The GlobalDiscoveryServer AddressSpace used for Certificate management is shown in Figure 20. Most of the interactions between the GlobalDiscoveryServer and Application administrator or the Client will be via Methods defined on the Directory folder.
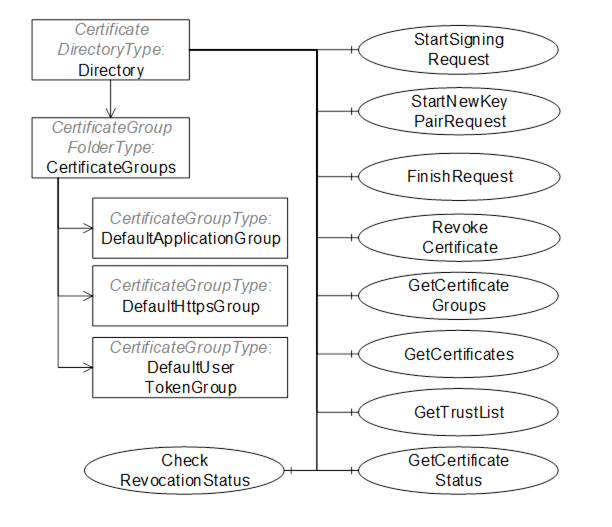
Figure 20 – The Certificate Management AddressSpace for the GlobalDiscoveryServer
This ObjectType is the TypeDefinition for the root of the CertificateManager AddressSpace. It provides additional Methods for Certificate management which are shown in Table 51.
Table 51 – CertificateDirectoryType ObjectType Definition
|
Attribute |
Value |
|||||
|
BrowseName |
2:CertificateDirectoryType |
|||||
|
IsAbstract |
False |
|||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
|
Subtype of the 2:DirectoryType defined in 6.6.3. |
||||||
|
|
|
|
|
|
|
|
|
0:Organizes |
Object |
2:CertificateGroups |
|
0:CertificateGroup FolderType |
Mandatory |
|
|
0:HasComponent |
Method |
2:StartSigningRequest |
Defined in 7.9.3. |
Mandatory |
||
|
0:HasComponent |
Method |
2:StartNewKeyPairRequest |
Defined in 7.9.4. |
Mandatory |
||
|
0:HasComponent |
Method |
2:FinishRequest |
Defined in 7.9.5. |
Mandatory |
||
|
0:HasComponent |
Method |
2:RevokeCertificate |
Defined in 7.9.6. |
Optional |
||
|
0:HasComponent |
Method |
2:GetCertificateGroups |
Defined in 7.9.7. |
Mandatory |
||
|
0:HasComponent |
Method |
2:GetCertificates |
Defined in 7.9.8. |
Optional |
||
|
0:HasComponent |
Method |
2:GetTrustList |
Defined in 7.9.9. |
Mandatory |
||
|
0:HasComponent |
Method |
2:GetCertificateStatus |
Defined in 7.9.10. |
Mandatory |
||
|
0:HasComponent |
Method |
2:CheckRevocationStatus |
Defined in 7.9.11. |
Optional |
||
|
|
||||||
|
Conformance Units |
||||||
|
GDS Certificate Manager Pull Model |
||||||
The CertificateGroups Object organizes the CertificateGroups supported by the CertificateManager. It is described in 7.8.4.6. CertificateManagers shall support the DefaultApplicationGroup and may support the DefaultHttpsGroup or the DefaultUserTokenGroup. CertificateManagers may support additional CertificateGroups depending on their requirements. For example, a CertificateManager with multiple Certificate Authorities would represent each as a CertificateGroupType Object organized by CertificateGroups Folder. Clients could then request Certificates issued by a specific CA by passing the appropriate NodeId to the StartSigningRequest or StartNewKeyPairRequest Methods.
CertificateGroups assigned by the CertificateManager to specific applications are persisted by PullManagement Clients. These Clients use the NodeIds to relate their local configuration to the CertificateGroup in the CertificateManager.
The StartSigningRequest Method is used to request a new a Certificate that is signed by a CA managed by the CertificateManager. This Method is recommended when the caller already has a private key.
The StartNewKeyPairRequest Method is used to request a new Certificate that is signed by a CA managed by the CertificateManager along with a new private key. This Method is used only when the caller does not have a private key and cannot generate one.
The FinishRequest Method is used to check that a Certificate request has been approved by an entity with access to the RegistrationAuthorityAdmin Role. If successful the Certificate and Private Key (if requested) are returned.
The GetCertificateGroups Method returns a list of NodeIds for CertificateGroupType Objects that can be used to request Certificates or Trust Lists for an Application.
The GetCertificates Method returns a list of Certificates assigned to the Application for a CertificateGroup.
The GetTrustList Method returns a NodeId of a TrustListType Object that belongs to a CertificateGroup assigned to an Application.
The GetCertificateStatus Method checks whether the Application needs to update the Certificate identified in the call.
The CheckRevocationStatus Method checks the revocation status of a Certificate.
StartSigningRequest is used to initiate a request to create a Certificate which uses the private key which the caller currently has. The new Certificate is returned in the FinishRequest response.
Signature
StartSigningRequest(
[in] NodeId applicationId
[in] NodeId certificateGroupId
[in] NodeId certificateTypeId
[in] ByteString certificateRequest
[out] NodeId requestId
);
|
Argument |
Description |
|
applicationId |
The identifier assigned to the Application record by the CertificateManager. |
|
certificateGroupId |
The NodeId of the CertificateGroup which provides the context for the new request. If null the CertificateManager shall choose the DefaultApplicationGroup. |
|
certificateTypeId |
The NodeId of the CertificateType for the new Certificate. If null the CertificateManager shall generate a Certificate based on the value of the certificateGroupId argument. |
|
certificateRequest |
A CertificateRequest used to prove possession of the Private Key. It is a PKCS #10 encoded blob in DER format. If the CertificateRequest is for an ApplicationInstance Certificate then it shall include all fields required by OPC 10000-6 such as the subjectAltName. |
|
requestId |
The NodeId that represents the request. This value is passed to FinishRequest . |
The call returns the NodeId that is passed to the FinishRequest Method.
The certificateGroupId parameter allows the caller to specify a CertificateGroup that provides context for the request. If null the CertificateManager shall choose the DefaultApplicationGroup. If the Application does not currently belong to the requested CertificateGroup the CertificateManager shall verify that the Application is allowed to join the CertificateGroup and then, if permitted, add the Application to the CertificateGroup. The CertificateGroup verification and assignment may occur anytime before FinishRequest returns success.
The set of available CertificateGroups are found in the CertificateGroups folder described in 7.9.2. The CertificateGroups allowed for an Application are returned by the GetCertificateGroups Method (see 7.9.7).
The certificateTypeId parameter specifies the type of Certificate to return. The permitted values are specified by the CertificateTypes Property of the Object specified by the certificateGroupId parameter.
The certificateRequest parameter is a DER encoded CertificateRequest. The subject, subjectAltName and Public Key are copied into the new Certificate.
If the certificateTypeId is a subtype of ApplicationCertificateType the subject conforms to the requirements defined in OPC 10000-6. The public key length shall meet the length restrictions for the CertificateType. If the certificateType is a subtype of HttpsCertificateType the Certificate common name (CN=) shall be the same as a domain from a DiscoveryUrl which uses HTTPS and the subject shall have an organization (O=) field.
The ApplicationUri shall be specified in the CSR. The CertificateManager shall return Bad_CertificateUriInvalid if the stored ApplicationUri for the Application is different from what is in the CSR.
The subject in the CSR may be ignored by the CertificateManager. The CertificateManager may update the subject to comply with policy requirements and to ensure global uniqueness.
Any bits set in basicConstraints or extendedKeyUsage fields in the CSR are ignored by the CertificateManager. The CertificateManager uses values that are appropriate and compliant with the specification.
For Servers, the list of domain names shall be specified in the CSR. The domains shall include the domain(s) in the DiscoveryUrls known to the CertificateManager.
This Method shall be called from an encrypted SecureChannel and from a Session that has access to the CertificateAuthorityAdmin Role, the ApplicationAdmin Privilege, or the ApplicationSelfAdmin Privilege (see 7.2).
If auditing is supported, the CertificateManager shall generate the CertificateRequested AuditEventType (see 7.9.12) if this Method succeeds or fails.
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_NotFound |
The applicationId does not refer to a registered Application. |
|
Bad_InvalidArgument |
One or more of the certificateGroupId, certificateTypeId or certificateRequest arguments is not valid. The text associated with the error shall indicate the exact problem. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_RequestNotAllowed |
The current configuration of the CertificateManager does not allow the request. The text associated with the error should indicate the exact reason. |
|
Bad_CertificateUriInvalid |
The ApplicationUri was not specified in the CSR or does not match the Application record. |
|
Bad_NotSupported |
The signing algorithm, public algorithm or public key size are not supported by the CertificateManager. The text associated with the error shall indicate the exact problem. |
Table 52 specifies the AddressSpace representation for the StartSigningRequest Method.
Table 52 – StartSigningRequest Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:StartSigningRequest |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
This Method is used to start a request for a new Certificate and Private Key. The Certificate and Private Key. are returned in the FinishRequest response.
Signature
StartNewKeyPairRequest(
[in] NodeId applicationId
[in] NodeId certificateGroupId
[in] NodeId certificateTypeId
[in] String subjectName
[in] String[] domainNames
[in] String privateKeyFormat
[in] String privateKeyPassword
[out] NodeId requestId
);
|
Argument |
Description |
|
applicationId |
The identifier assigned to the Application Instance by the CertificateManager. |
|
certificateGroupId |
The NodeId of the CertificateGroup which provides the context for the new request. If null the CertificateManager shall choose the DefaultApplicationGroup. |
|
certificateTypeId |
The NodeId of the CertificateType for the new Certificate. If null the CertificateManager shall generate a Certificate based on the value of the certificateGroupId argument. |
|
subjectName |
The subject to use for the Certificate. If not specified the ApplicationName and/or domainNames are used to create a suitable default value. The format of the subject is a sequence of name value pairs separated by a ‘/’. The name shall be one of ‘CN’, ‘O’, ‘OU’, ‘DC’, ‘L’, ‘S’ or ‘C’ and shall be followed by a ‘=’ and then followed by the value. The value may be any printable character except for ‘”’. If the value contains a ‘/’ or a ‘=’ then it shall be enclosed in double quotes (‘”’). |
|
domainNames |
The domain names to include in the Certificate. If not specified the DiscoveryUrls are used to create suitable defaults. |
|
privateKeyFormat |
The format of the private key. The following values are always supported: PFX- PKCS #12 encoded PEM- PKCS #8 Base64 encoded DER (see RFC 5958). |
|
privateKeyPassword |
The password to use for the private key. |
|
requestId |
The NodeId that represents the request. This value is passed to FinishRequest. |
The call returns the NodeId that is passed to the FinishRequest Method.
The certificateGroupId parameter allows the caller to specify a CertificateGroup that provides context for the request. If null the CertificateManager shall choose the DefaultApplicationGroup. If the Application does not currently belong to the requested CertificateGroup the CertificateManager shall verify that the Application is allowed to join the CertificateGroup and then, if permitted, add the Application to the CertificateGroup.
The set of available CertificateGroups are found in the CertificateGroups folder described in 7.9.2. The CertificateGroups allowed for an Application are returned by the GetCertificateGroups Method (see 7.9.7).
The certificateTypeId parameter specifies the type of Certificate to return. The permitted values are specified by the CertificateTypes Property of the Object specified by the certificateGroupId parameter.
The subjectName parameter is a sequence of X.500 name value pairs separated by a ‘/’. For example: CN=ApplicationName/OU=Group/O=Company.
If the certificateType is a subtype of ApplicationCertificateType the Certificate subject shall have an organization (O=) or domain name (DC=) field. The public key length shall meet the length restrictions for the CertificateType. The domain name field specified in the subject is a logical domain used to qualify the subject that may or may not be the same as a domain or IP address in the subjectAltName field of the Certificate.
If the certificateType is a subtype of HttpsCertificateType the Certificate common name (CN=) shall be the same as a domain from a DiscoveryUrl which uses HTTPS and the subject shall have an organization (O=) field.
If the subjectName is blank or null the CertificateManager generates a suitable default.
The requested subject may be ignored by the CertificateManager. The CertificateManager may update the subject to comply with policy requirements and to ensure global uniqueness.
The domainNames parameter is list of domains to be includes in the Certificate. If it is null or empty the GDS uses the DiscoveryUrls of the Server to create a list. For Clients the domainNames are omitted from the Certificate if they are not explicitly provided.
The privateKeyFormat specifies the format of the private key returned. All CertificateManager implementations shall support “PEM” and “PFX”.
The privateKeyPassword specifies the password on the private key. The CertificateManager shall not persist this information and shall discard it once the new private key is generated.
This Method shall be called from an encrypted SecureChannel and from a Session that has access to the CertificateAuthorityAdmin Role, the ApplicationAdmin Privilege, or the ApplicationSelfAdmin Privilege (see 7.2).
If auditing is supported, the CertificateManager shall generate the CertificateRequested AuditEventType (see 7.9.12) if this Method succeeds or fails.
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_NodeIdUnknown |
The applicationId does not refer to a registered Application (deprecated). |
|
Bad_NotFound |
The applicationId does not refer to a registered Application. |
|
Bad_InvalidArgument |
One or more of the certificateGroupId, certificateTypeId, subjectName, domainNames or privateKeyFormat parameters is not valid. The text associated with the error shall indicate the exact problem. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_RequestNotAllowed |
The current configuration of the CertificateManager does not allow the request. The text associated with the error should indicate the exact reason. |
Table 53 specifies the AddressSpace representation for the StartNewKeyPairRequest Method.
Table 53 – StartNewKeyPairRequest Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:StartNewKeyPairRequest |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
FinishRequest is used to finish a certificate request started with a call to StartNewKeyPairRequest or StartSigningRequest.
Signature
FinishRequest (
[in] NodeId applicationId
[in] NodeId requestId
[out] ByteString certificate
[out] ByteString privateKey
[out] ByteString[] issuerCertificates
);
|
Argument |
Description |
|
applicationId |
The identifier assigned to the Application Instance by the GDS. |
|
requestId |
The NodeId returned by StartNewKeyPairRequest or StartSigningRequest. |
|
certificate |
The DER encoded Certificate. |
|
privateKey |
The private key encoded in the format requested. If a password was supplied the blob is protected with it. This field is null if no private key was requested. |
|
issuerCertificates |
The Certificates required to validate the new Certificate. |
This call is passes the NodeId returned by a previous call to StartNewKeyPairRequest or StartSigningRequest.
It is expected that a Client will periodically call this Method until an entity with access to the RegistrationAuthorityAdmin Role has approved the request.
This Method shall be called from an encrypted SecureChannel and from a Session that has access to the CertificateAuthorityAdmin Role, the ApplicationAdmin Privilege, or the ApplicationSelfAdmin Privilege (see 7.2). In addition, the Client Certificate shall be the same as the one used to call StartSigningRequest or StartNewKeyPairRequest.
If auditing is supported, the GDS shall generate the CertificateDeliveredAuditEventType (see 7.9.13) if this Method succeeds or if it fails with anything but Bad_NothingToDo.
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_NotFound |
The applicationId does not refer to a registered Application. |
|
Bad_InvalidArgument |
The requestId is does not reference to a valid request for the Application. |
|
Bad_NothingToDo |
There is nothing to do because request has not yet completed. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
|
Bad_RequestNotAllowed |
The CertificateManager rejected the request. The text associated with the error should indicate the exact reason. |
Table 54 specifies the AddressSpace representation for the FinishRequest Method.
Table 54 – FinishRequest Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:FinishRequest |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
RevokeCertificate is used to revoke a Certificate issued by the CertificateManager.
When a Certificate is revoked it shall be removed from any TrustLists that it is in and TrustLists with the issuer Certificate shall be updated with the new CRL.
Certificates assigned to an Application are automatically revoked when the UnregisterApplication Method is called (see 6.6.8).
This Method shall be called from an authenticated SecureChannel and from a Client that has access to the CertificateAuthorityAdmin Role (see 7.2).
Signature
RevokeCertificate (
[in] NodeId applicationId
[in] ByteString certificate
);
|
Argument |
Description |
|
applicationId |
The identifier assigned to the Application by the CertificateManager. |
|
certificate |
The DER encoded Certificate to revoke. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_NotFound |
The applicationId does not refer to a registered Application. |
|
Bad_InvalidArgument |
The certificate is not a Certificate for the specified Application that was issued by the CertificateManager. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
Table 55 specifies the AddressSpace representation for the RevokeCertificate Method.
Table 55 – RevokeCertificate Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:RevokeCertificate |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
GetCertificateGroups returns the CertificateGroups assigned to Application.
Signature
GetCertificateGroups(
[in] NodeId applicationId
[out] NodeId[] certificateGroupIds
);
|
Argument |
Description |
|
applicationId |
The identifier assigned to the Application by the GDS. |
|
certificateGroupIds |
An identifier for the CertificateGroups assigned to the Application. |
A CertificateGroup provides a TrustList and one or more CertificateTypes which may be assigned to an Application.
This Method shall be called from an authenticated SecureChannel and from a Client that has access to the CertificateAuthorityAdmin Role, the ApplicationAdmin Privilege, or the ApplicationSelfAdmin Privilege (see 7.2).
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_NotFound |
The applicationId does not refer to a registered Application. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
Table 58 specifies the AddressSpace representation for the GetCertificateGroups Method.
Table 56 – GetCertificateGroups Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:GetCertificateGroups |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
GetCertificates returns the Certificates assigned to Application and associated with the CertificateGroup.
This Method shall be called from an authenticated SecureChannel and from a Client that has access to the CertificateAuthorityAdmin Role, the ApplicationAdmin Privilege, or the ApplicationSelfAdmin Privilege (see 7.2).
Signature
GetCertificates(
[in] NodeId applicationId
[in] NodeId certificateGroupId
[out] NodeId[] certificateTypeIds
[out] ByteString[] certificates
);
|
Argument |
Description |
|
applicationId |
The identifier assigned to the Application by the GDS. |
|
certificateGroupId |
An identifier for the CertificateGroup that the Certificates belong to. If null, the CertificateManager shall return the Certificates for all CertificateGroups assigned to the Application. |
|
certificateTypeIds |
The CertificateTypes that currently have a Certificate assigned. The length of this list is the same as the length as certificates list. |
|
certificates |
A list of DER encoded Certificates assigned to Application. This list only includes Certificates that are currently valid. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_NotFound |
The applicationId does not refer to a registered Application. |
|
Bad_InvalidArgument |
The certificateGroupId is not recognized or not valid for the Application. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
Table 57 specifies the AddressSpace representation for the GetCertificates Method.
Table 57 – GetCertificates Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:GetCertificates |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
GetTrustList is used to retrieve the NodeId of a TrustList assigned to an Application.
Signature
GetTrustList(
[in] NodeId applicationId
[in] NodeId certificateGroupId
[out] NodeId trustListId
);
|
Argument |
Description |
|
applicationId |
The identifier assigned to the Application by the GDS. |
|
certificateGroupId |
An identifier for a CertificateGroup that the Application belongs to. If null, the CertificateManager shall return the trustListId for a suitable default group for the Application. |
|
trustListId |
The NodeId for a TrustList Object that can be used to download the TrustList assigned to the Application. |
Access permissions also apply to the TrustList Objects which are returned by this Method. This TrustList includes any Certificate Revocation Lists (CRLs) associated with issuer Certificates in the Trust List.
This Method shall be called from an authenticated SecureChannel and from a Client that has access to the CertificateAuthorityAdmin Role, the ApplicationAdmin Privilege, or the ApplicationSelfAdmin Privilege (see 7.2).
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_NotFound |
The applicationId does not refer to a registered Application. |
|
Bad_InvalidArgument |
The certificateGroupId parameter is not valid. The text associated with the error shall indicate the exact problem. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
Table 58 specifies the AddressSpace representation for the GetTrustList Method.
Table 58 – GetTrustList Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:GetTrustList |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
GetCertificateStatus is used to check if an Application needs to update its Certificate.
This Method shall be called from an authenticated SecureChannel and from a Client that has access to the CertificateAuthorityAdmin Role, the ApplicationAdmin Privilege, or the ApplicationSelfAdmin Privilege (see 7.2).
Signature
GetCertificateStatus(
[in] NodeId applicationId
[in] NodeId certificateGroupId
[in] NodeId certificateTypeId
[out] Boolean updateRequired
);
|
Argument |
Description |
|
applicationId |
The identifier assigned to the Application Instance by the GDS. |
|
certificateGroupId |
The NodeId of the CertificateGroup which provides the context. If null the CertificateManager shall choose the DefaultApplicationGroup. |
|
certificateTypeId |
The NodeId of the CertificateType for the Certificate. If null the CertificateManager shall select a Certificate based on the value of the certificateGroupId argument. |
|
updateRequired |
TRUE if the Application needs to request a new Certificate from the GDS. FALSE if the Application can keep using the existing Certificate. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_NotFound |
The applicationId does not refer to a registered Application. |
|
Bad_InvalidArgument |
The certificateGroupId or certificateTypeId parameter is not valid. The text associated with the error shall indicate the exact problem. |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
Table 59 specifies the AddressSpace representation for the GetCertificateStatus Method.
Table 59 – GetCertificateStatus Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:GetCertificateStatus |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
CheckRevocationStatus Method is used to check the revocation status of an Certificate.
Clients or Servers may use this Method if the issuer Certificate has a crlDistributionPoint extension, an authorityInformationAccess extension (see RFC 6960) or the TrustList is configured to require online Certificate revocation checks (see 7.8.2.1).
The CertificateManager will typically use a protocol such as OCSP (see RFC 6960) to verify the Certificate status using the endpoint in the CDP extension, however, it may also optimize performance by maintaining a cache of recently verified Certificate and/or maintaining it’s own offline CRLs. The validityTime parameter provides guidance on how long a result can be kept in a local cache.
The caller shall perform all validation checks other than the revocation status check (see OPC 10000-4) on the Certificate before calling this Method. The CertificateManager shall check the Signature on the Certificate and may do additional validation.
This Method shall be called from an authenticated SecureChannel.
Signature
CheckRevocationStatus (
[in] ByteString certificate
[out] StatusCode certificateStatus
[out] UtcTime validityTime
);
|
Argument |
Description |
|
INPUTS |
|
|
certificate |
The DER encoded form of the Certificate to check. |
|
OUTPUTS |
|
|
certificateStatus |
The first error encountered when validating the Certificate. |
|
validityTime |
When the result expires and should be rechecked. DateTime.MinValue is this is unknown. |
Method Result Codes (defined in Call Service)
|
Result Code |
Description |
|
Bad_UserAccessDenied |
The current user does not have the rights required. |
Table 60 specifies the AddressSpace representation for the CheckRevocationStatus Method.
Table 60 – CheckRevocationStatus Method AddressSpace Definition
|
Attribute |
Value |
||||
|
BrowseName |
2:CheckRevocationStatus |
||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
ModellingRule |
|
0:HasProperty |
Variable |
0:InputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
|
0:HasProperty |
Variable |
0:OutputArguments |
0:Argument[] |
0:PropertyType |
Mandatory |
This event is raised when a new certificate request has been accepted or rejected by the CertificateManager.
This can be the result of a StartNewKeyPairRequest or StartSigningRequest Method calls.
Its representation in the AddressSpace is formally defined in Table 61.
Table 61 – CertificateRequestedAuditEventType Definition
|
Attribute |
Value |
|||||
|
BrowseName |
2:CertificateRequestedAuditEventType |
|||||
|
IsAbstract |
True |
|||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
|
Subtype of the 0:AuditUpdateMethodEventType defined in OPC 10000-5. |
||||||
|
0:HasProperty |
Variable |
2:CertificateGroup |
0:NodeId |
0:PropertyType |
Mandatory |
|
|
0:HasProperty |
Variable |
2:CertificateType |
0:NodeId |
0:PropertyType |
Mandatory |
|
|
|
||||||
|
Conformance Units |
||||||
|
GDS Certificate Manager Pull Model |
||||||
This EventType inherits all Properties of the AuditUpdateMethodEventType. Their semantic is defined in OPC 10000-5.
The CertificateGroup Property specifies the CertificateGroup that was affected by the update.
The CertificateType Property specifies the type of Certificate that was updated.
This event is raised when a certificate is delivered by the CertificateManager to a Client.
This is the result of a FinishRequest Method completing successfully.
Its representation in the AddressSpace is formally defined in Table 62.
Table 62 – CertificateDeliveredAuditEventType Definition
|
Attribute |
Value |
|||||
|
BrowseName |
2:CertificateDeliveredAuditEventType |
|||||
|
IsAbstract |
True |
|||||
|
References |
NodeClass |
BrowseName |
DataType |
TypeDefinition |
Modelling Rule |
|
|
Subtype of the 0:AuditUpdateMethodEventType defined in OPC 10000-5. |
||||||
|
0:HasProperty |
Variable |
2:CertificateGroup |
0:NodeId |
0:PropertyType |
Mandatory |
|
|
0:HasProperty |
Variable |
2:CertificateType |
0:NodeId |
0:PropertyType |
Mandatory |
|
|
|
||||||
|
Conformance Units |
||||||
|
GDS Certificate Manager Pull Model |
||||||
This EventType inherits all Properties of the AuditUpdateMethodEventType. Their semantic is defined in OPC 10000-5.
The CertificateGroup Property specifies the CertificateGroup that was affected by the update.
The CertificateType Property specifies the type of Certificate that was updated.