OPC UA is a protocol used between components in the operation of an industrial facility at multiple levels: from high-level enterprise management to low-level direct process control of a device. The use of OPC UA for enterprise management involves dealings with customers and suppliers. It could be an attractive target for industrial espionage or sabotage and could also be exposed to threats through untargeted malware, such as worms, circulating on public networks. Disruption of communications at the process control could result in financial losses, affect employee and public safety or cause environmental damage.
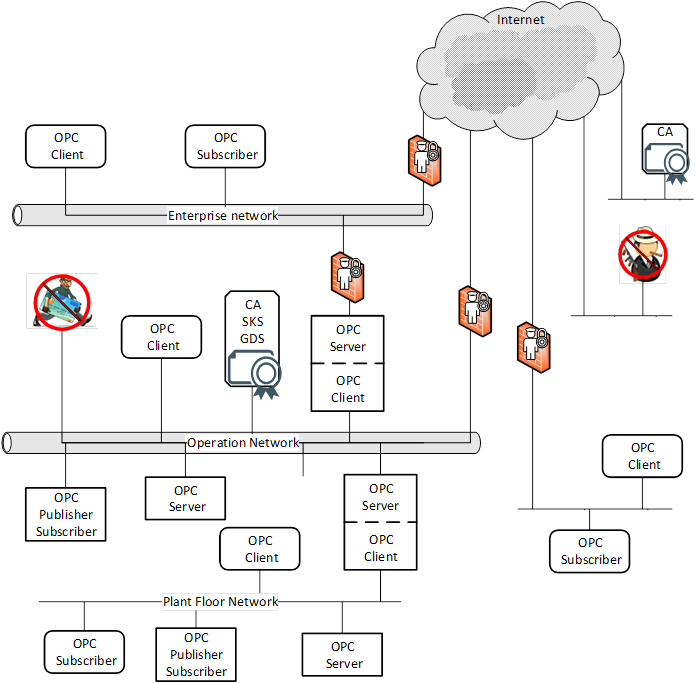
OPC UA will be deployed in a diverse range of operational environments with varying assumptions about threats and accessibility, and with a variety of security policies and enforcement regimes. OPC UA, therefore, provides a flexible set of security mechanisms. Figure 1 is a composite that shows a combination of such environments. Some OPC UA Applications are on the same host and can be easily protected from external attack. Some OPC UA Applications are on different hosts in the same operations network and could be protected by the security boundary protections that separate the operations network from external connections. Some OPC UA Applications run in relatively open environments where users and applications could be difficult to control. Other OPC UA Applications are embedded in control systems that have no direct electronic connection to external systems. OPC UA also supports multiple protocols and communication technologies, that could require different levels of security and different security infrastructure. For example, both Client - Server and Publisher - Subscriber communication is shown in Figure 1. OPC UA also defines global services such as Certificate management, KeyCredential management, AuthorizationService, and GlobalDiscoveryServer (GDS) to help manage security and other global functionality.