Push management is targeted at Server applications and relies on Methods defined in 7.7 to get a Certificate Request which can be passed onto the CertificateManager. After the CertificateManager signs the Certificate the new Certificate is pushed to the Server with the UpdateCertificate Method.
The interactions between a Server Application and CertificateManager during Push Management are illustrated in Figure 13.
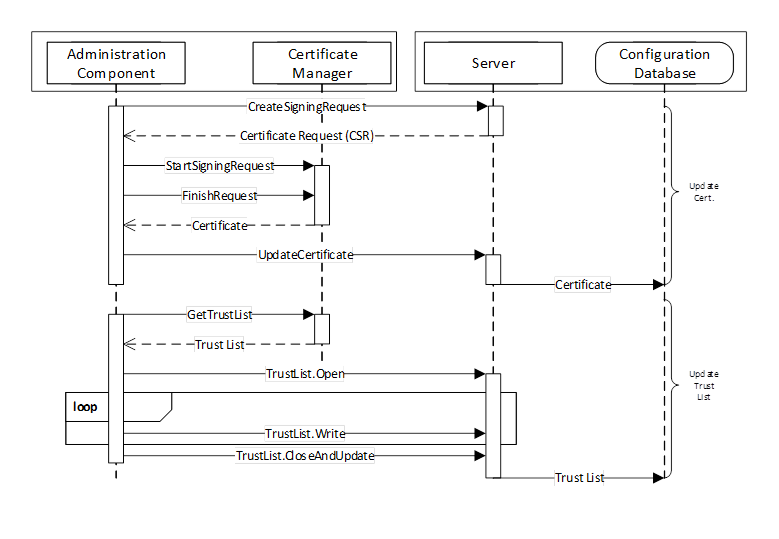
Figure 13 – The Push Certificate Management Model
The Administration Component may be part of the CertificateManager or a standalone utility that uses OPC UA to communicate with the CertificateManager (see 7.2 for a more complete description of the interactions required for this use case). The Configuration Database is used by the Server to persist its configuration information. The RegisterApplication Method (or internal equivalent) is assumed to have been called before the sequence in the diagram starts.
A similar process is used to renew certificates or to periodically update Trust List.
Security when using the Push Management Model requires an encrypted channel and the use of Administrator credentials for the Server that ensure only authorized users can update Certificates or Trust Lists. In addition, separate Administrator credentials are required for the CertificateManager that ensure only authorized users can register new Servers and request new Certificates.