Errata exists for this version of the document.
Once an OPC UA Client has established a SecureChannel with a Server it can create an OPC UA Session.
The steps involved in establishing a Session are shown in Figure 22.
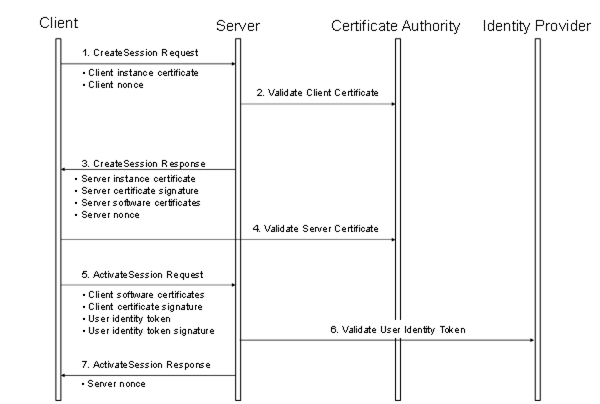
Figure 22 – Establishing a Session
Figure 22 above illustrates the interactions between a Client, a Server, a Certificate Authority (CA) and an identity provider. The CA is responsible for issuing the Application Instance Certificates. If the Client or Server does not have online access to the CA, then they shall validate the Application Instance Certificates using the CA public key that the administrator shall install on the local machine.
The identity provider may be a central database that can verify that user token provided by the Client. This identity provider may also tell the Server which access rights the user has. The identity provider depends on the user identity token. It could be a Certificate Authority, a Kerberos ticket granting service, a WS-Trust Server or a proprietary database of some sort.
The Client and Server shall prove possession of their Application Instance Certificates by signing the Certificates with a nonce appended. The exact mechanism used to create the proof of possession signatures is described in 5.6.2. Similarly, the Client shall prove possession by either providing a secret like a password in the user identity token or by creating a signature with the secret associated with a user identity token like x.509 v3.