Errata exists for this version of the document.
The UADP NetworkMessage header and other parts of the NetworkMessage are shown in Figure 27.
When using security, the payload and the Padding field are encrypted and after that, the whole NetworkMessage is signed if signing and encryption is active. The NetworkMessage shall be signed without being encrypted if only the signing is active.
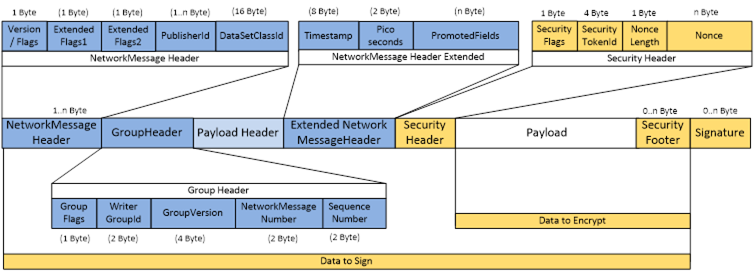
Figure 27 – UADP NetworkMessage
The encoding of the UADP NetworkMessage is specified in Table 73.
The NetworkMessageContentMask setting of the Publisher controls the flags in the fields UADPFlags and ExtendedFlags1. The SecurityMode setting of the Publisher controls the security enabled flag of the ExtendedFlags1. The setting of the flags shall not change until the configuration of the Publisher is changed.
Table 73 – UADP NetworkMessage
|
Name |
Type |
Description |
|
UADPVersion |
Bit[0-3] |
Bit range 0-3: Version of the UADP NetworkMessage. The UADPVersion for this specification version is 1. |
|
UADPFlags |
Bit[4-7] |
Bit 4: PublisherId enabled If the PublisherId is enabled, the type of PublisherId is indicated in the ExtendedFlags1 field. Bit 5: GroupHeader enabled Bit 6: PayloadHeader enabled Bit 7: ExtendedFlags1 enabledThe bit shall be false, if ExtendedFlags1 is 0. |
|
ExtendedFlags1 |
Byte |
The ExtendedFlags1 shall be omitted if bit 7 of the UADPFlags is false. If the field is omitted, the Subscriber shall handle the related bits as false. Bit range 0-2: PublisherId Type 000 The PublisherId is of DataType Byte This is the default value if ExtendedFlags1 is omitted 001 The PublisherId is of DataType UInt16 010 The PublisherId is of DataType UInt32 011 The PublisherId is of DataType UInt64 100 The PublisherId is of DataType String 101 Reserved 11x Reserved 111 Reserved Bit 3: DataSetClassId enabled Bit 4: Security enabled If the SecurityMode is SIGN_1 or SIGNANDENCRYPT_2, this flag is set, message security is enabled and the SecurityHeader is contained in the NetworkMessage header. If this flag is not set, the SecurityHeader is omitted. Bit 5: Timestamp enabled Bit 6: PicoSeconds enabled Bit 7: ExtendedFlags2 enabled The bit shall be false, if ExtendedFlags2 is 0. |
|
ExtendedFlags2 |
Byte |
The ExtendedFlags2 shall be omitted if bit 7 of the ExtendedFlags1 is false. If the field is omitted, the Subscriber shall handle the related bits as false. Bit 0: Chunk message defined in in 7.2.2.2.4. Bit 1: PromotedFields enabled Promoted fields can only be sent if the NetworkMessage contains only one DataSetMessage. Bit range 2-4: UADP NetworkMessage type 000 NetworkMessage with DataSetMessage payload defined in 7.2.2.2.4. If the ExtendedFlags2 field is not provided, this is the default NetworkMessage type. 001 NetworkMessage with discovery request payload defined in 7.2.2.3.4. 010 NetworkMessage with discovery response payload defined in 7.2.2.4.2. 011 Reserved 1xxReserved Bit 5: Reserved Bit 6: Reserved Bit 7: Reserved for further extended flag fields |
|
PublisherId |
Byte[*] |
The PublisherId shall be omitted if bit 4 of the UADPFlags is false. The Id of the Publisher that sent the data. Valid DataTypes are UInteger and String. The DataType is indicated by bits 0-2 of the ExtendedFlags1. A Subscriber can skip NetworkMessages from Publishers it does not expect NetworkMessages from. |
|
DataSetClassId |
Guid |
The DataSetClassId associated with the DataSets in the NetworkMessage. All DataSetMessages in the NetworkMessage shall have the same DataSetClassId. The DataSetClassId shall be omitted if bit 3 of the ExtendedFlags1 is false. |
|
GroupHeader |
|
The group header shall be omitted if bit 5 of the UADPFlags is false. |
|
GroupFlags |
Byte |
Bit 0: WriterGroupId enabled Bit 1: GroupVersion enabled Bit 2: NetworkMessageNumber enabled Bit 3: SequenceNumber enabled Bits 4-6: Reserved Bit 7: Reserved for further extended flag fields |
|
WriterGroupId |
UInt16 |
Unique id for the WriterGroup in the Publisher. A Subscriber can skip NetworkMessages from WriterGroups it does not expect NetworkMessages from. This field shall be omitted if bit 0 of the GroupFlags is false. |
|
GroupVersion |
VersionTime |
Version of the header and payload layout configuration of the NetworkMessages sent for the group. This field shall be omitted if bit 1 of the GroupFlags is false. |
|
NetworkMessage Number |
UInt16 |
Unique number of a NetworkMessage across the combination of PublisherId and WriterGroupId within one PublishingInterval. The number is needed if the DataSetMessages for one group are split into more than one NetworkMessage in a PublishingInterval. The value 0 is invalid. This field shall be omitted if bit 2 of the GroupFlags is false. |
|
SequenceNumber |
UInt16 |
Sequence number for the NetworkMessage. This field shall be omitted if bit 3 of the GroupFlags is false. |
|
PayloadHeader |
Byte [*] |
The payload header depends on the UADP NetworkMessage Type flags defined in the ExtendedFlags2 bit range 0-3. The default is DataSetMessage if the ExtendedFlags2 field is not enabled. The PayloadHeader shall be omitted if bit 6 of the UADPFlags is false. The PayloadHeader is not contained in the payload but it is contained in the unencrypted NetworkMessage header since it contains information necessary to filter DataSetMessages on the Subscriber side. |
|
Timestamp |
DateTime |
The time the NetworkMessage was created. The Timestamp shall be omitted if bit 5 of ExtendedFlags1 is false. The PublishingInterval, the SamplingOffset the PublishingOffset and the Timestamp and PicoSeconds in the NetworkMessage header shall use the same time base. |
|
PicoSeconds |
UInt16 |
Specifies the number of 10 picoseconds (1,0 e-11 seconds) intervals which shall be added to the Timestamp. The PicoSeconds shall be omitted if bit 6 of ExtendedFlags1 is false. |
|
PromotedFields |
|
The PromotedFields shall be omitted if bit 4 of the ExtendedFlags2 is false. If the PromotedFields are provided, the number of DataSetMessages in the Network Message shall be one. |
|
Size |
UInt16 |
Total size in Bytes of the Fields contained in the PromotedFields. |
|
Fields |
BaseDataType[ ] |
Array of promoted fields. The size, order and DataTypes of the fields depend on the settings in the FieldMetaData of the DataSetMetaData associated with the DataSetMessage contained in the NetworkMessage. |
|
SecurityHeader |
|
The security header shall be omitted if bit 4 of the ExtendedFlags1 is false. |
|
SecurityFlags |
Byte |
Bit 0: NetworkMessage Signed Bit 1: NetworkMessage Encrypted Bit 2: SecurityFooter enabled Bit 3: Force key reset This bit is set if all keys will be made invalid. It is set until the new key is used. The publisher must give subscribers a reasonable time to request new keys. The minimum time is five times the KeepAliveTime configured for the corresponding PubSub group. This flag is typically set if all keys are invalidated to exclude Subscribers, that no longer have access to the keys. Bit range 4-7: Reserved |
|
SecurityTokenId |
IntegerId |
The ID of the security token that identifies the security key in a SecurityGroup. The relation to the SecurityGroup is done through DataSetWriterIds contained in the NetworkMessage. |
|
NonceLength |
Byte |
The length of the Nonce used to initialize the encryption algorithm. |
|
MessageNonce |
Byte [NonceLength] |
A number used exactly once for a given security key. For a given security key a unique nonce shall be generated for every NetworkMessage. The rules for constructing the MessageNonce are defined for the UADP Message Security in 7.2.2.2.3. |
|
SecurityFooterSize |
UInt16 |
The size of the SecurityFooter. The security footer size shall be omitted if bit 2 of the SecurityFlags is false. |
|
Payload |
Byte [*] |
The payload depends on the UADP NetworkMessage Type flags defined in the ExtendedFlags2 bit range 2-5. |
|
SecurityFooter |
Byte [*] |
Optional security footer shall be omitted if bit 2 of the SecurityFlags is false. The content of the security footer is defined by the SecurityPolicy. |
|
Signature |
Byte [*] |
The signature of the NetworkMessage. |
The algorithm and nonce length used of the UADP NetworkMessage security depend on the selected SecurityPolicy. They are defined by SymmetricPubSubEncryptionAlgorithm and SymmetricPubSubNonceLength.
The keys used to encrypt and sign messages are returned from the GetSecurityKeys method (see 8.4). This Method returns a sequence of random data with a length that depends on the SecurityPolicyUri, which is also returned by the Method. The layout of the random data is defined in Table 74.
Table 74 – Layout of the key data for UADP message security
|
Name |
Type |
Description |
|
SigningKey |
Byte [SymmetricSignatureAlgorithm Key Length] |
Signing key part of the key data returned from GetSecurityKeys. The SymmetricSignatureAlgorithm is defined in the SecurityPolicy. |
|
EncryptingKey |
Byte [SymmetricEncryptionAlgorithm KeyLength] |
Encryption key part of the key data returned from GetSecurityKeys. The SymmetricEncryptionAlgorithm is defined in the SecurityPolicy. |
|
KeyNonce |
Byte [SymmetricPubSubNonceLength] |
Nonce part of the key data returned from GetSecurityKeys. |
The layout of the MessageNonce for AES-CTR mode is defined in Table 75.
Table 75 – Layout of the MessageNonce for AES-CTR
|
Name |
Type |
Description |
|
Random |
Byte [4] |
The random part of the MessageNonce. This number does not need to be a cryptographically random number, it can be pseudo-random. |
|
SequenceNumber |
UInt32 |
A strictly monotonically increasing sequence number assigned by the publisher to each NetworkMessage sent for a SecurityTokenId and PublisherId combination. The sequence number is reset to 1 after the key and SecurityTokenId are updated in the Publisher. A receiver should ignore older NetworkMessages than the last sequence processed if it does not handle reordering of NetworkMessages. Receivers need to be aware of sequence numbers roll over (change from 4294967295 to 0). To determine whether a received NetworkMessages is newer than the last processed NetworkMessages the following formula shall be used: (4294967295 + received sequence number – last processed sequence number) modulo 4294967296. Results below 1073741824 indicate that the received NetworkMessages is newer than the last processed NetworkMessages and the received NetworkMessages is processed. Results above 3221225472 indicate that the received message is older (or same) than the last processed NetworkMessages and the received NetworkMessages should be ignored if reordering of NetworkMessages is not necessary. Other results are invalid and the NetworkMessages shall be ignored. The key lifetime should be selected in a way that a new key is used before a rollover for the SequenceNumber happens. Subscribers shall reset the records they keep for sequence numbers if they do not receive messages for two times the keep alive time to deal with Publishers that are out of service and were not able to continue from the last used SequenceNumber. |
The message encryption and decryption with AES-CTR mode uses a secret and a counter block. The secret is the EncryptingKey from the key data defined in Table 74. The layout and content of the counter block is defined in Table 76.
Table 76 – Layout of the counter block for UADP message security
|
Name |
Type |
Description |
|
KeyNonce |
Byte [4] |
The KeyNonce portion of the key data returned from GetSecurityKeys. |
|
MessageNonce |
Byte [8] |
The first 8 bytes of the Nonce in the SecurityHeader of the NetworkMessage. For AES-CTR mode the length of the SecurityHeader Nonce shall be 8 Bytes. |
|
BlockCounter |
Byte [4] |
The counter for each encrypted block of the NetworkMessage. The counter is a 32-bit big endian integer (the opposite of the normal encoding for UInt32 values in OPC UA. This convention comes from the AES-CTR RFC). The counter starts with 0 at the first block. The counter is incremented by 1 for each block. |
AES-CTR mode takes the counter block and encrypts it using the encrypting key. The encrypted key stream is then logically XORed with the data to encrypt or decrypt. The process is repeated for each block in the plain text. No padding is added to the end of the plain text. AES-CTR does not change the size of the plain text data and can be applied directly to a memory buffer containing the message.
The signature is calculated on the entire NetworkMessage including any encrypted data. The signature algorithm is specified by the SecurityPolicyUri in OPC 10000-7.
When a Subscriber receives a NetworkMessage, it shall verify the signature first. If verification fails, it drops the NetworkMessage.
Other SecurityPolicy may specify different key lengths or cryptography algorithms.
If a NetworkMessage payload like a DataSetMessage or a discovery response message has to be split across multiple NetworkMessages the chunks are sent with the payload header defined in Table 77 and the payload defined in Table 78. A chunk NetworkMessage can only contain chunked payload of one DataSetMessage.
Table 77 – Chunked NetworkMessage Payload Header
|
Name |
Type |
Description |
|
DataSetWriterId |
UInt16 |
DataSetWriterId contained in the NetworkMessage. The DataSetWriterId identifies the PublishedDataSet and the DataSetWriter responsible for sending Messages for the DataSet. A Subscriber can skip DataSetMessages from DataSetWriters it does not expect DataSetMessages from. The DataSetWriterId shall be set to 0 for discovery response messages. |
Table 78 – Chunked NetworkMessage Payload Fields
|
Name |
Type |
Description |
|
MessageSequenceNumber |
UInt16 |
Sequence number of the payload as defined for the NetworkMessage type like DataSetMessageSequenceNumber in a DataSetMessage. NetworkMessages may be received out of order. In this case, a chunk for the next payload can be received before the last chunk of the previous payload was received. If the next sequence number is received by a Subscribers that can handle only one payload, the chunks of the previous payload are skipped if they are not completely received yet. |
|
ChunkOffset |
UInt32 |
The byte offset position of the chunk in the complete NetworkMessage payload. The last chunk is received if ChunkOffset plus the size of the current chunk equals TotalSize. The reassembled NetworkMessage payload can be processed after all chunks are received. |
|
TotalSize |
UInt32 |
Total size of the NetworkMessage payload in bytes. |
|
ChunkData |
ByteString |
The pieces of the original DataSetMessage, are copied into the chunk until the maximum size allowed for a single NetworkMessage is reached minus space for the signature. The data copied into next chunk starts with the byte after the last byte copied into current chunk. A DataSetMessage is completely received when all chunks are received and the DataSetMessage can be processed completely. |