued Token Windows Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
User Token – Issued Token Server Facet |
False |
|
|
Security |
Security User IssuedToken Kerberos Windows |
False |
Table 192 describes the details of the User Token – JWT Server Facet. This Facet defines support for JSON Web Tokens (JWT) to identify the user during Session setup. A JWT is the Access Token format which OPC UA requires when using OAuth2.
Table 192 – User Token – JWT Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
||
|
Security |
Azure Identity Provider Authority Profile |
True |
||
|
Security |
OAuth2 Authority Profile |
True |
||
|
Security |
OPC UA Authority Profile |
True |
||
|
Security |
Security Invalid user token |
False |
||
|
Security |
Security User JWT IssuedToken |
False |
||
|
Security |
Security User JWT Token Policy |
False |
||
Table 193 describes the details of the User Token – User Name Password Client Facet. This Facet defines the ability to use a user token that is comprised of a username and password.
Table 193 – User Token – User Name Password Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security User Name Password Client |
False |
Table 194 describes the details of the User Token – X509 Certificate Client Facet. This Facet defines the ability to use an X509 certificates to identify users.
Table 194 – User Token – X509 Certificate Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security User X509 Client |
False |
Table 195 describes the details of the User Token – Issued Token Client Facet. This Facet defines the ability to use the User Token - Issued Token (Kerberos) to connect to a Server.
Table 195 – User Token – Issued Token Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security User IssuedToken Kerberos Client |
False |
Table 196 describes the details of the User Token – Issued Token Windows Client Facet. This Facet defines the ability to use the User Token - Issued Token (Windows implementation of Kerberos) to connect to a Server
Table 196 – User Token – Issued Token Windows Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Security |
Security User IssuedToken Kerberos Windows Client |
False |
Table 197 describes the details of the User Token – JWT Client Facet. This Facet defines the ability to use JSON Web Tokens (JWT) as user identification during Session setup. JWTs are used to request an access token from an external Authorization Service.
Table 197 – User Token – JWT Client Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
||
|
Security |
Azure Identity Provider Authority Profile |
True |
||
|
Security |
OAuth2 Authority Profile |
True |
||
|
Security |
OPC UA Authority Profile |
True |
||
|
Security |
Security User JWT IssuedToken Client |
False |
||
|
Security |
Security User JWT Token Policy Client |
False |
||
Table 198 describes the details of the Global Discovery Server Profile. This Profile is a FullFeatured Profile that covers the necessary Services and Information Model of a UA Server that acts as a GDS.
Table 198 – Global Discovery Server Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Core Server Facet |
False |
|
|
False |
||
|
SecurityPolicy – Basic128Rsa15 |
False |
|
|
SecurityPolicy – Basic256 |
False |
|
|
Standard DataChange Subscription Server Facet |
False |
|
|
UA-TCP UA-SC UA-Binary |
False |
|
|
User Token – X509 Certificate Server Facet |
False |
|
|
GDS |
GDS Application Directory |
False |
|
GDS |
GDS LDS-ME Connectivity |
False |
|
Security |
Security Default ApplicationInstance Certificate |
False |
|
Session Minimum 50 Parallel |
False |
Table 199 describes the details of the Global Discovery Server 2017 Profile. This Profile is a FullFeatured Profile that covers the necessary Services and Information Model of a UA Server that acts as a GDS.This Profile supersedes the “Global Discovery Server Profile”.
Table 199 – Global Discovery Server 2017 Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Core 2017 Server Facet |
False |
|
|
False |
||
|
Standard DataChange Subscription 2017 Server Facet |
False |
|
|
UA-TCP UA-SC UA-Binary |
False |
|
|
GDS |
GDS Application Directory |
False |
|
GDS |
GDS LDS-ME Connectivity |
False |
|
GDS |
GDS Query Applications |
False |
|
Security |
Security Default ApplicationInstance Certificate |
False |
|
Security |
Security Policy Required |
False |
|
Session Minimum 50 Parallel |
False |
Table 200 describes the details of the Global Discovery and Certificate Management Server. This Profile is a FullFeatured Profile that covers the necessary Services and Information Model of a UA Server that acts as a GDS and a global Certificate Manager.
Table 200 – Global Discovery and Certificate Management Server
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Auditing Server Facet |
False |
|
|
File Access Server Facet |
False |
|
|
False |
||
|
SecurityPolicy [B] – Basic256Sha256 |
False |
|
|
Standard Event Subscription Server Facet |
False |
|
|
GDS |
GDS Certificate Manager Pull Model |
False |
|
GDS |
GDS Certificate Manager Push Model |
False |
Table 201 describes the details of the Global Discovery and Certificate Mgmt 2017 Server. This Profile is a FullFeatured Profile that covers the necessary Services and Information Model of a UA Server that acts as a GDS and a global Certificate Manager.This Profile supersedes the “Global Discovery and Certificate Management Server”.
Table 201 – Global Discovery and Certificate Mgmt 2017 Server
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Auditing Server Facet |
False |
|
|
File Access Server Facet |
False |
|
|
False |
||
|
Standard Event Subscription Server Facet |
False |
|
|
GDS |
GDS Certificate Manager Pull Model |
False |
Table 202 describes the details of the Global Certificate Management Client Profile. This Profile is a FullFeatured Profile that uses the Push Model for the management of Certificates and Trust Lists.
Table 202 – Global Certificate Management Client Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Core Client Facet |
False |
|
|
False |
||
|
Entry Level Support 2015 Client Facet |
False |
|
|
File Access Client Facet |
False |
|
|
False |
||
|
SecurityPolicy [B] – Basic256Sha256 |
False |
|
|
SecurityPolicy – Basic256 |
False |
|
|
UA-TCP UA-SC UA-Binary |
False |
|
|
GDS |
GDS Certificate Manager Push Model |
False |
|
Security |
Security Default ApplicationInstance Certificate |
False |
Table 203 describes the details of the Global Certificate Management Client 2017 Profile. This Profile is a FullFeatured Profile that uses the Push Model for the management of Certificates and Trust Lists.This Profile supersedes the “Global Certificate Management Client Profile”.
Table 203 – Global Certificate Management Client 2017 Profile
|
Group |
Conformance Unit / Profile Title |
Optional |
|
Core 2017 Client Facet |
False |
|
|
False |
||
|
Entry Level Support 2015 Client Facet |
False |
|
|
File Access Client Facet |
False |
|
|
False |
||
|
UA-TCP UA-SC UA-Binary |
False |
|
|
GDS |
GDS Certificate Manager Push Model |
False |
|
Security |
Security Default ApplicationInstance Certificate |
False |
Table 204 describes the details of the Global Service Authorization Request Server Facet. This Facet defines the capability of a Server (like a GDS) to provide access tokes to OPC UA Clients via an Authorization Service as defined in UA Part 12.
Table 204 – Global Service Authorization Request Server Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
GDS |
False |
Table 205 describes the details of the Global Service KeyCredential Pull Facet. This Facet requires providing the Information Model for Pull Management as defined in UA Part 12. For example KeyCredentials are needed to access an Authorization Service or a Broker. OPC UA Clients use this Information Model to request and update KeyCredentials they need.
Table 205 – Global Service KeyCredential Pull Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
GDS |
GDS Key Credential Service Pull Model |
False |
Table 206 describes the details of the Global Service KeyCredential Push Facet. This Facet requires the use of KeyCredential Push Management functions to set or update credentials in an OPC UA Server. For example KeyCredentials are needed to access an Authorization Service or a Broker. This OPC UA Server in turn has to provide the KeyCredentialConfigurationType Objects that represent required credentials.
Table 206 – Global Service KeyCredential Push Facet
|
Group |
Conformance Unit / Profile Title |
Optional |
|
GDS |
GDS Key Credential Service Push Model |
False |
______________