The SessionAuthenticationToken type is an opaque identifier that is used to identify requests associated with a particular Session. This identifier is used in conjunction with the SecureChannelId or Client Certificate to authenticate incoming messages. It is the secret form of the sessionId for internal use in the Client and Server Applications. The SessionAuthenticationToken is a subtype of NodeId.
A Server returns a SessionAuthenticationToken in the CreateSession response. The Client then sends this value with every request which allows the Server to verify that the sender of the request is the same as the sender of the original CreateSession request.
For the purposes of this discussion, a Server consists of application (code) and a Communication Stack as shown in Figure 37. The security provided by the SessionAuthenticationToken depends on a trust relationship between the Server application and the Communication Stack. The Communication Stack shall be able to verify the sender of the message and it uses the SecureChannelId or the Client Certificate to identify the sender to the Server. In these cases, the SessionAuthenticationToken is a NodeId with a UInt32 identifier that allows the Server to distinguish between different Sessions created by the same sender.
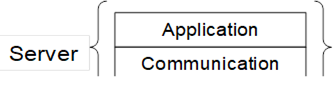
Figure 37 – Logical layers of a Server
In some cases, the application and the Communication Stack cannot exchange information at runtime which means the application will not have access to the SecureChannelId or the Certificate used to create the SecureChannel. In these cases the application shall create a random ByteString value that is at least 32 bytes long. This value shall be kept secret and shall always be exchanged over a SecureChannel with encryption enabled. The Administrator is responsible for ensuring that encryption is enabled. In this cases, the SessionAuthenticationToken is a NodeId with a ByteString identifier. The Profiles in OPC 10000-7 may define additional requirements for a ByteString SessionAuthenticationToken.
Client and Server applications should be written to be independent of the SecureChannel implementation. Therefore, they should always treat the SessionAuthenticationToken as secret information even if it is not required when using some SecureChannel implementations.
Figure 38 illustrates the information exchanged between the Client, the Server and the Server Communication Stack when the Client obtains a SessionAuthenticationToken. In this figure the GetSecureChannelInfo step represents an API that depends on the Communication Stack implementation.
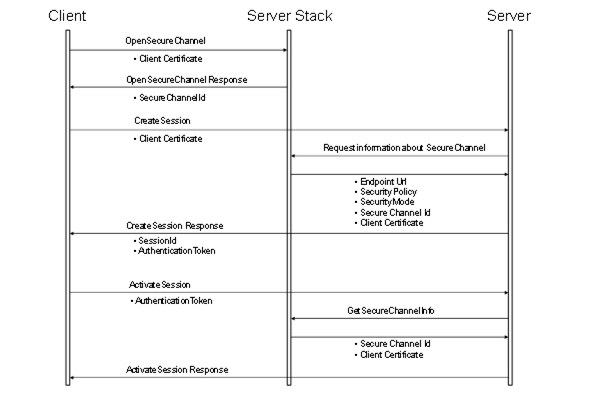
Figure 38 – Obtaining a SessionAuthenticationToken
The SessionAuthenticationToken is a subtype of the NodeId data type; however, it is never used to identify a Node in the AddressSpace. Servers may assign a value to the NamespaceIndex; however, its meaning is Server specific.