OPC UA provides standard approach for implementing role based security. Servers could choose to implement none, part or all of mechanisms defined in OPC 10000-5 and in OPC 10000-18. The OPC UA approach assigns Permissions to Roles illustrated in Figure 6. Clients are then granted Roles based on connection information (Session creation). Roles could be restricted by User Authentication, Application Authentication, SecurityModes, or Transports. The assignment of Roles and restrictions is application specific, but they can be assigned to all Nodes in a Namespace or to specific Nodes.
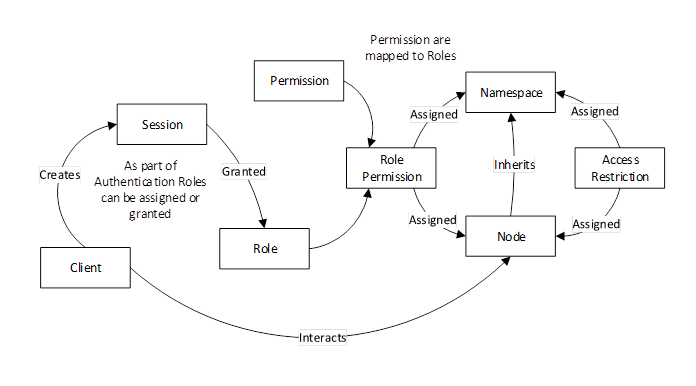
OPC UA defines a set of standard roles that OPC UA Applications can use, these include SecurityAdmin, ConfigureAdmin, Supervisor, Engineer, Operator, Observer and AuthenticatedUser. They are defined in OPC 10000-3 with recommended permissions. The standard roles are also utilized in various other specification as recommended security setting (e.g. see OPC 10000-12). Roles can be assigned via OAuth2 (see 6.12). Role based security is further defined in OPC 10000-18.