All OPC UA Applications require an ApplicationInstanceCertificate which shall contain the following information:
- The network name or address of the computer where the application runs;
- The name of the organization that administers or owns the application;
- The name of the application;
- The URI of the application instance;
- The validFrom and validTo date for the Certificate.
ApplicationInstanceCertificates issued by a Certificate Authority (CA) shall contain the following additional information:
- The name of the Certificate Authority that issued the Certificate;
- The public key issued to the application by the Certificate Authority;
- A digital signature created by the Certificate Authority.
NoteSelf-signed Certificates contain this information but in this case the information is set to itself.
In addition, each ApplicationInstanceCertificate has a private key which should be stored in a location that can only be accessed by the application. If this private key is compromised, the administrator shall force the creation of a new ApplicationInstanceCertificate and private key by the application.
This Certificate may be generated automatically when the application is installed. In this situation the private key assigned to the Certificate shall be used to create the Certificate signature. Certificates created in this way are called self-signed Certificates.
Manual management and replacement before expiry of self-signed Certificates may be appropriate for a few Clients connected to one Server. In complex communication scenarios a central management of Certificates based on a Certificate Authority is recommended. This includes initial roll-out and automatic updates by a CertificateManager defined in OPC 10000-12.
If the administrator responsible for the application decides that a self-signed Certificate does not meet the security requirements of the organization, then the administrator should install a Certificate issued by a Certification Authority. The steps involved in requesting an ApplicationInstanceCertificate from a Certificate Authority are shown in Figure 19.
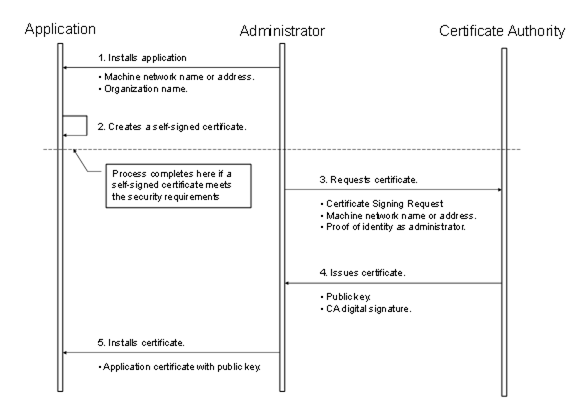
Figure 19 – Obtaining and installing an ApplicationInstanceCertificate
Figure 19 above illustrates the interactions between the application, the Administrator and the Certificate Authority. The application is a OPC UA Application installed on a single machine. The Administrator is the person responsible for managing the machine and the OPC UA Application. The Certificate Authority is an entity that can issue digital Certificates that meet the requirements of the organization deploying the OPC UA Application.
OPC UA defines interfaces and workflows to register OPC UA Applications with a central discovery service and to execute the interaction necessary with a CertificateManager to issue the initial Certificate Authority signed Certificate, The CertificateManager interface includes features to get a TrustList and also Certificate updates from a central place. The Global Discovery Server (GDS) and CertificateManager functionality is defined in OPC 10000-12.
If the Administrator decides that a self-signed Certificate meets the security requirements for the organization, then the Administrator may skip Steps 3 through 5. Application vendors shall ensure that a Certificate is available after the installation process. Every OPC UA Application shall allow the Administrators to replace ApplicationInstanceCertificates with Certificates that meet their requirements.
When the Administrator requests a new Certificate from a Certificate Authority, the Certificate Authority may require that the Administrator provide proof of authorization to request Certificates for the organization that will own the Certificate. The exact mechanism used to provide this proof depends on the Certificate Authority.
Vendors should automate the process of acquiring Certificates from an authority using the CertificateManager defined in OPC 10000-12. If this is the case, the Administrator would still go through the steps illustrated in Figure 19, however, the installation program for the application would do them automatically and only prompt the Administrator to provide information about the application instance being installed.