A Network is the logical representation of wired and wireless technologies and represents the communication means for Devices that are connected to it. A Network instance is qualified by its Communication Profile components.
Figure 19 shows the type hierarchy and the NetworkType components. It is formally defined in Table 37.
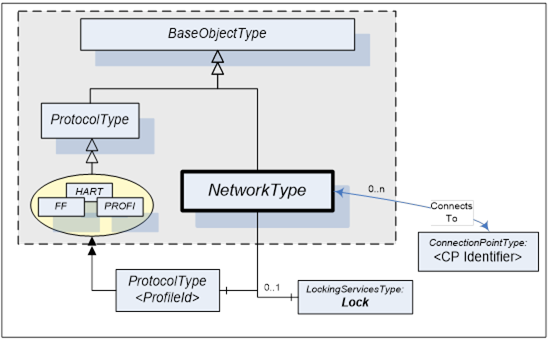
Table 37 – NetworkType definition
|
Attribute |
Value |
||||
|
BrowseName |
NetworkType |
||||
|
IsAbstract |
False |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
Subtype of the BaseObjectType defined in OPC 10000-5. |
|||||
|
HasComponent |
Object |
<ProfileIdentifier> |
|
ProtocolType |
MandatoryPlaceholder |
|
ConnectsTo |
Object |
<CPIdentifier> |
|
ConnectionPointType |
OptionalPlaceholder |
|
HasComponent |
Object |
Lock |
|
LockingServicesType |
Optional |
|
Conformance Units |
|||||
|
DI Network |
|||||
The <ProfileIdentifier> specifies the Protocol and Communication Profile that this Network is used for.
<CPIdentifier> (referenced by a ConnectsTo Reference) references the ConnectionPoint(s) that have been configured for this Network. All ConnectionPoints shall adhere to the same Protocol as the Network. See also Figure 22 for a usage example. They represent the protocol-specific access points for the connected Devices.
In addition, Networks may also support LockingServices (defined in 7).
Clients shall use the LockingServices if they need to make a set of changes (for example, several Write operations and Method invocations) and where a consistent state is available only after all of these changes have been performed. The main purpose of locking a Network is avoiding concurrent topology changes.
The lock on a Network applies to the Network, all connected TopologyElements and their components. If any of the connected TopologyElements provides access to a sub-ordinate Network (like a gateway), the sub-ordinate Network and its connected TopologyElements are locked as well.
If InitLock is requested for a Network, it will be rejected if any of the Devices connected to this Network or any sub-ordinate Network including their connected Devices is already locked.
If the Online/Offline model is supported (see 6.3), the lock always applies to both the online and the offline version.