Push management is performed by using a KeyCredentialConfiguration Object (see 8.6.5) which is a component of the KeyCredentialConfigurationFolder Object which, in turn, is component of the ServerConfiguration Object in a Server. The interactions between the Administration application and the KeyCredentialService during PushManagement are illustrated in Figure 24.
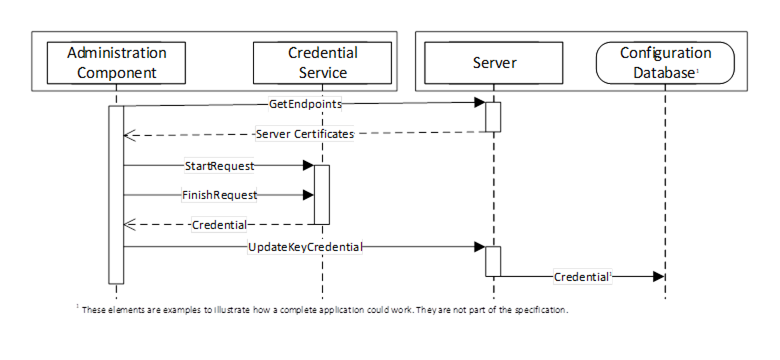
Figure 24 – The Push Model for KeyCredential Management
The Administration Component may use internal APIs to manage KeyCredentials or it could be a standalone utility that uses OPC UA to communicate with a Server which supports the pull model (see 8.3). The Configuration Database is used by the Server to persist its configuration information. The administration and database components are examples to illustrate how an application could be built and are not a requirement.
To ensure security of the KeyCredentials, the KeyCredentialService component can require that secrets be encrypted with a key only known to the intended recipient of the KeyCredentials. For this reason, the Administration Component uses the GetEndpoints Service to read the Certificate from the Server before initiating the credential request on behalf of the Server.
Security, when using the PushManagement model, requires an encrypted channel and Clients with acccess to the SecurityAdmin Role.