If a Server supports Push Management it is required to support an information model as part of its address space. It shall support the ServerConfiguration Object shown in Figure 15. This Object shall only be visible and accessible to administrators and/or the GDS.
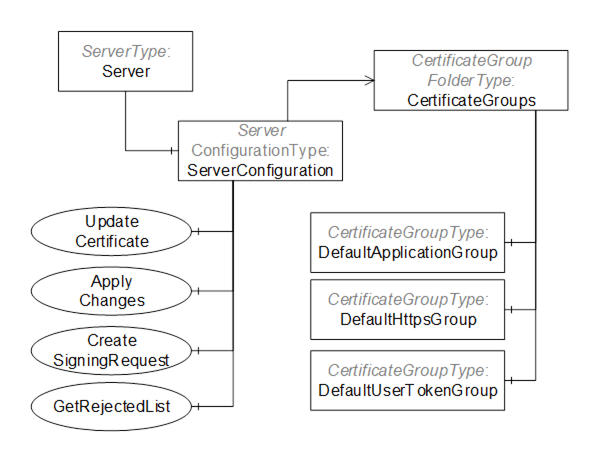
Figure 15 – The AddressSpace for the Server that supports Push Management
All access to Methods defined on the ServerConfiguration Object shall be over an encrypted channel. In addition, Servers should have user credentials with administrator privileges.
This Object allows access to the Server’s configuration and it is the target of an HasComponent reference from the Server Object defined in OPC 10000-5.
This Object and its immediate children shall be visible (i.e. browse access is available) to users who can access the Server Object. The children of the CertificateGroups Object should only be visible to authorized administrators.
Its representation in the AddressSpace is formally defined in Table 39.
Table 39 – ServerConfiguration Object Definition
|
Attribute |
Value |
||||
|
BrowseName |
ServerConfiguration |
||||
|
Namespace |
CORE (see 3.3) |
||||
|
TypeDefinition |
ServerConfigurationType defined in 7.7.3. |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
This type defines an ObjectType which represents the configuration of a Server which supports Push Management . Its values are defined in Table 40. There is always exactly one instance in the Server AddressSpace.
Table 40 – ServerConfigurationType Definition
|
Attribute |
Value |
||||
|
BrowseName |
ServerConfigurationType |
||||
|
Namespace |
CORE (see 3.3) |
||||
|
IsAbstract |
False |
||||
|
References |
NodeClass |
BrowseName |
DataType |
Type Definition |
Modelling Rule |
|
Subtype of the BaseObjectType defined in OPC 10000-5. |
|||||
|
|
|
|
|
|
|
|
HasComponent |
Object |
CertificateGroups |
|
CertificateGroup FolderType |
Mandatory |
|
HasProperty |
Variable |
ServerCapabilities |
String[] |
PropertyType |
Mandatory |
|
HasProperty |
Variable |
SupportedPrivateKeyFormats |
String[] |
PropertyType |
Mandatory |
|
HasProperty |
Variable |
MaxTrustListSize |
UInt32 |
PropertyType |
Mandatory |
|
HasProperty |
Variable |
MulticastDnsEnabled |
Boolean |
PropertyType |
Mandatory |
|
HasComponent |
Method |
UpdateCertificate |
See 7.7.4 |
Mandatory |
|
|
HasComponent |
Method |
ApplyChanges |
See 7.7.5. |
Mandatory |
|
|
HasComponent |
Method |
CreateSigningRequest |
See 7.7.6. |
Mandatory |
|
|
HasComponent |
Method |
GetRejectedList |
See 7.7.7. |
Mandatory |
|
The CertificateGroups Object organizes the Certificate Groups supported by the Server. It is described in 7.5.17. Servers shall support the DefaultApplicationGroup and may support the DefaultHttpsGroup or the DefaultUserTokenGroup. Servers may support additional Certificate Groups depending on their requirements. For example, a Server with two network interfaces should have a different Trust List for each interface. The second Trust List would be represented as a new CertificateGroupType Object organized by CertificateGroups Folder.
The ServerCapabilities Property specifies the capabilities from Annex D which the Server supports. The value is the same as the value reported to the LocalDiscoveryServer when the Server calls the RegisterServer2 Service.
The SupportedPrivateKeyFormats specifies the PrivateKey formats supported by the Server. Possible values include “PEM” (see RFC 5958) or “PFX” (see PKCS #12). The array is empty if the Server does not allow external Clients to update the PrivateKey.
The MaxTrustListSize is the maximum size of the Trust List in bytes. 0 means no limit. The default is 65 535 bytes.
If MulticastDnsEnabled is TRUE then the Server announces itself using multicast DNS. It can be changed by writing to the Variable.
The GetRejectedList Method returns the list of Certificates which have been rejected by the Server. It can be used to track activity or allow administrators to move a rejected Certificate into the Trust List.
The UpdateCertificate Method is used to update a Certificate.
The ApplyChanges Method is used to apply any security related changes if the Server sets the applyChangesRequired flag when another Method is called. Servers should minimize the impact of applying the new configuration, however, it could require that all existing Sessions be closed and re-opened by the Clients.
The CreateSigningRequest Method asks the Server to create a PKCS #10 encoded Certificate Request that is signed with the Server’s private key.
UpdateCertificate is used to update a Certificate for a Server.
There are the following three use cases for this Method:
- The new Certificate was created based on a signing request created with the Method CreateSigningRequest defined in 7.7.6. In this case there is no privateKey provided.
- A new privateKey and Certificate was created outside the Server and both are updated with this Method.
- A new Certificate was created and signed with the information from the old Certificate. In this case there is no privateKey provided.
The Server shall do all normal integrity checks on the Certificate and all of the issuer Certificates. If errors occur the Bad_SecurityChecksFailed error is returned.
The Server shall report an error if the public key does not match the existing Certificate and the privateKey was not provided.
If the Server returns applyChangesRequired =FALSE then it is indicating that it is able to satisfy the requirements specified for the ApplyChanges Method.
This Method requires an encrypted channel and that the Client provides credentials with administrative rights on the Server.
Signature
UpdateCertificate(
[in] NodeId certificateGroupId
[in] NodeId certificateTypeId
[in] ByteString certificate
[in] ByteString[] issuerCertificates
[in] String privateKeyFormat
[in] ByteString privateKey
[out] Boolean applyChangesRequired
);
|
Argument |
Description |
|
certificateGroupId |
The NodeId of the Certificate Group Object which is affected by the update. If null the DefaultApplicationGroup is used. |
|
certificateTypeId |
The type of Certificate being updated. The set of permitted types is specified by the CertificateTypes Property belonging to the Certificate Group. |
|
certificate |
The DER encoded Certificate which replaces the existing Certificate. |
|
issuerCertificates |
The issuer Certificates needed to verify the signature on the new Certificate. |
|
privateKeyFormat |
The format of the Private Key (PEM or PFX). If the privateKey is not specified the privateKeyFormat is null or empty. |
|
privateKey |
The Private Key encoded in the privateKeyFormat. |
|
applyChangesRequired |
Indicates that the ApplyChanges Method shall be called before the new Certificate will be used. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_InvalidArgument |
The certificateTypeId or certificateGroupId is not valid. |
|
Bad_CertificateInvalid |
The Certificate is invalid or the format is not supported. |
|
Bad_NotSupported |
The PrivateKey is invalid or the format is not supported. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_SecurityChecksFailed |
Some failure occurred verifying the integrity of the Certificate. |
Table 41 specifies the AddressSpace representation for the UpdateCertificate Method.
Table 41 – UpdateCertificate Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
UpdateCertificate |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
HasProperty |
Variable |
InputArguments |
Argument[] |
PropertyType |
Mandatory |
|
HasProperty |
Variable |
OutputArguments |
Argument[] |
PropertyType |
Mandatory |
ApplyChanges is used to tell the Server to apply any security changes.
This Method should only be called if a previous call to a Method that changed the configuration returns applyChangesRequired=true (see 7.7.4).
If the Server Certificate has changed, Secure Channels using the old Certificate will eventually be interrupted. The only leeway the Server has is with the timing. In the best case, the Server can close the TransportConnections for the affected Endpoints and leave any Subscriptions intact. This should appear no different than a network interruption from the perspective of the Client. The Client should be prepared to deal with Certificate changes during its reconnect logic. In the worst case, a full shutdown which affects all connected Clients will be necessary. In the latter case, the Server shall advertise its intent to interrupt connections by setting the SecondsTillShutdown and ShutdownReason Properties in the ServerStatus Variable.
If the Secure Channel being used to call this Method will be affected by the Certificate change then the Server shall introduce a delay long enough to allow the caller to receive a reply.
This Method requires an encrypted channel and that the Client provide credentials with administrative rights on the Server.
Signature
ApplyChanges();
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
Table 42 specifies the AddressSpace representation for the ApplyChanges Method.
Table 42 – ApplyChanges Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
ApplyChanges |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
CreateSigningRequest Method asks the Server to create a PKCS #10 DER encoded Certificate Request that is signed with the Server’s private key. This request can be then used to request a Certificate from a CA that expects requests in this format.
This Method requires an encrypted channel and that the Client provide credentials with administrative rights on the Server.
Signature
CreateSigningRequest(
[in]NodeId certificateGroupId,
[in]NodeId certificateTypeId,
[in]String subjectName,
[in]Boolean regeneratePrivateKey,
[in]ByteString nonce,
[out]ByteString certificateRequest
);
|
Argument |
Description |
|
certificateGroupId |
The NodeId of the Certificate Group Object which is affected by the request. If null the DefaultApplicationGroup is used. |
|
certificateTypeId |
The type of Certificate being requested. The set of permitted types is specified by the CertificateTypes Property belonging to the Certificate Group. |
|
subjectName |
The subject name to use in the Certificate Request. If not specified the SubjectName from the current Certificate is used. The format of the subjectName is defined in 7.6.4. |
|
regeneratePrivateKey |
If TRUE the Server shall create a new Private Key which it stores until the matching signed Certificate is uploaded with the UpdateCertificate Method. Previously created Private Keys may be discarded if UpdateCertificate was not called before calling this method again. If FALSE the Server uses its existing Private Key. |
|
nonce |
Additional entropy which the caller shall provide if regeneratePrivateKey is TRUE. It shall be at least 32 bytes long. |
|
certificateRequest |
The PKCS #10 DER encoded Certificate Request. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_InvalidArgument |
The certificateTypeId, certificateGroupId or subjectName is not valid. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
Table 43 specifies the AddressSpace representation for the CreateSigningRequest Method.
Table 43 – CreateSigningRequest Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
CreateSigningRequest |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
HasProperty |
Variable |
InputArguments |
Argument[] |
PropertyType |
Mandatory |
|
HasProperty |
Variable |
OutputArguments |
Argument[] |
PropertyType |
Mandatory |
GetRejectedList Method returns the list of Certificates that have been rejected by the Server.
No rules are defined for how the Server updates this list or how long a Certificate is kept in the list. It is recommended that every valid but untrusted Certificate be added to the rejected list as long as storage is available. Servers should omit older entries from the list returned if the maximum message size is not large enough to allow the entire list to be returned.
This Method requires an encrypted channel and that the Client provides credentials with administrative rights on the Server.
Signature
GetRejectedList(
[out] ByteString[] certificates
);
|
Argument |
Description |
|
certificates |
The DER encoded form of the Certificates rejected by the Server. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
Table 44 specifies the AddressSpace representation for the GetRejectedList Method.
Table 44 – GetRejectedList Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
GetRejectedList |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
HasProperty |
Variable |
OutputArguments |
Argument[] |
PropertyType |
Mandatory |
This event is raised when the Application Certificate is changed.
This is the result of a UpdateCertificate Method completing successfully or failing.
Its representation in the AddressSpace is formally defined in Table 45.
Table 45 – CertificateUpdatedAuditEventType Definition
|
Attribute |
Value |
||||||||||
|
BrowseName |
CertificateUpdatedAuditEventType |
||||||||||
|
Namespace |
CORE (see 3.3) |
||||||||||
|
IsAbstract |
True |
||||||||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
||||||
|
Subtype of the AuditUpdateMethodEventType defined in OPC 10000-5. |
|||||||||||
|
|
|
|
|
|
|
||||||
|
HasProperty |
Variable |
CertificateGroup |
NodeId |
PropertyType |
Mandatory |
||||||
|
HasProperty |
Variable |
CertificateType |
NodeId |
PropertyType |
Mandatory |
||||||
This EventType inherits all Properties of the AuditUpdateMethodEventType. Their semantic is defined in OPC 10000-5.
The CertificateGroup Property specifies the Certificate Group that was affected by the update.
The CertificateType Property specifies the type of Certificate that was updated.