Figure 13 illustrates the use of TrustAnchor capabilities integrated in the Push Management process (See OPC 10000-21).
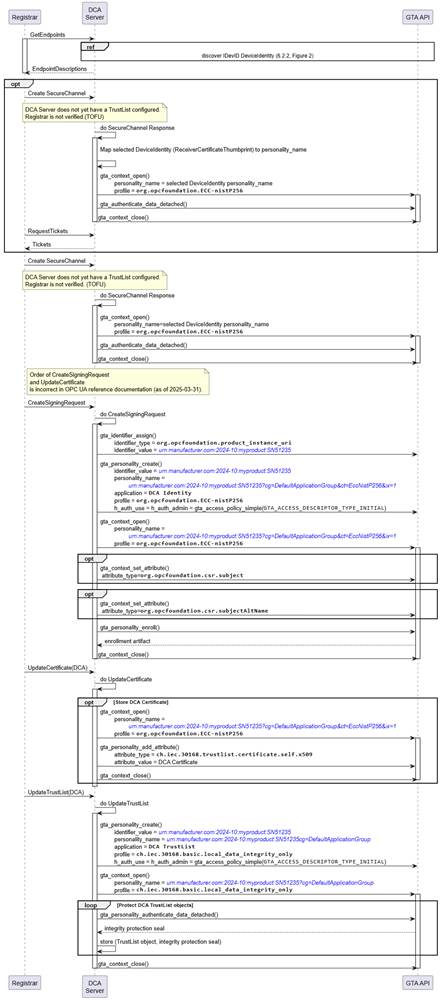
Figure 13 – Onboarding of Device Configuration Application (Push Management)
In response to a GetEndpoints request received from the registrar the DCA server compiles a list of DeviceIdentity(s) that are eligible for onboarding (see 5.2.2). The DCA server needs to maintain a mapping between DeviceIdentity certificates and the corresponding DeviceIdentity personality. The list of EndpointDescriptions created from the available DeviceIdentity certificates is returned to the Registar.
The Registrar selects one DeviceIdentity and starts a create SecureChannel Request. Details for establishing a SecureChannel are explained in 5.5. The DeviceIdentity selected by the Registrar is indicated by the ReceiverCertificateThumbprint contained in the security header (See OPC 10000-6).
The subsequent actions of the DCA server towards the GTA API correspond to Pull Management.
- The sequence following on CreateSigningRequest (Push) corresponds to the sequence used to prepare StartSigningRequest (Pull).
- The sequence following on UpdateCertificate (Push) corresponds to the sequence following the response to StartSigningRequest (Pull)
- The sequence following on UpdateTrustList (Push) corresponds to the sequence following the response to GetTrustList (Pull)