In the Client Server communication model the application exposing information consisting of physical and software objects is the OPC UA Server and the application operationg upon this information is the OPC UA Client.
The information provided by an OPC UA Server is organized in the Server Address Space. Services like Read, Write and Browse are available with a request/response pattern used by OPC UA Clients to access information provided by an OPC UA Server.
Every Client creates individual Sessions, Subscriptions and MonitoredItems which are not shared with other Clients. In other words, the data that is published only goes to the Client that created the Subscription.
Sessions are used to manage the communication relationship between Client and Server. MonitoredItems represent the settings used to subscribe to Events and Variable Value data changes from the OPC UA Server Address Space. MonitoredItems are grouped in Subscriptions.
The entities used by OPC UA Clients to subscribe to information from an OPC UA Server are illustrated in Figure B.1.
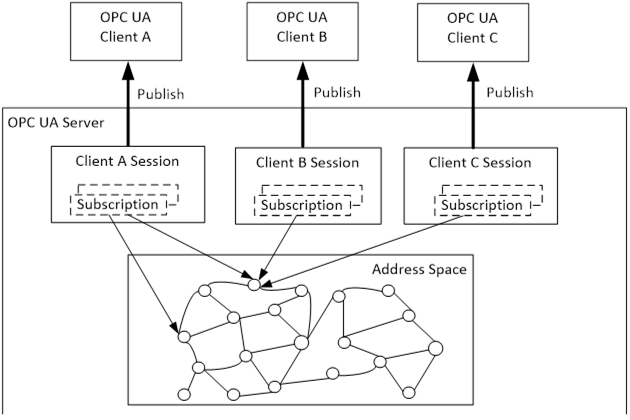
Figure B.1 – Subscriptions in OPC UA Client Server model
In this model the Client is the active entity. It chooses what Nodes of the Server AddressSpace and what Services to use. Subscriptions are created or deleted on the fly. The published data only goes to the Client that created a Subscription.
The Client Server Subscription model provides reliable delivery using buffering, acknowledgements, and retransmissions. This requires resources in the Server for each connected Client.
Resource-constrained Servers limit the number of parallel Client connections, Subscriptions, and MonitoredItems. Similar limitations can also occur in the Client. Clients that continuously need data from a larger number of Servers also consume significant resources.