Errata exists for this version of the document.
All SecurityProtocols shall implement the OpenSecureChannel and CloseSecureChannel services defined in OPC 10000-4. These Services specify how to establish a SecureChannel and how to apply security to Messages exchanged over that SecureChannel. The Messages exchanged and the security algorithms applied to them are shown in Figure 10.
SecurityProtocols shall support three SecurityModes: None, SignOnly and SignAndEncrypt. If the SecurityMode is None then no security is used and the security handshake shown in Figure 10 is not required. However, a SecurityProtocol implementation shall still maintain a logical channel and provide a unique identifier for the SecureChannel.
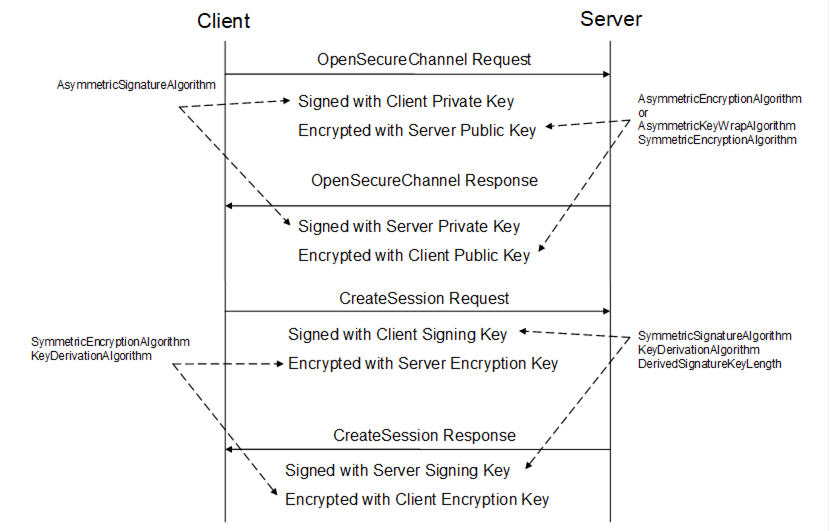
Figure 10 – Security handshake
Each SecurityProtocol mapping specifies exactly how to apply the security algorithms to the Message. A set of security algorithms that shall be used together during a security handshake is called a SecurityPolicy. OPC 10000-7 defines standard SecurityPolicies as parts of the standard Profiles which OPC UA applications are expected to support. OPC 10000-7 also defines a URI for each standard SecurityPolicy.
A Stack is expected to have built in knowledge of the SecurityPolicies that it supports. applications specify the SecurityPolicy they wish to use by passing the URI to the Stack.
Table 35 defines the contents of a SecurityPolicy. Each SecurityProtocol mapping specifies how to use each of the parameters in the SecurityPolicy. A SecurityProtocol mapping may not make use of all of the parameters.
|
Name |
Description |
|
PolicyUri |
The URI assigned to the SecurityPolicy. |
|
SymmetricSignatureAlgorithm |
The symmetric signature algorithm to use. |
|
SymmetricEncryptionAlgorithm |
The symmetric encryption algorithm to use. |
|
AsymmetricSignatureAlgorithm |
The asymmetric signature algorithm to use. |
|
AsymmetricEncryptionAlgorithm |
The asymmetric encryption algorithm to use. |
|
MinAsymmetricKeyLength |
The minimum length, in bits, for an asymmetric key. |
|
MaxAsymmetricKeyLength |
The maximum length, in bits, for an asymmetric key. |
|
KeyDerivationAlgorithm |
The key derivation algorithm to use. |
|
DerivedSignatureKeyLength |
The length in bits of the derived key used for Message authentication. |
|
CertificateSignatureAlgorithm |
The asymmetric signature algorithm used to sign certificates. |
|
SecureChannelNonceLength |
The length, in bytes, of the Nonces exchanged when creating a SecureChannel. |
The KeyDerivationAlgorithm is used to create the keys used to secure Messages sent over the SecureChannel. The length of the keys used for encryption is implied by the SymmetricEncryptionAlgorithm. The length of the keys used for creating Signatures are specified by the DerivedSignatureKeyLength.
The CertificateSignatureAlgorithm is used to sign the Certificates used for asymmetric cryptography. OPC 10000-7 specifies the bit lengths that need to be supported for each SecurityPolicy.
The SecureChannelNonceLength specifies the length of the Nonces exhanged when establishing a SecureChannel (see 6.7.4).