Authorization Services provide Access Tokens to Clients that may use them to access resources. A Server, such as a GDS, with Authorization Service capabilities may support one or more AuthorizationService Objects (see 9.5.2) which may represent an internal Authorization Service or be an API to an external Authorization Service. The Authorization Service is best used in conjunction with the Role model defined in OPC 10000-5. In this scenario, the mapping rules assigned to the Roles known to the Server are used to populate an Access Token with the Roles associated with the UserIdentity provided when the Client submits the request. This scenario is illustrated in Figure 20.
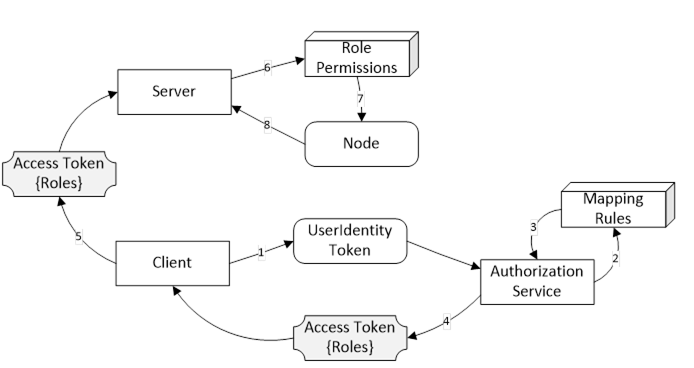
Figure 20 – Roles and Authorization Services
When requesting Access Tokens from an AuthorizationService Object there are three primary use cases based on where the UserIdentityToken comes from: Implicit, Explicit and Chained. These use cases are discussed below. The Implicit and Explicit use cases are implementations of the ‘Indirect’ model for Authorization Services described in OPC 10000-4. The Chained use case is an implementation of the ‘Direct’ model.