Errata exists for this version of the document.
In systems with multiple Servers and Clients the installation of Public Keys in Trust Lists can very quickly become cumbersome. In these instances, the use of a company specific CA can greatly simplify the installation/configuration issues. The CA can also provide additional benefits such as management of Certificate expiration and Certificate Revocation Lists (CRL). Figure 10 provides an illustration of this activity.
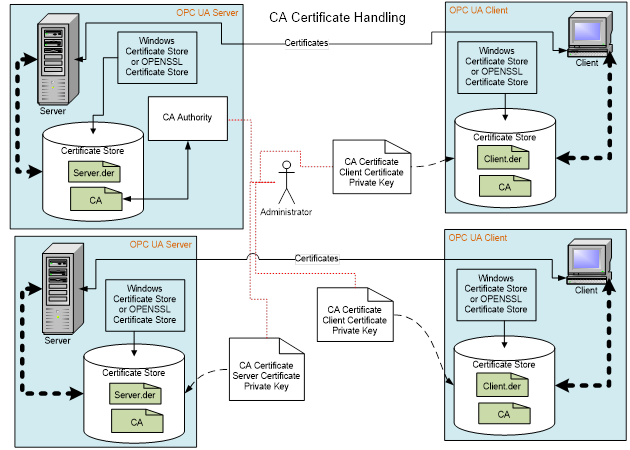
Figure 10 - CA Certificate handling
The administrator will need to generate a CA signed Application Instance Certificate for all Clients and Servers that are installed in a system, but he will only need to install the CA Public Key on all machines. When a Certificate expires and is replaced, the administrator will only need to replace the expired Certificate (Public Keys and Private Keys), there will be no need to copy a Public Key to any locations.
The company specific CA allows the company to control the issuing of Certificates. The use of a commercial CA (such as VeriSign) would not be recommended in most cases. An OPC UA Application typically is configured to trust only the other applications determined by the Company as trusted. If all Certificates issued by a commercial CA were to be trusted then the commercial CA would be controlling which applications are to be trusted, not the company.
Certificate management needs to be addressed by all application developers. Some applications may make use of Certificate management that is provided as part of a system wide infrastructure, others will generate self-signed Certificates as part of an installation. See OPC 10000-12 for additional details on system wide infrastructures for Certificate management.