KeyCredential management functions allow the management and distribution of KeyCredentials which OPC UA Applications use to access AuthorizationServices and/or Brokers. An application that provides the KeyCredential management functions is called a KeyCredentialService and is typically combined with the GDS into a single application.
There are two primary models for KeyCredential management: pull and PushManagement. In PullManagement, the application acts as a Client and uses the Methods on the KeyCredentialService to request and update KeyCredentials. The application is responsible for ensuring the KeyCredentials are kept up to date. In PushManagement the application acts as a Server and exposes Methods which the KeyCredentialService can call to update the KeyCredentials as required.
A KeyCredentialService can directly manage the KeyCredentials it supplies or it may act as an intermediary between a Client and a system that does not support OPC UA such as Azure AD or LDAP.
Note that KeyCredentials are secrets that are directly passed to AuthorizationServices and/or Brokers and are not Certificates with private keys. Certificate distribution is managed by the Certificate management model described in 7. For example, AuthorizationServices that support OAuth2 often require the client to provide a client_id and client_secret parameter with any request. The KeyCredentials are the values that the application shall place in these parameters.
KeyCredentialServices restrict access to many of the features they provide. These restrictions are described either by referring to well-known Roles which a Session must have access to or by referring to Privileges which are assigned to Sessions using mechanisms other than the well-known Roles. The well-known Roles used for a KeyCredentialService are listed in Table 80.
Table 80 – Well-known Roles for a KeyCredentialService
|
Name |
Description |
|
KeyCredentialAdmin |
This Role grants rights to request or revoke any KeyCredential. |
|
SecurityAdmin |
This Role grants the right to change the security configuration of a KeyCredentialService. |
The well-known Roles for Server managed by a KeyCredentialService are listed in Table 81.
Table 81 – Well-known Roles for Server managed by a KeyCredentialService
|
Name |
Description |
|
SecurityAdmin |
For PushManagement, this Role grants the right to change the security configuration of a Server managed by a KeyCredentialService. |
The Privileges used for a KeyCredentialService are listed in Table 82.
Table 82 – Privileges for a KeyCredentialService
|
Name |
Description |
|
ApplicationSelfAdmin |
This Privilege grants an OPC UA Application the right to request its own KeyCredentials. The Certificate used to create the SecureChannel is used to determine the identity of the OPC UA Application. |
|
ApplicationAdmin |
This Privilege grants rights to request KeyCredentials for one or more OPC UA Applications. The Certificate used to create the SecureChannel is used to determine the identity of the OPC UA Application and the set of OPC UA Applications that it is authorized to manage. |
Pull management is performed by using a KeyCredentialManagement Object (see 8.5.4). It allows Clients to request credentials for AuthorizationServices or Brokers which are supported by the KeyCredentialService. The interactions between the Client and the KeyCredentialService during PullManagement are illustrated in Figure 23.
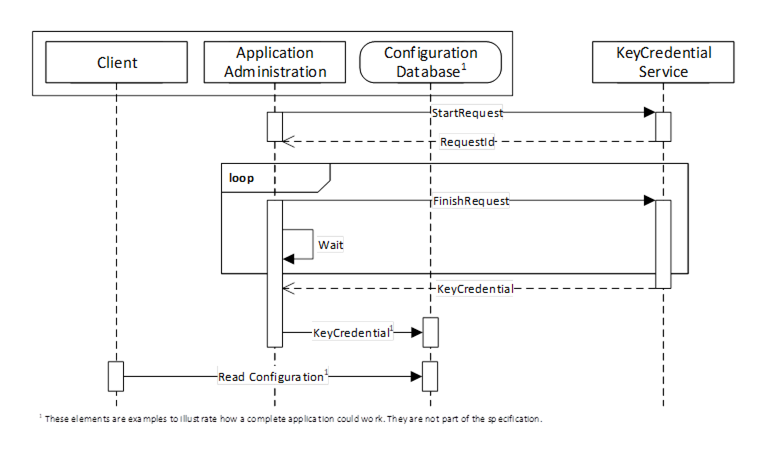
Figure 23 – The Pull Model for KeyCredential Management
The Application Administration component may be part of the Client or a standalone utility that understands how the Client persists its configuration information in its Configuration Database. The administration and database components are examples to illustrate how an application could be built and are not a requirement.
Requesting credentials is a two stage process because some KeyCredentialServices require a human to review and approve requests. The calls to the FinishRequest Method may not be periodic and could be initiated by events such as a user starting up the application or interacting with a UI element such as a button.
KeyCredentials shall only be returned to applications which are authorized by the KeyCredentialService.
Security in PullManagement requires an encrypted channel and Clients with access to the KeyCredentialAdmin Role, the ApplicationAdmin Priviledge or the ApplicationSelfAdmin Priviledge.
Push management is performed by using a KeyCredentialConfiguration Object (see 8.6.5) which is a component of the KeyCredentialConfigurationFolder Object which, in turn, is component of the ServerConfiguration Object in a Server. The interactions between the Administration application and the KeyCredentialService during PushManagement are illustrated in Figure 24.
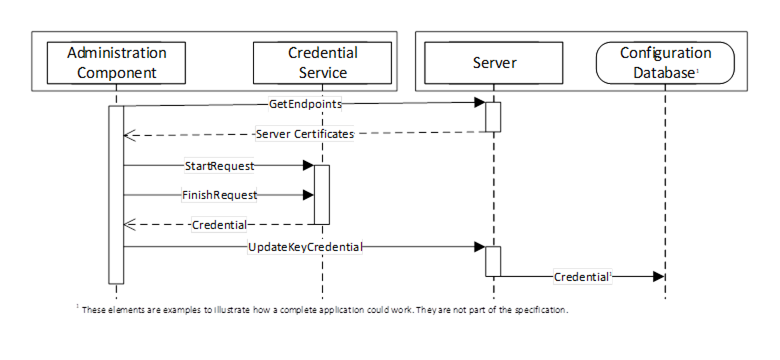
Figure 24 – The Push Model for KeyCredential Management
The Administration Component may use internal APIs to manage KeyCredentials or it could be a standalone utility that uses OPC UA to communicate with a Server which supports the pull model (see 8.3). The Configuration Database is used by the Server to persist its configuration information. The administration and database components are examples to illustrate how an application could be built and are not a requirement.
To ensure security of the KeyCredentials, the KeyCredentialService component can require that secrets be encrypted with a key only known to the intended recipient of the KeyCredentials. For this reason, the Administration Component uses the GetEndpoints Service to read the Certificate from the Server before initiating the credential request on behalf of the Server.
Security, when using the PushManagement model, requires an encrypted channel and Clients with acccess to the SecurityAdmin Role.
The AddressSpace used for PullManagement is shown in Figure 25. Clients interact with the Nodes defined in this model when they need to request or revoke KeyCredentials for themselves or for another application. The KeyCredentialManagement Folder is a well-known Object that appears in the AddressSpace of any Server which supports KeyCredential management.
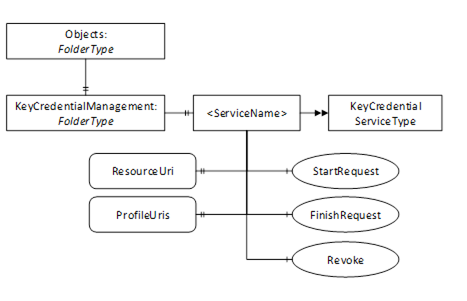
Figure 25 – The Address Space used for Pull KeyCredential Management
This ObjectType represents a Folder that contains KeyCredentialService Objects which may be accessed via the Server. It is defined in Table 83.
Table 83 – KeyCredentialManagementFolderType Definition
|
Attribute |
Value |
|||
|
BrowseName |
2:KeyCredentialManagementFolderType |
|||
|
IsAbstract |
False |
|||
|
References |
NodeClass |
BrowseName |
TypeDefinition |
Modelling Rule |
|
Subtype of the 0:FolderType defined in OPC 10000-5. |
||||
|
0:HasComponent |
Object |
2:<ServiceName> |
2:KeyCredentialServiceType |
OptionalPlaceholder |
|
|
||||
|
Conformance Units |
||||
|
GDS Key Credential Service Pull Model |
||||
This Object contains the KeyCredentialService Objects which may be accessed via the Server. It is the target of an Organizes reference from the Objects Folder defined in OPC 10000-5. It is defined in Table 84.
Table 84 – KeyCredentialManagement Object Definition
|
Attribute |
Value |
|||
|
BrowseName |
2:KeyCredentialManagement |
|||
|
TypeDefinition |
2:KeyCredentialManagementFolderType defined in 8.5.2. |
|||
|
References |
NodeClass |
BrowseName |
TypeDefinition |
Modelling Rule |
|
|
||||
|
Conformance Units |
||||
|
GDS Key Credential Service Pull Model |
||||
This ObjectType is the TypeDefinition for an Object that allows the management of KeyCredentials. It is defined in Table 85.
Table 85 – KeyCredentialServiceType Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:KeyCredentialServiceType |
||||
|
IsAbstract |
False |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
Subtype of the BaseObjectType defined in OPC 10000-5. |
|||||
|
0:HasProperty |
Variable |
2:ResourceUri |
0:String |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
2:ProfileUris |
0:String[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
2:SecurityPolicyUris |
0:String[] |
0:PropertyType |
Optional |
|
0:HasComponent |
Method |
2:StartRequest |
|
Defined in 8.5.5. |
Mandatory |
|
0:HasComponent |
Method |
2:FinishRequest |
|
Defined in 8.5.6. |
Mandatory |
|
0:HasComponent |
Method |
2:Revoke |
|
Defined in 8.5.7. |
Optional |
|
|
|||||
|
Conformance Units |
|||||
|
GDS Key Credential Service Pull Model |
|||||
The ResourceUri Property uniquely identifies the resource that accepts the KeyCredentials provided by the KeyCredentialService Object.
The ProfileUris Property specifies URIs assigned in OPC 10000-7 to the authentication mechanism used to communicate with the resource that accepts KeyCredentials provided by the Object. For example, it could specify that the resource returns JWTs using OAuth2 HTTP based APIs. As another example, it could specify an MQTT broker that expects a username/password.
The SecurityPolicyUris Property is the list of SecurityPolicies that may be used when encrypting the KeyCredentials. One of these URIs is passed in the StartRequest Method. If not present, The Server shall support all of the SecurityPoliciesUris returned by GetEndpoints,
The StartRequest Method is used to initiate a request for new KeyCredentials for an application. This request may complete immediately or it can require offline approval by an administrator.
The FinishRequest Method is used to complete a request created by calling StartRequest . If the KeyCredential is available it is returned. If request is not yet completed it returns Bad_NothingToDo.
The Revoke Method is used to revoke a previously issued KeyCredential.
StartRequest is used to request a new KeyCredential.
The KeyCredential secret may be encrypted with the public key of the Certificate supplied in the request. The SecurityPolicyUri specifies the security profile used for the encryption.
This Method shall be called from an encrypted SecureChannel and from a Client that has access to the KeyCredentialAdmin Role, the ApplicationAdmin Privilege, or the ApplicationSelfAdmin Privilege (see 8.2).
Signature
StartRequest (
[in] String applicationUri
[in] ByteString publicKey
[in] String securityPolicyUri
[in] NodeId[] requestedRoles
[out] NodeId requestId
);
|
Argument |
Description |
|
applicationUri |
The applicationUri of the application receiving the KeyCredentials. The request is rejected applicationUri does not uniquely identify an application known to the GDS (see 6.6.6). If the requestor is not the same as the application used to create the Secure Channel then a Certificate should be provided. |
|
publicKey |
A Public Key used to encrypt the returned KeyCredential secret. For RSA SecurityPolicies this is the DER encoded form of an X.509 v3 Certificate as described in OPC 10000-6. For ECC SecurityPolicies this is an ephemeral key created by the owner of the KeyCredentials. Not specified if no encryption is required. If the securityPolicyUri is provided this field shall be provided. |
|
securityPolicyUri |
The SecurityPolicy used to encrypt the secret. If the certificate is provided this field shall be provided. |
|
requestedRoles |
A list of Roles which should be assigned to the KeyCredential. If not provided the Server chooses suitable defaults. The Server ignores Roles which it does not recognize or if the caller is not authorized to request access to the Role. |
|
requestId |
A unique identifier for the request. This identifier shall be passed to the FinishRequest (see 8.5.6). |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_NotFound |
The applicationUri is not known to the GDS. |
|
Bad_ConfigurationError |
The applicationUri is used by multiple records in the GDS. |
|
Bad_CertificateInvalid |
The Certificate is invalid. |
|
Bad_SecurityPolicyRejected |
The SecurityPolicy is unrecognized or not allowed or does not match the Certificate. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_SecurityModeInsufficient |
The SecureChannel is not encrypted. |
Table 86 specifies the AddressSpace representation for the StartRequest Method.
Table 86 – StartRequest Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:StartRequest |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
FinishRequest is used to retrieve a KeyCredential.
If a Certificate was provided in the request then the KeyCredential secret is encrypted using an asymmetric encryption algorithm specified by the SecurityPolicyUri provided in the request.
The credentialId is the identifier, such as a user name, which often needs to be presented when using the credentialSecret.
The credentialSecret is a UA Binary encoded form of one of the EncryptedSecret DataTypes defined in OPC 10000-4. If the securityPolicyUri requires an RSA Certificate then the RsaEncryptedSecret DataType is used. If the securityPolicyUri requires an ECC Certificate then the EccEncryptedSecret DataType is used.
The Signing Certificate is owned by the source of the KeyCredential. The KeyCredentialService determines the most appropriate Certificate to use.
If the return code is Bad_RequestNotComplete then the request has not been processed and the Client should call again. It is expected that a Client will periodically call this Method until the KeyCredentialService has completed the request.
This Method shall be called from an encrypted SecureChannel and from a Client that has access to the KeyCredentialAdmin Role, the ApplicationAdmin Privilege, or the ApplicationSelfAdmin Privilege (see 8.2). In addition, this Method shall only be called SecureChannel using that same Certificate that Client used to call StartRequest.
Signature
FinishRequest (
[in] NodeId requestId
[in] Boolean cancelRequest
[out] String credentialId
[out] ByteString credentialSecret
[out] String certificateThumbprint
[out] String securityPolicyUri
[out] NodeId[] grantedRoles
);
|
Argument |
Description |
|
requestId |
The identifier returned from a previous call to StartRequest. |
|
cancelRequest |
If TRUE the request is cancelled and no KeyCredentials are returned. If FALSE the normal processing proceeds. |
|
credentialId |
The unique identifier for the KeyCredential. |
|
credentialSecret |
The secret associated with the KeyCredential. |
|
certificateThumbprint |
The thumbprint of the Certificate used to encrypt the secret for RSA SecurityPolicies. Set to NULL for ECC SecurityPolicies. |
|
securityPolicyUri |
The SecurityPolicy used to create the credentialSecret. |
|
|
|
|
grantedRoles |
A list of Roles which have been granted to KeyCredential. If empty then the information is not relevant or not available. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_InvalidArgument |
The requestId is does not reference to a valid request for the Application. |
|
Bad_RequestNotComplete |
The request has not been processed by the Server yet. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_RequestNotAllowed |
The KeyCredential manager rejected the request. The text associated with the error should indicate the exact reason. |
|
Bad_SecurityModeInsufficient |
The SecureChannel is not encrypted. |
Table 87 specifies the AddressSpace representation for the FinishRequest Method.
Table 87 – FinishRequest Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:FinishRequest |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
Revoke is used to revoke a KeyCredential used by a Client or Server.
KeyCredentials shall be deleted when revoked.
This Method shall be called from an encrypted SecureChannel and from a Client that has access to the KeyCredentialAdmin Role, the ApplicationAdmin Privilege, or the ApplicationSelfAdmin Privilege (see 8.2).
Signature
Revoke (
[in] String credentialId
);
|
Argument |
Description |
|
credentialId |
The unique identifier for the KeyCredential. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_InvalidArgument |
The credentialId is does not reference a valid KeyCredential. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_SecurityModeInsufficient |
The SecureChannel is not encrypted. |
Table 88 specifies the AddressSpace representation for the RevokeCredential Method.
Table 88 – Revoke Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:Revoke |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
HasProperty |
Variable |
0:InputArguments |
Argument[] |
0:PropertyType |
Mandatory |
This abstract event is raised when an operation affecting KeyCredentials occur
This Event and it subtypes are security related and Servers shall only report them to users authorized to view security related audit events.
Its representation in the AddressSpace is formally defined in Table 90.
Table 89 – KeyCredentialAuditEventType Definition
|
Attribute |
Value |
||||
|
BrowseName |
0:KeyCredentialAuditEventType |
||||
|
IsAbstract |
True |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
Subtype of the 0:AuditUpdateMethodEventType defined in OPC 10000-5. |
|||||
|
0:HasProperty |
Variable |
ResourceUri |
String |
0:PropertyType |
Mandatory |
|
|
|||||
|
Conformance Units |
|||||
|
GDS Key Credential Service Pull Model |
|||||
This EventType inherits all Properties of the AuditUpdateMethodEventType. Their semantic is defined in OPC 10000-5.
The ResourceUri Property specifies the URI for the resource which accepts the KeyCredential.
This event is raised when a new KeyCredential request has been accepted or rejected by the Server.
This can be the result of a StartRequest Method call.
Its representation in the AddressSpace is formally defined in Table 90.
Table 90 – KeyCredentialRequestedAuditEventType Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:KeyCredentialRequestedAuditEventType |
||||
|
IsAbstract |
False |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
Subtype of the 0:KeyCredentialAuditEventType defined in 8.5.8. |
|||||
|
|
|||||
|
Conformance Units |
|||||
|
GDS Key Credential Service Pull Model |
|||||
This EventType inherits all Properties of the KeyCredentialAuditEventType.
This event is raised when a KeyCredential is delivered by the Server to an application.
This is the result of a FinishRequest Method completing.
Its representation in the AddressSpace is formally defined in Table 91.
Table 91 – KeyCredentialDeliveredAuditEventType Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:KeyCredentialDeliveredAuditEventType |
||||
|
IsAbstract |
False |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
Subtype of the 0:KeyCredentialAuditEventType defined in 8.5.8. |
|||||
|
|
|||||
|
Conformance Units |
|||||
|
GDS Key Credential Service Pull Model |
|||||
This EventType inherits all Properties of the KeyCredentialAuditEventType.
This event is raised when a KeyCredential is revoked.
This is the result of a RevokeKeyCredential Method completing.
Its representation in the AddressSpace is formally defined in Table 92.
Table 92 – KeyCredentialRevokedAuditEventType Definition
|
Attribute |
Value |
|||||
|
BrowseName |
2:KeyCredentialRevokedAuditEventType |
|||||
|
IsAbstract |
False |
|||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
|
Subtype of the 0:KeyCredentialAuditEventType defined in 8.5.8. |
||||||
|
|
||||||
|
Conformance Units |
||||||
|
GDS Key Credential Service Pull Model |
||||||
This EventType inherits all Properties of the KeyCredentialAuditEventType.
The AddressSpace used for PushManagement is shown in Figure 26. Clients interact with the Nodes defined in this model when they need update the KeyCredentials used by a Server to access resources such as Brokers or Authorization Servers. The KeyCredentialConfiguration Folder is a well-known Object that appears in the AddressSpace of any Server which supports KeyCredential management.
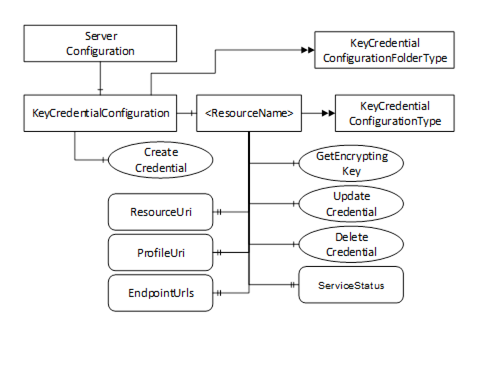
Figure 26 – The Address Space used for Push KeyCredential Management
This ObjectType is the TypeDefinition for an Folder Object that contains the KeyCredentialConfiguration Objects which may be accessed via the Server.
Table 93 – KeyCredentialConfigurationFolderType Definition
|
Attribute |
Value |
|||
|
BrowseName |
0:KeyCredentialConfigurationFolderType |
|||
|
IsAbstract |
False |
|||
|
References |
NodeClass |
BrowseName |
TypeDefinition |
Modelling Rule |
|
Subtype of the 0:FolderType defined in OPC 10000-5. |
||||
|
0:HasComponent |
Object |
0:<ServiceName> |
0:KeyCredentialConfigurationType |
Optional Placeholder |
|
0:HasComponent |
Method |
0:CreateCredential |
Defined in 8.6.3. |
Optional |
|
|
||||
|
Conformance Units |
||||
|
GDS Key Credential Service Push Model |
||||
CreateCredential is used to add a new KeyCredentialConfiguration Object.
This Method shall be called from an encrypted SecureChannel and from a Client that has access to the SecurityAdmin Role (see 8.2).
Signature
CreateCredential (
[in] String name
[in] String resourceUri
[in] String profileUri
[in] String[] endpointUrls
[out] NodeId credentialNodeId
);
|
Argument |
Description |
|
name |
This the BrowseName of the new Object. |
|
resourceUri |
The resourceUri uniquely identifies the resource that accepts the KeyCredentials. A valid URI shall be provided. |
|
profileUri |
The specified URI assigned in OPC 10000-7 to the protocol used to communicate with the resource identified by the resourceUri. A valid URI shall be provided. |
|
endpointUrls |
The specifies URLs used by the Server to communicate with the resource identified by the resourceUri. Valid URLs shall be provided. |
|
credentialNodeId |
A unique identifier for the new KeyCredentialConfiguration Object Node. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_InvalidArgument |
The resourceUri, profileUri, or one or more endpointUrls are not valid. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_SecurityModeInsufficient |
The SecureChannel is not encrypted. |
Table 94 specifies the AddressSpace representation for the CreateCredential Method.
Table 94 – CreateCredential Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
0:CreateCredential |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
Argument[] |
0:PropertyType |
Mandatory |
This Object is an instance of FolderType. It contains The Objects which may be accessed via the Server. It is the target of an HasComponent reference from the ServerConfiguration Object defined in 7.10.3. It is defined in Table 95.
Table 95 – KeyCredentialConfiguration Object Definition
|
Attribute |
Value |
||||
|
BrowseName |
0:KeyCredentialConfiguration |
||||
|
TypeDefinition |
0:KeyCredentialConfigurationFolderType defined in 8.6.2. |
||||
|
References |
NodeClass |
BrowseName |
TypeDefinition |
|
Modelling Rule |
|
|
|||||
|
Conformance Units |
|||||
|
GDS Key Credential Service Push Model |
|||||
This ObjectType is the TypeDefinition for an Object that allows the configuration of KeyCredentials used by the Server. It also includes basic status information which report problems accessing the resource that might be related to bad KeyCredentials. It is defined in Table 96.
Table 96 – KeyCredentialConfigurationType Definition
|
Attribute |
Value |
||||
|
BrowseName |
0:KeyCredentialConfigurationType |
||||
|
IsAbstract |
False |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
Subtype of the BaseObjectType defined in OPC 10000-5. |
|||||
|
0:HasProperty |
Variable |
0:ResourceUri |
0:String |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:ProfileUri |
0:String |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:EndpointUrls |
0:String[] |
0:PropertyType |
Optional |
|
0:HasProperty |
Variable |
0:CredentialId |
0:String |
0:PropertyType |
Optional |
|
0:HasProperty |
Variable |
0:ServiceStatus |
0:StatusCode |
0:PropertyType |
Optional |
|
0:HasComponent |
Method |
0:GetEncryptingKey |
|
Defined in 8.6.6. |
Optional |
|
0:HasComponent |
Method |
0:UpdateCredential |
|
Defined in 8.6.7. |
Optional |
|
0:HasComponent |
Method |
0:DeleteCredential |
|
Defined in 8.6.8. |
Optional |
|
|
|||||
|
Conformance Units |
|||||
|
GDS Key Credential Service Push Model |
|||||
The ResourceUri Property uniquely identifies the resource that accepts the KeyCredentials.
The ProfileUri Property specifies the protocol used to access the resource.
The EndpointUrls Property specifies the URLs that the Server uses to access the resource.
The CredentialId Property is the identifier, such as a user name, which often needs to be presented when using the credentialSecret.
The ServiceStatus Property indicates the result of the last attempt to communicate with the resource. The following common error values are defined:
|
ServiceStatus |
Description |
|
Bad_OutOfService |
Communication was not attempted by the Server because Enabled is FALSE. |
|
Bad_IdentityTokenRejected |
Communication failed because the KeyCredentials are not valid. |
|
Bad_NoCommunication |
Communication failed because the endpoint is not reachable. Where possible a more specific error code should be used. See OPC 10000-4 for a complete list of standard StatusCodes. |
The GetEncryptingKey Method is used request a Public Key that can be used to encrypt the KeyCredentials.
The UpdateKeyCredential Method is used to change the KeyCredentials used by the Server.
The DeleteKeyCredential Method is used to delete the KeyCredentials stored by the Server.
GetEncryptingKey is used to request a key that can be used to encrypt a KeyCredential.
This Method shall be called from an encrypted SecureChannel and from a Client that has access to the SecurityAdmin Role (see 8.2).
Signature
GetEncryptingKey(
[in] String credentialId
[in] String requestedSecurityPolicyUri
[out] ByteString publicKey
[out] String revisedSecurityPolicyUri
);
|
Argument |
Description |
|
credentialId |
The unique identifier associated with the KeyCredential. |
|
requestedSecurityPolicyUri |
The SecurityPolicy used to encrypt the secret. If not specified the Server chooses a suitable default. |
|
publicKey |
The Public Key used to encrypt the secret. The format depends on the SecurityPolicyUri. |
|
revisedSecurityPolicyUri |
The SecurityPolicy used to encrypt the secret. It also specifies the contents of the publicKey. This may be different from the requestedSecurityPolicyUri. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_InvalidArgument |
The credentialId is not valid. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_SecurityModeInsufficient |
The SecureChannel is not encrypted. |
Table 97 specifies the AddressSpace representation for the GetEncryptingKey Method.
Table 97 – GetEncryptingKey Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
0:GetEncryptingKey |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
UpdateCredential is used to update a KeyCredential used by a Server.
The KeyCredential secret may be encrypted using the key returned by GetEncryptingKey. The SecurityPolicyUri species the algorithm used for encryption. The format of the encrypted data is described in 8.5.6.
This Method shall be called from an encrypted SecureChannel and from a Client that has access to the SecurityAdmin Role (see 8.2).
Signature
UpdateCredential(
[in] String credentialId
[in] ByteString credentialSecret
[in] String certificateThumbprint
[in] String securityPolicyUri
);
|
Argument |
Description |
|
credentialId |
The credentialId is the identifier, such as a user name, which often needs to be presented when using the credentialSecret. |
|
credentialSecret |
The secret associated with the KeyCredential. |
|
certificateThumbprint |
The thumbprint of the Certificate used to encrypt the secret. For RSA SecurityPolicies this shall be one of the Application Instance Certificates assigned to the Server. For ECC SecurityPolicies this field is not specified.Not specified if the secret is not encrypted. |
|
securityPolicyUri |
The SecurityPolicy used to encrypt the secret. If not specified the secret is not encrypted. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_InvalidArgument |
The credentialId or credentialSecret is not valid. |
|
Bad_CertificateInvalid |
The Certificate is invalid or it is not one of the Server’s Certificates. |
|
Bad_SecurityPolicyRejected |
The SecurityPolicy is unrecognized or not allowed. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_SecurityModeInsufficient |
The SecureChannel is not encrypted. |
Table 99 specifies the AddressSpace representation for the UpdateKeyCredential Method.
Table 98 – UpdateCredential Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
0:UpdateCredential |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
DeleteCredential is used to delete a KeyCredential used by a Server.
This Method shall be called from an encrypted SecureChannel and from a Client that has access to the SecurityAdmin Role (see 8.2).
Signature
DeleteCredential();
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_SecurityModeInsufficient |
The SecureChannel is not encrypted. |
Table 98 specifies the AddressSpace representation for the DeleteKeyCredential Method.
Table 99 – DeleteCredential Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
0:DeleteCredential |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
This event is raised when a KeyCredential is updated.
This Event and its subtypes report sensitive security related information. Servers shall only report these Events to Clients which are authorized to view such information.
This is the result of a UpdateCredential Method completing.
Its representation in the AddressSpace is formally defined in Table 100.
Table 100 – KeyCredentialUpdatedAuditEventType Definition
|
Attribute |
Value |
||||
|
BrowseName |
0:KeyCredentialUpdatedAuditEventType |
||||
|
IsAbstract |
False |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
Subtype of the 0:KeyCredentialAuditEventType defined in 8.5.8. |
|||||
|
|
|||||
|
Conformance Units |
|||||
|
Push Model for KeyCredential Service |
|||||
This EventType inherits all Properties of the KeyCredentialAuditEventType.
This event is raised when a KeyCredential is updated.
This is the result of a DeleteCredential Method completing.
Its representation in the AddressSpace is formally defined in Table 101.
Table 101 – KeyCredentialDeletedAuditEventType Definition
|
Attribute |
Value |
||||
|
BrowseName |
0:KeyCredentialDeletedAuditEventType |
||||
|
IsAbstract |
False |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
Subtype of the 0:KeyCredentialAuditEventType defined in 8.5.8. |
|||||
|
|
|||||
|
Conformance Units |
|||||
|
GDS Key Credential Service Push Model |
|||||
This EventType inherits all Properties of the KeyCredentialAuditEventType.