PullManagement is performed by using the CertificateManager information model, in particular the Methods defined in 7.9. The interactions between Application and CertificateManager during PullManagement are illustrated in Figure 13.
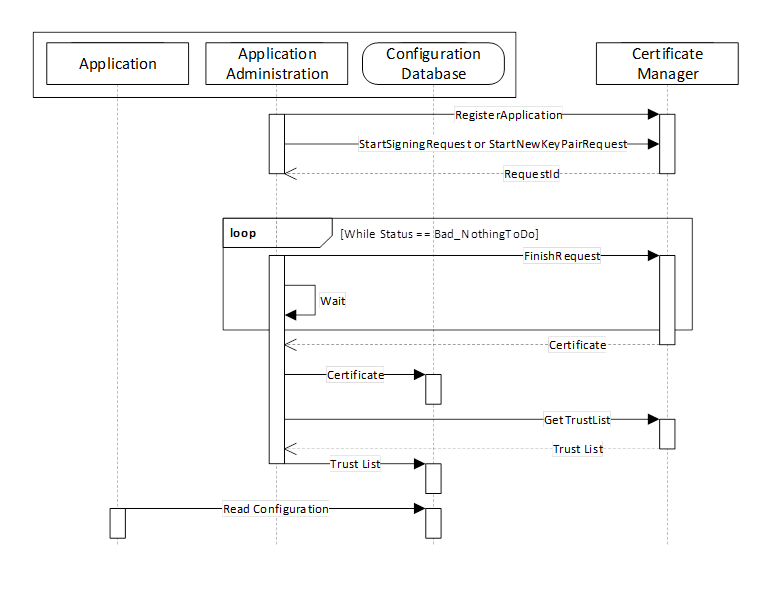
Figure 13 – The Pull Management Model for Certificates
The Application Administration component may be part of the Client or Server or a standalone utility that understands how the application persists its configuration information in its Configuration Database.
A similar process is used to renew certificates or to periodically update TrustList.
Security in PullManagement requires an encrypted channel and authorized credentials. These credentials may be user credentials for a CertificateAuthorityAdmin or application credentials determined by the Certificate used to create the SecureChannel. Examples of the application credentials include Certificates previously issued to the application being accessed, Device Certificates issued by the Registrar defined in OPC 10000-21 or Certificates issued to an application with access to the ApplicationAdmin Privilege (see 6.2).
The CertificateManager shall ensure that any application with a Certificate issued by the CertificateManager may connect securely to the CertificateManager using that Certificate (i.e. all CAs and CRLs needed to verify a Certificate are added to the CertificateManager’s TrustList).
Before a Client provides any secrets associated with credentials to a CertificateManager it needs to know that it can trust the CertificateManager. This can be done by an administrator that adds the CertificateManager to the Client TrustList before the Client attempts to connect to the CertificateManager. If the Client finds a CertificateManager on a network via mDNS or other insecure mechanism it could trust the CertificateManager if it has some independently acquired information that allows it to trust the CertificateManager. For example, the DNS address of the CertificateManager could be provided by a trusted authority and this address appears in the Certificate of the CertificateManager being used and the address was used to connect.
Once the Client finds a CertificateManager that it can trust, it needs to provide credentials that allows the CertificateManager to know that it can issue Certificates. The Certificate used by the Client can be the credential if there is an out of band process to provide the Certificate to the CertificateManager. The CertificateManager could provide a one-time password to the Client via email or other mechanisms.
The CertificateManager can only issue Certificates to authenticated Clients. There are a number of ways to authenticate Clients:
- The CertificateManager is pre-configured with information about the Client Certificate that allows the CertificateManager to know that the Client can request Certificates even if anonymous user credentials are used. The Client may be a DCA authenticated by a Registrar (see OPC 10000-21), a Client with a previously issued Certificate, or a Client authorized to create Certificates on behalf of other applications.
- The CertificateManager may have a manual process where an administrator reviews each request before issuing a Certificate.
- The Client provides user credentials. A Client shall not provide a secret (e.g. a password) to an untrusted CertificateManager.