Figure 2 gives an overview of the GTA API information model. The starting point for objects organized by the GTA API information model are identifiers (cf. ISO/IEC TS 30168 clause 5.5.3). An identifier is used to identify a device or application in a specific security context. For example, with OPC UA an ApplicationUri is a suitable identifier.
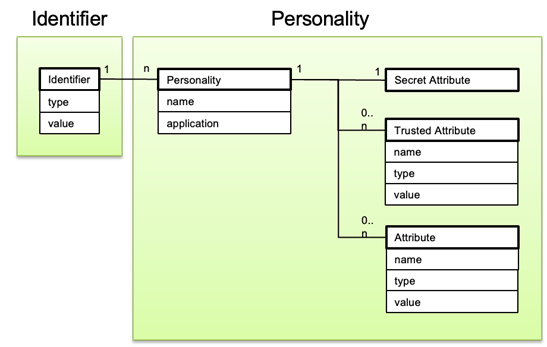
Figure 2 – GTA API personality object model
Personalities are means that allow to present the device or application identity associated to an identifier in the digital world. A personality comprises all security objects which are needed to act in a given security context. The different security objects are represented as attributes of the personality:
- Secret Attributes: These are objects which are typically used to proof the identity and authenticity of an entity or to access data which shall only be exposed to a designated entity. The SecureElement provides capabilities to protect the integrity, authenticity, and confidentiality of these objects. Examples are, private keys for asymmetric crypto, secret keys, and passcodes. In case of OPC UA this corresponds to an RSA or ECC private key (depending on the SecurityPolicy).
- Trusted Attributes: These are objects which are typically used to proof the identity and authenticity of another entity. The SecureElement provides capabilities to protect the integrity and authenticity of these objects. Examples are, trusted public keys, trusted certificates, passcode verifiers.
- Attributes: These are additional objects which can be managed by GTA API to provide a single point of information for objects belonging to the security context. These attributes can also be used to enable organization and discovery of personalities. However, these attributes do not depend on the security capabilities of the SecureElement. Examples are end entity and intermediate certificates, application specific information like labels or URIs.